Emergency Response Overview#
When a company experiences a security incident that affects normal business operations, such as a hacker intrusion or system crash, it is crucial to address the situation immediately to restore the company's network information system to normal operation in the shortest time possible. This includes further investigation into the source of the intrusion, reconstructing the incident process, and providing solutions and preventive measures to mitigate or reduce economic losses for the company.
Common classifications of emergency response incidents include:
Web intrusion: website defacement, homepage tampering, Webshell
System intrusion: viruses, Trojans, ransomware, remote control backdoors
Network attacks: DDOS attacks, DNS hijacking, ARP spoofing
Basic Information Gathering#
This section on basic information gathering can be accomplished using Windows built-in commands or tools. This includes gathering system information, network information, process information, user information, and historical traffic information.
System Information Gathering#
There are two methods to obtain relevant system information. The first method is for older versions of the operating system, where you can use winmsd to gather information. The specific operation is as follows:
Start -> Run -> winmsd
Click on Software Environment -> System Drivers to view the currently loaded drivers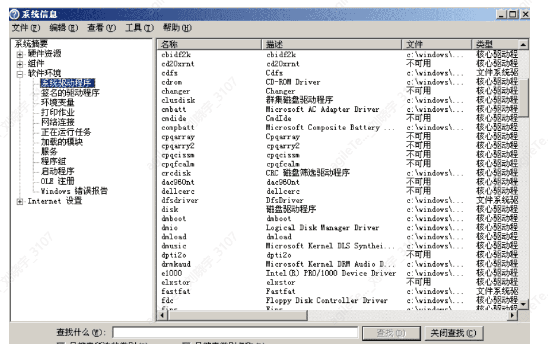
Click on Software Environment -> Running Tasks to view the currently running processes
Click on Software Environment -> Loaded Modules to view the DLL files loaded by the program
However, this functionality has been removed in newer operating systems, such as Windows Server 2008, so the second method is introduced below.
The second method is command line output. We can enter systeminfo in the cmd command line, and we can see the patch information marked in red in the image below. Here we can learn about some potential vulnerabilities in the system.
However, it is clear that the difference from the first method is that it does not list loaded processes, DLL files, drivers, etc., but this information can be obtained through other tools. In Windows Server 2008 and later, Windows introduced the Resource Monitor. There are two ways to open it:
1. Run -> resmon
2. Task Manager -> Performance -> Resource Monitor
This section can search for loaded DLL files based on related exe files.
Network Information Gathering#
In the Windows cmd command line, enter ipconfig to confirm the current IP address allocation of the network card.
Then, you can further confirm the network connection status by entering netstat -ano in the cmd command line to obtain the status of network process connections and check for any suspicious process network connection information.
Various States of netstat#
CLOSED
Initial (no connection) state. -9-
LISTEN
Listening state, waiting for connection requests from remote machines.
SYN_SEND
During the TCP three-way handshake, after the active connecting end sends the SYN packet, it enters the SYN_SEND state, waiting for the ACK packet from the other party.
SYN_RECV
During the TCP three-way handshake, after the active connecting end receives the SYN packet, it enters the SYN_RECV state.
ESTABLISHED
After completing the TCP three-way handshake, the active connecting end enters the ESTABLISHED state. At this point, the TCP connection has been established and communication can occur.
FIN_WAIT_1
During the TCP four-way handshake, after the active closing end sends the FIN packet, it enters the FIN_WAIT_1 state.
FIN_WAIT_2
During the TCP four-way handshake, after the active closing end receives the ACK packet, it enters the FIN_WAIT_2 state.
TIME_WAIT
During the TCP four-way handshake, after the active closing end sends the ACK packet, it enters the TIME_WAIT state, waiting for a maximum of MSL time for the passive closing end to receive the ACK packet.
CLOSING
During the TCP four-way handshake, after the active closing end sends the FIN packet but does not receive the corresponding ACK packet, and instead receives the other party's FIN packet, it enters the CLOSING state.
CLOSE_WAIT
During the TCP four-way handshake, after the passive closing end receives the FIN packet, it enters the CLOSE_WAIT state.
LAST_ACK
During the TCP four-way handshake, after the passive closing end sends the FIN packet, it enters the LAST_ACK state, waiting for the other party's ACK packet.
Summary#
Possible states for the active connecting end include: CLOSED, SYN_SEND, ESTABLISHED
Possible states for the active closing end include: FIN_WAIT_1, FIN_WAIT_2, TIME_WAIT. Possible states for the passive connecting end include: LISTEN, SYN_RECV, ESTABLISHED.
Possible states for the passive closing end include: CLOSE_WAIT, LAST_ACK, CLOSED.
User Information Gathering#
In the Windows cmd command line, enter net user to confirm the user information of the current operating system and check for any suspicious accounts.
Of course, you can continue to the next step by entering net user xx to confirm the group information to which that xx belongs in Windows.
Windows comes with a Resource Monitor that can filter relevant information about the current processes, which is particularly useful in cases of mining or when being used as a botnet for external DOS attacks.
Not available on Windows Server 2003.
Detailed Information Gathering#
Startup Information Collection#
This involves a tool called Autoruns. Since most malware does not have relevant descriptive information, checking the Publisher and Description fields can help exclude some simpler backdoor programs or malicious code: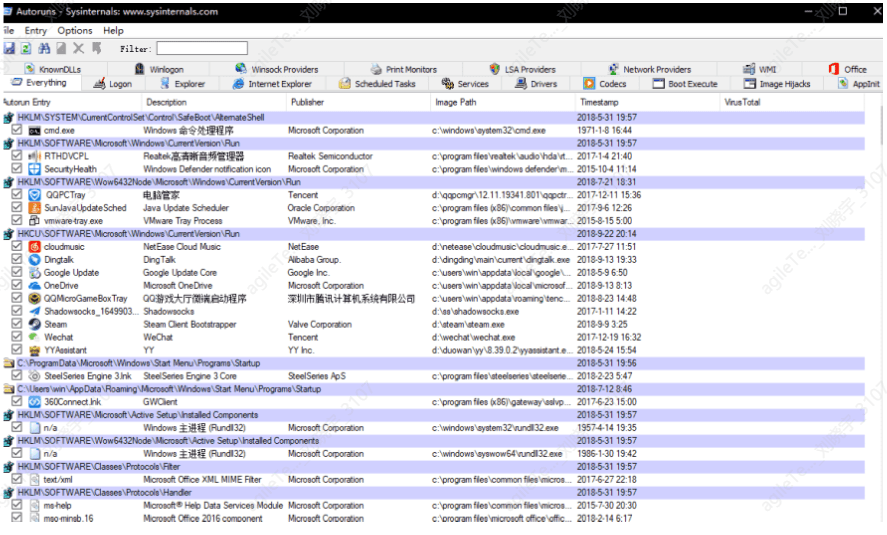
By selecting the Hide Microsoft and Windows Entries option in the Options menu, Autoruns can automatically filter out some safe startup items: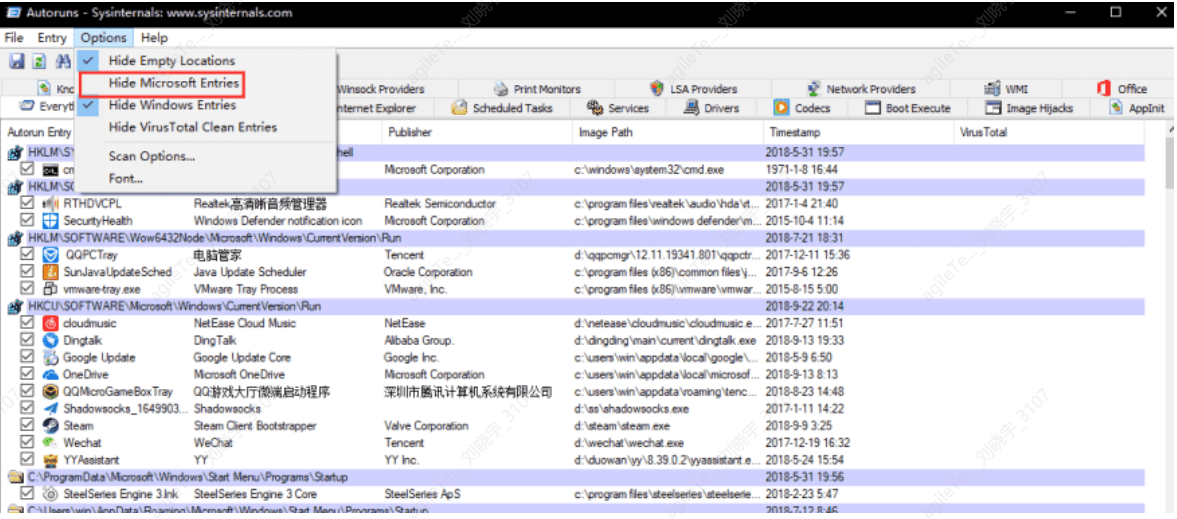
Behavior Information Collection#
Some viruses often seek to access sensitive files, the registry, create modules, and other abnormal behaviors, so we can use auxiliary monitoring software to check the behavior of malicious programs.
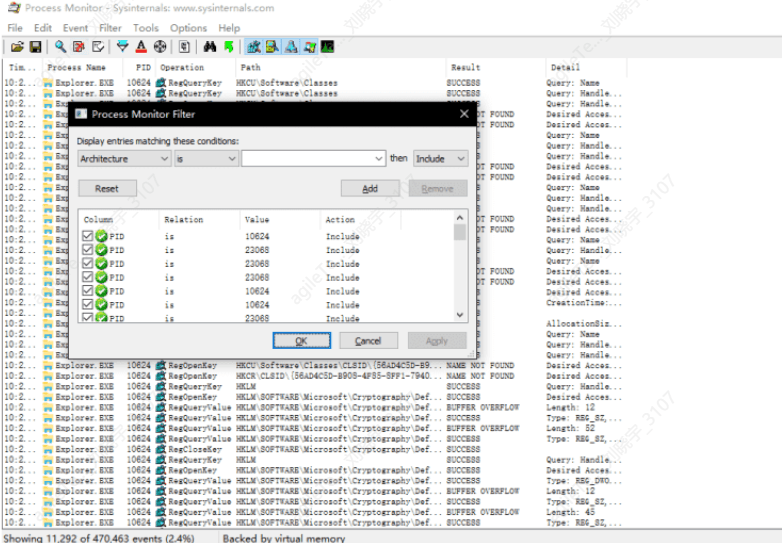
Procmon will display the process's behavior towards files and the results in real-time, as shown in the image below: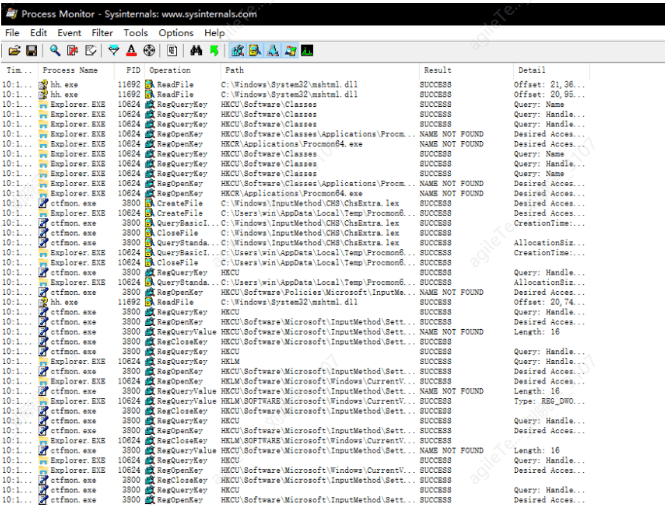
This tool will clearly show what operations the process has performed on certain files. If you need to monitor or filter a specific process, you can press the shortcut key ctrl+L and enter the specified process name to filter the results: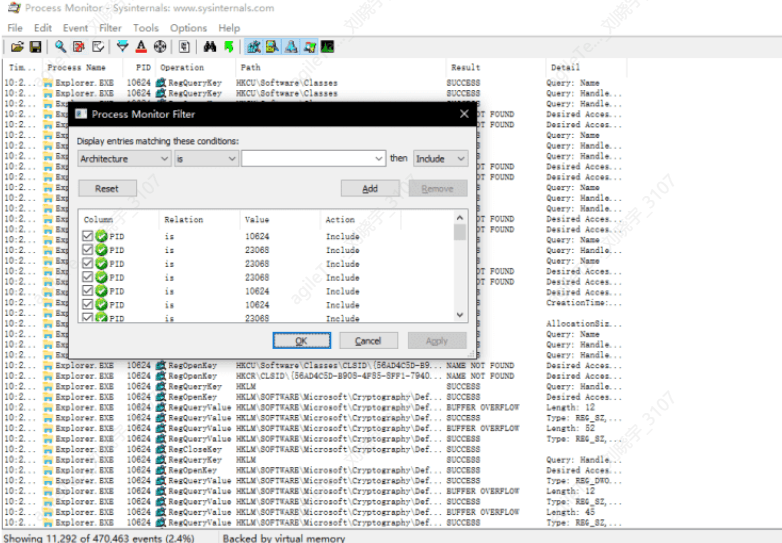
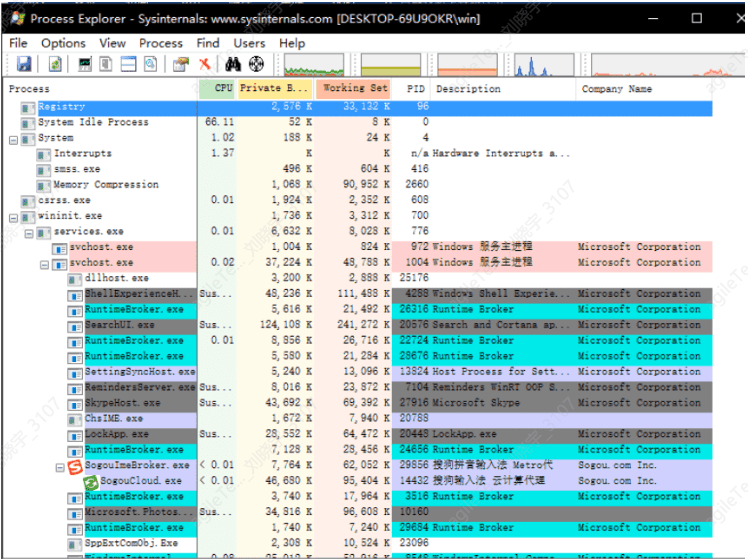
Process Information Collection#
Network Behavior Collection#
TcpView can dynamically display the current network connection status, but this tool has a drawback, as it cannot display UDP traffic.
User Information Collection#
Open the Start menu and enter compmgmt.msc, select "System Tools" - "Local Users and Groups" to view
all local user and group information (including hidden users with usernames ending in $, such as: admin$)
or use LP_Check to check for shadow accounts.
Generally, if a system account has been created and used for operations, even if the account is deleted using Computer Management or the net command, some account information will still remain in the system, which can be used to analyze the account's related behavior.
If the user account was only deleted using the net command or user management program, the user's directory will still remain in the system, and some files in the directory will record certain specific behaviors of the user for tracking purposes. These files are:
(Taking C drive as the system installation drive and the malicious username as cracker as an example)
C: \Documents and Settings \cracker\Desktop
The user's desktop, which may contain some temporary or downloaded files
C: \Documents and Settings \cracker\Cookies
User's web access situation, cookie files may record some sensitive information
C: \Documents and Settings \cracker\Recent
Files or folders the user has recently accessed
C: \Documents and Settings \cracker\Local Settings\History
User's internet browsing history
C: \Documents and Settings\cracker\Local Settings\Temp
Some temporary files may be generated in this directory during program installation, extraction, etc.
C: \Documents and Settings\cracker\Local Settings\Temporary
Internet Files
Temporary files generated while browsing the internet, which not only store webpage content but may also store some downloaded files as temporary files.
If the user has enabled security log auditing, if the account is deleted, the operations related to that account will leave a string of account SID values in the audit log.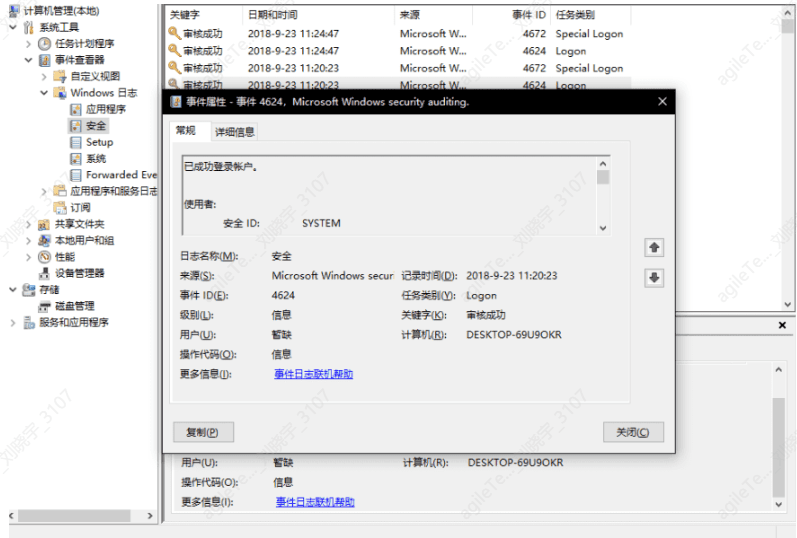
Windows Log Analysis#
Windows log files are divided into three main sections:
Application logs
Security logs
System logs
Setup logs (added after Server 2003)
These logs were stored in the %systemroot%\system32\config directory in evt file format before Server 2003 (where %SystemRoot% is a system environment variable, defaulting to C: \WINDOWS). However, after Server 2003, the storage location is in
%systemroot%\System32\winevt\Logs directory
Click "Start → Settings → Control Panel → Administrative Tools → Event Viewer" to list the types of logs contained in the local machine in the left pane of the Event Viewer window, such as Application, Security, System, etc.
Precautions:
The three core log files built into the system
(System, Security, and Application) have a default size of 2048KB (20MB). When the recorded event data exceeds 20MB, the system will prioritize overwriting expired log records.
Other application and service logs have a default maximum size of 1024KB, and exceeding this maximum limit will also prioritize overwriting expired log records.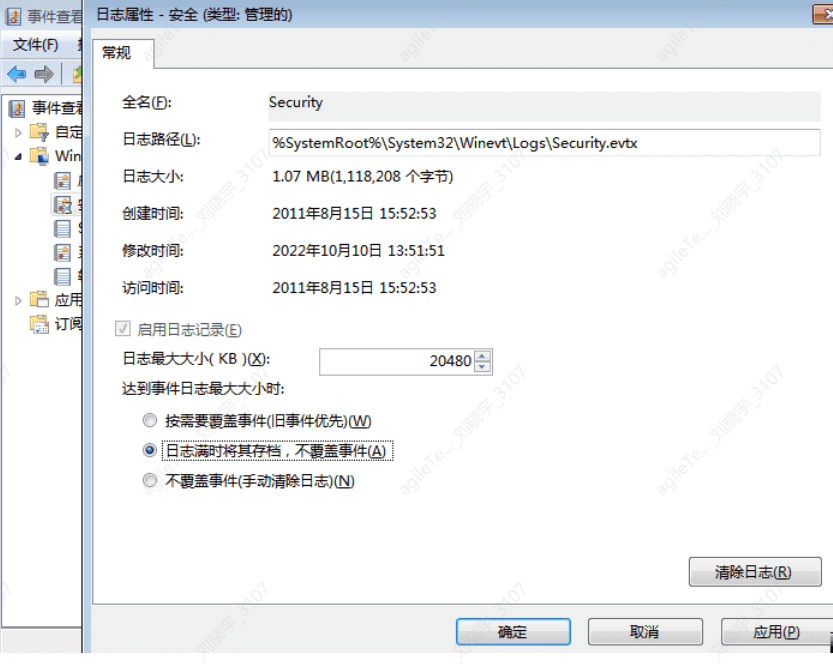
There are five types of events in Windows event logs, and all events must have one of these five types, and only one can exist. The five types of events are:
1. Information
Information events refer to successful operations of applications, drivers, or services.
2. Warning
Warning events refer to issues that are not direct or primary but may lead to future problems. For example, when disk space is low or a printer is not found, a "warning" event will be recorded.
3. Error
Error events refer to important issues that users should be aware of. Error events usually indicate loss of functionality and data. For example, if a service fails to load as the system boots, it will generate an error event.
4. Success Audit
Successful audit of security access attempts, mainly referring to security logs, which record events such as user logins/logouts, object access, privilege usage, account management, policy changes, detailed tracking, directory service access, account logins, etc. For example, all successful logins to the system will be recorded as "success audit" events.
5. Failure Audit
Failed audit of security login attempts, for example, if a user fails to access a network drive, that attempt will be recorded as a failure audit event.
Application Logs#
Application logs contain events related to application software installed by the operating system. Events include errors, warnings, and any information that applications need to report. Application developers can decide which information to log. Developers can then use these logs to determine which programs are running incorrectly and the nature of the errors: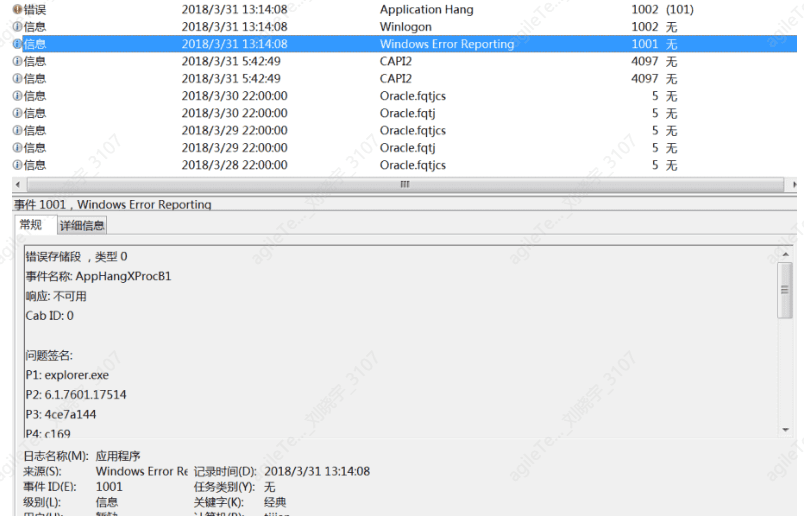
For example, when using an MSI package to install software, if there is an MSI error, it will trigger the application log of MsiInstaller: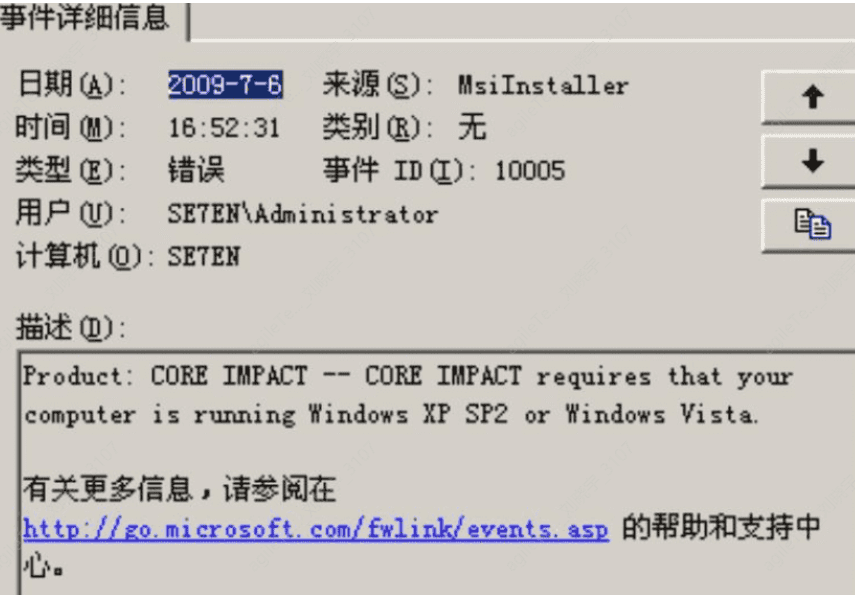
Security Logs#
Security logs contain events related to security, such as changes in user permissions, logins and logouts, file and folder access, printing, and other information. The following image shows a corresponding table of related events.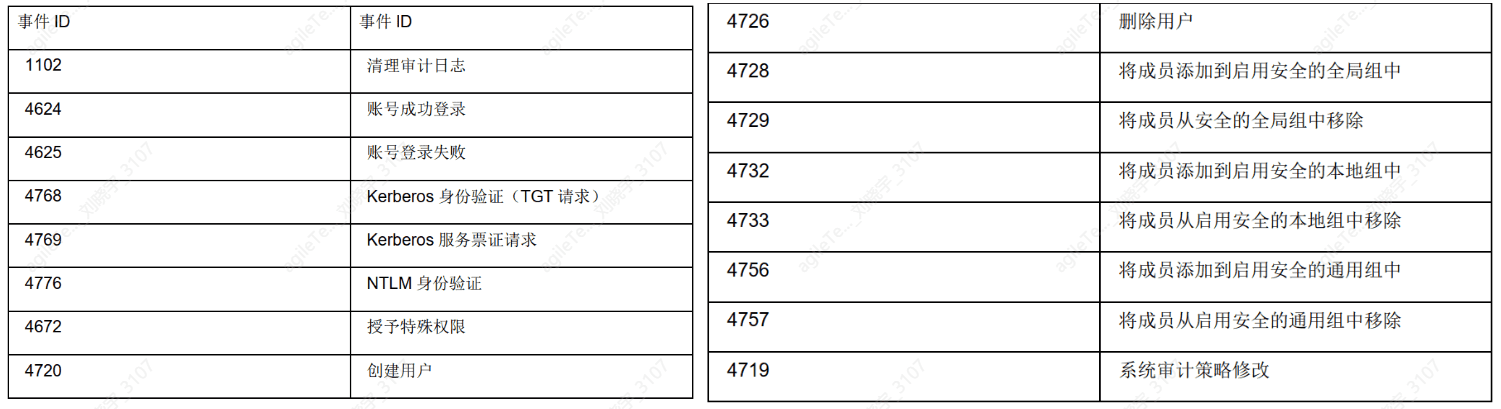
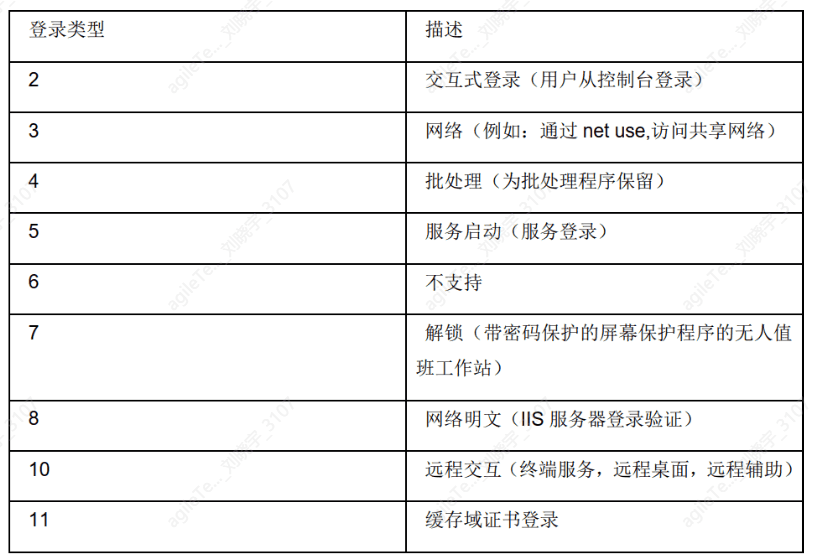
From the logs, detailed login information can be seen: login time, user, source network address, etc. If there is a large number of login failures, and the login type is 3, it may indicate that a user is attempting to crack passwords remotely, and caution should be exercised.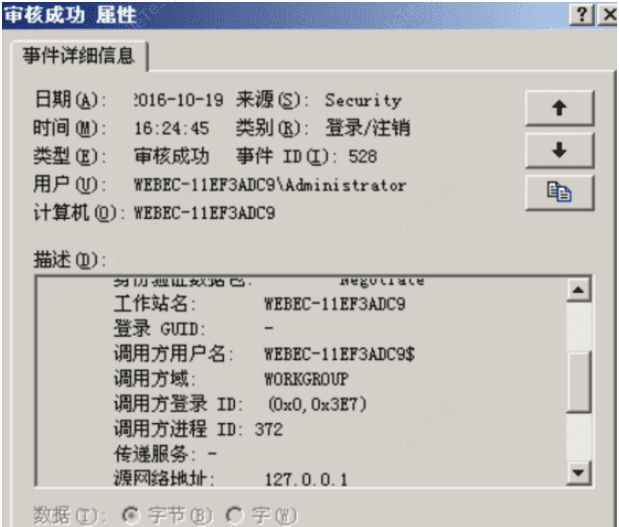
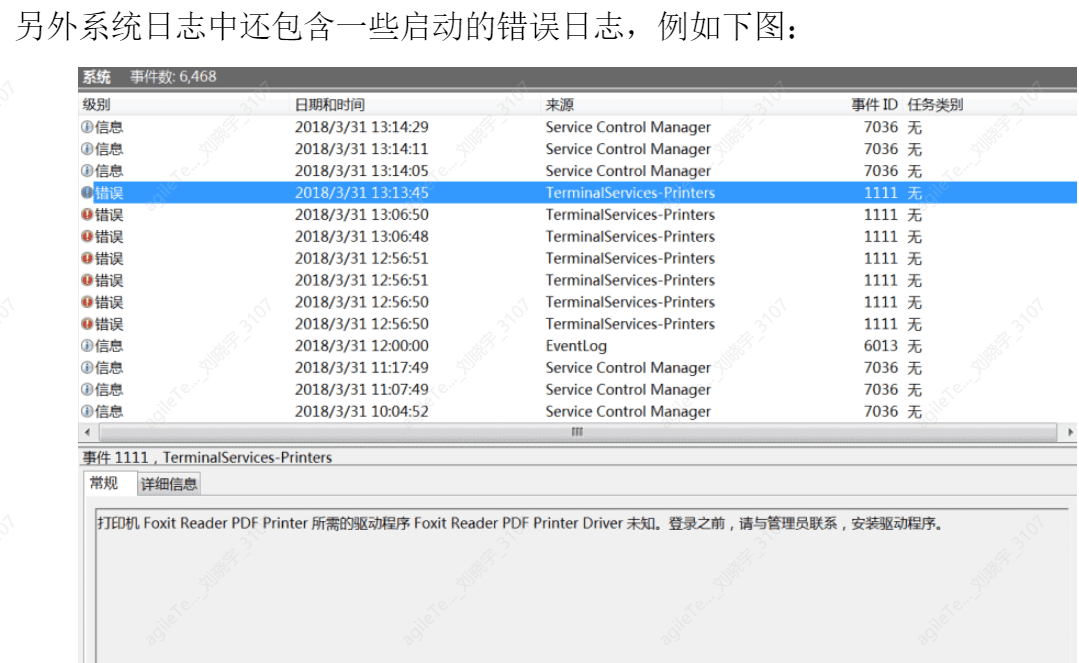
Additionally, by default, Windows does not have extra system startup logs or related recording programs, so some services must be relied upon to determine the system's status, among which the event log service is the best reference marker. The startup and shutdown of the event log service indicate the startup and shutdown of the Windows system. The system log contains system processes, device disk activity, etc. Events record behaviors such as device drivers failing to start or stop, hardware failures, duplicate IP addresses, and the starting, stopping, and pausing of system processes.
If a large number of IP address conflict logs suddenly appear in the system, it may indicate the presence of ARP spoofing attacks.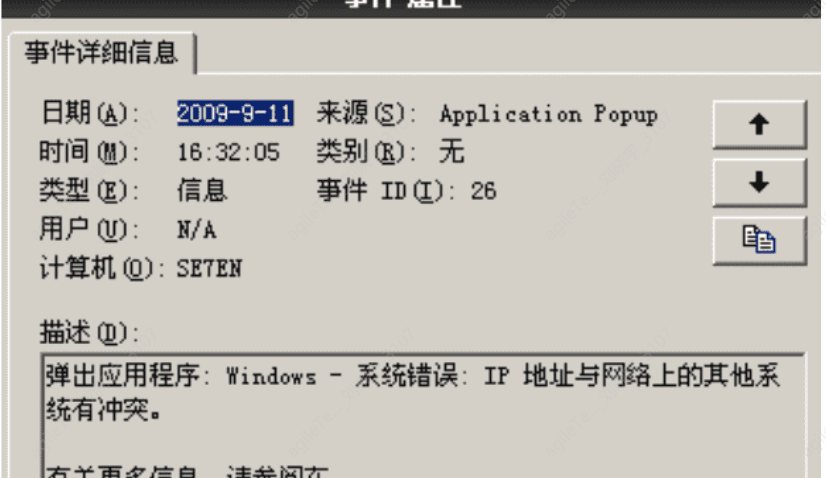
System Logs#
Setup Logs#
These logs record some patch installation logs. Some malicious users may use Windows Update to install patches after exploiting vulnerabilities to prevent other users from intruding. Thus, relevant logs will remain in the system: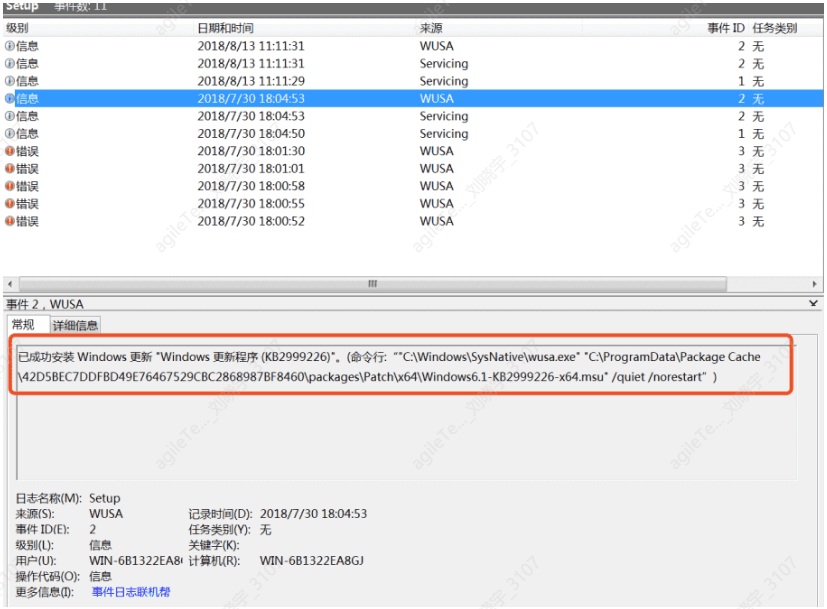
Common Tools#
Huorong Sword#
Huorong Sword is quite useful, and many of the key points mentioned in previous content are covered by this tool. Here are some simple functions:
1. System process monitoring
2. Startup items
3. Network monitoring
PcHunter#
PCHunter is similar to Huorong Sword, but the UI is significantly inferior:
This tool features marking suspicious items in red, and it has good support for kernel hooks and application layer hooks, each having its strengths.
PowerTool#
Some viruses may check for Huorong Sword and PC Hunter, so here I recommend a PowerTool, which checks from the kernel level and has similar functions to Huorong Sword and PC Hunter.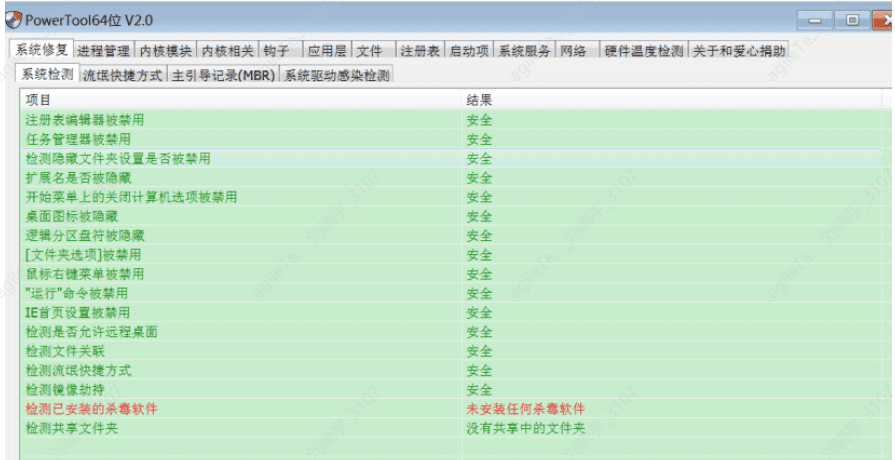
Virus Analysis#
PCHunter: http://www.xuetr.com
Huorong Sword: https://www.huorong.cn
Process Explorer: https://docs.microsoft.com/zh-cn/sysinternals/downloads/process-explorer
Process Hacker: https://processhacker.sourceforge.io/downloads.php
Autoruns: https://docs.microsoft.com/en-us/sysinternals/downloadslautoruns(invalid link)
https://learn.microsoft.com/en-us/sysinternals/downloads/autoruns
OTL: https://www.bleepingcomputer.com/download/otl/ (invalid link)
Kaspersky: http://devbuilds.kaspersky-labs.com/devbuilds/KVRT/latest/fullKVRT.exe
(Recommended: portable version, latest virus database)
Dr.Web CureIt: http://free.drweb.ru/download+cureit+free
(Recommended: fast scanning, can only be used for one week after one download, updates virus database)
Huorong Security Software: https://www.huorong.cn
360 Antivirus: http://sd.360.cn/download_center.html
Virus Dynamics#
CVERC - National Computer Virus Emergency Response Center: http://www.cverc.org.cn
Weibu Online Threat Intelligence Community: https://x.threatbook.cn
Huorong Security Forum: http://bbs.huorong.cn/forum-59-1.html
Aidu Ba Community: http://bbs.duba.net
Webshell Detection#
D Shield Web Detection: http://www.d99net.net/index.asp
Hippo Webshell Detection: http://www.shellpub.com
Sangfor Webshell Backdoor Detection Tool: http://edr.sangfor.com.cn/backdoor_detection.html
Safe3: http://www.uusec.com/webshell.zip (invalid link)
https://sourceforge.net/projects/safe3wvs/