User Classification#
Local Users
Domain Users
User Group: A group composed of multiple users that have the same permissions for a certain resource.
User Group Accounts
Description
Local User Groups#
Administrators——
Members of this group have full control over the server and can assign user permissions as needed.
Backup Operators——
Can back up and restore files on the server without regard to file permissions and cannot change security settings.
Guests——
Members of this group have a temporary profile created upon login, which is deleted upon logout.
Event Log Readers——
Can read the event logs from the local computer.
Power Users——
Members of this group can create, modify, and delete accounts. They can create local groups and add or remove users from the local user groups they have created, as well as add or remove users in the power users, users, and guests groups. They can create shared resources and manage the shared resources they create, but cannot take ownership of files, back up and restore directories, load or unload device drivers, or manage security and logs.
Members of this group can perform common tasks such as running applications, using local and network printers, and locking the server. Users cannot share directories or create local printers. By default, domain users and authenticated users are members of this group, so any user account created in the domain becomes a member of this group.
Remote Desktop Users——
Can log in to the server remotely.
Common System Commands#
net user——Displays the currently existing users.
dir View files in the current directory.
cd Switch directories.
net user testaa /add Add a user to the user group.
net user username View detailed information about a user.
net localgroup administrators testadd /add Add a user to the administrators group.
net user testaa /del Delete a user.
Points to Note#
Account empty passwords/weak passwords.
System Policies#
User Security Policy/Local Security Policy
secpol.msc
Group Security Policy
gpedit.msc
Such as account lockout policies, password policies.
Audit Policies
Audit policies are part of the Windows local security policy. When a user performs an action, the audit log records each event. By configuring audit policies, the system can automatically log all events of users logging into the local computer, allowing for quick determination of whether the system has been breached or is being attempted to be breached.
Policy Activation Recommendations#
- Audit login events
- Audit object access
- Audit process tracking
- Audit directory access
- Privilege use
- System events
- Account login events
- Account management
Points to Note#
To avoid confusion in permission management, user rights should be assigned to groups, and users needing these permissions should be added to those groups.
Open the "Local Security Policy" window in "Start" "Administrative Tools" and double-click the user permissions to assign to the group.
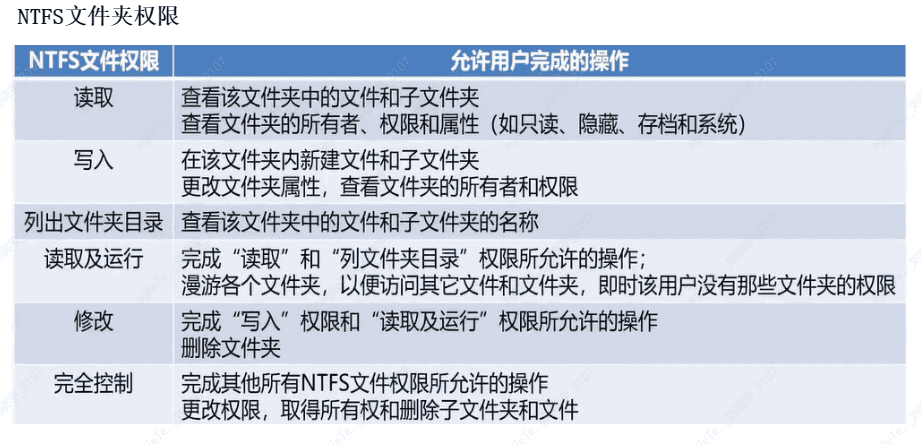
NTFS Permissions#
NTFS is the most widely used file system on computers, characterized by high security and ease of unified management of file security, allowing administrators to configure detailed access control permissions for files.
Permissions refer to the access rules associated with file or folder objects on the computer, used to determine whether a user can access the object and what operations can be performed. Using the NTFS file system, users can achieve authorized access to files or folders, ensuring the security of stored data.
By default, only authorized users can access.
Permission Accumulation#
The final permissions a user has on a file are the sum of all NTFS permissions specified by the user and all NTFS permissions specified by the user's group.
For example, if a user account belongs to group B and the user has read permissions on folder C, while group B has write permissions on folder C, the effective permissions for user A on folder C would be "read + write."
File permissions take precedence over folder permissions.
As long as a user has permission for a file, they can access that file even if they do not have permission to access the folder containing the file.
For example, if folder C contains files Files1 and Files2, and folder C's permissions allow user A to write, but File2's NTFS permissions only allow user A to read, then user A's effective permissions would be write permissions on folder C (including File1) and read permissions on File2.
Deny permissions take precedence over other permissions.
Among all NTFS permissions in Windows, deny permissions take precedence over any other permissions. Even if a user has access to a file or folder as a member of a group, once that user is set with deny access permissions, any other permissions that user may have will be revoked. In practice, deny permissions should be avoided as much as possible, as allowing users and groups to have certain access is easier than setting deny permissions.
Permission inheritance
Files and subfolders inherit permissions from their parent folder, meaning any permissions specified by the administrator for the parent folder also apply to the subfolders and files contained within that parent folder. For example, when permission inheritance is allowed, access permissions set for Folder1 will automatically be passed to File1, Folder2, and File2. Subfolder Folder2 and file File2 will automatically inherit the access permissions set for parent folder Folder1.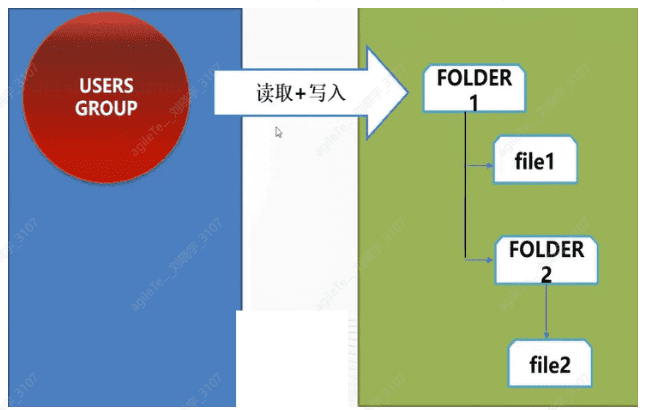
NTFS Permissions Related#
Effects of copying and moving on folder permissions
When copying or moving files and folders within and between NTFS partitions, the Windows system treats them as new files or folders, thus affecting the NTFS permissions of the source files or folders. When copying files and folders, one must have read permissions on the source folder and "write" permissions on the target folder. When moving files or folders, one must have "write" permissions on the target folder and "modify" permissions on the source folder.
When copying files or folders from one folder to another or from one disk partition to another, the copying of files or folders will have the following effects on NTFS permissions:
· When copying folders or files within a single NTFS partition, the copied folder or file will inherit the permissions of the destination folder. · When copying folders or files between NTFS partitions, the copied folder or file will inherit the permissions of the destination folder. · When copying files or folders to a non-NTFS partition (such as FAT32 or FAT), since non-NTFS partitions do not support NTFS permissions, these folders or files will lose their NTFS permissions.
The effects of moving on NTFS permissions are as follows:
When moving folders or files within a single NTFS partition, the folder or file retains its original permissions.
When moving folders or files between NTFS partitions, the folder or file will inherit the permissions of the destination folder. When moving folders or files between NTFS partitions, it is essentially copying the folder or file to a new location and then deleting it from its original location.
When moving files or folders to a non-NTFS partition, since non-NTFS partitions do not support NTFS permissions, these folders or files will lose their NTFS permissions.
File permissions auditing
The auditing feature can track detailed operations by users on specified objects and generate event logs for administrators to review, providing a method to view security events in the logs. This is very necessary for monitoring illegal user intrusions and attempts that threaten the security of system data.
Generally, the most common types of events that should be audited include:
Access to objects, such as files and folders
User and group account administration
User logins and logouts from the system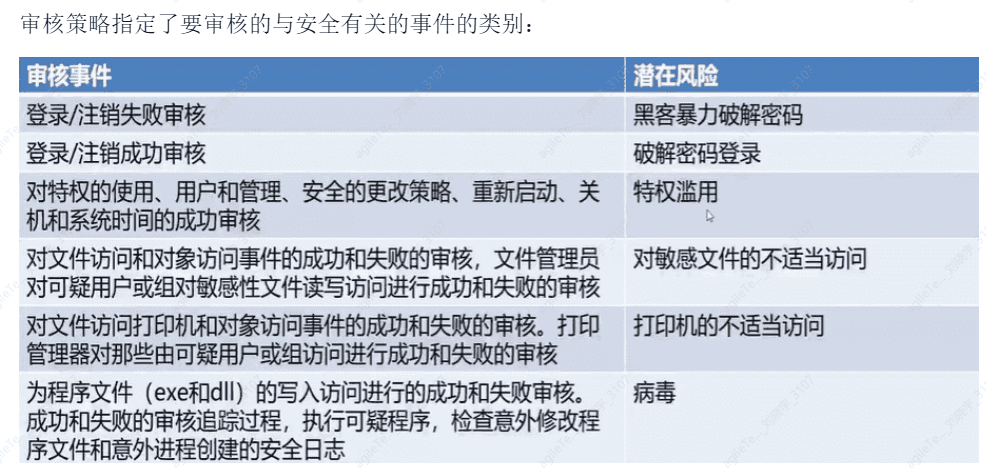

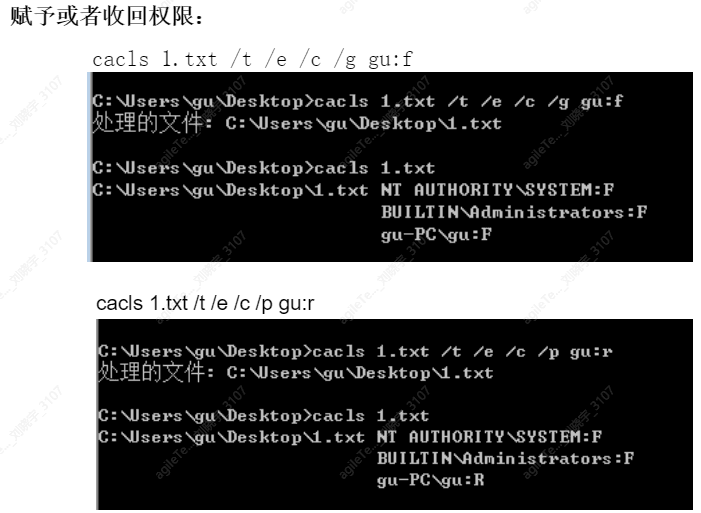
Using the cacls command to change file or folder permissions
1. View directory and ACL
cacls folder
2. Modify directory and ACL
Full control cacls test /t/e/c/g user : f
Read-only permissions cacls test/t/e/c/p user
Revoke permissions cacls test/t/e/c/r user: f
Deny user access cacls test/t/e/c/d user : f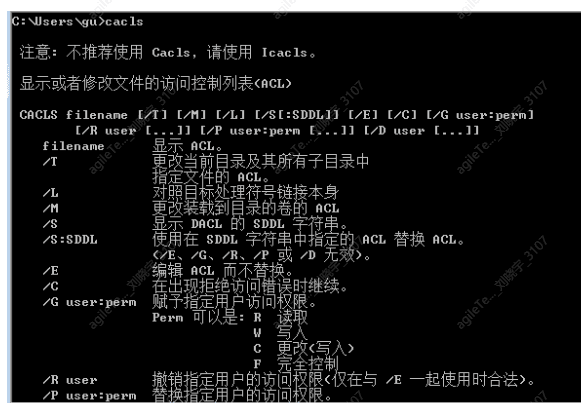
Windows Log Classification#
- Windows System Logs (including application, security, installer, system, and forwarded events)
- Server Role Logs
- Application Logs
- Service Logs
Basic information of event logs
Logs mainly record the current date, time, user, computer, information source, event, type, category, and other information.
Security Logs#
Through the log auditing feature, hacker infiltration and attacks can be quickly detected, preventing illegal users from intruding again. This is mainly done through the following event policy audits:
1. Audit of policies
2. Audit of successful or failed logins
3. Audit of object access
4. Audit of process tracking
5. Audit of account management
6. Audit of privilege use
7. Audit of directory service access
To access these logs, we need to search for "Computer Management" in the start menu and open it, or right-click on My Computer → Manage → System Tools.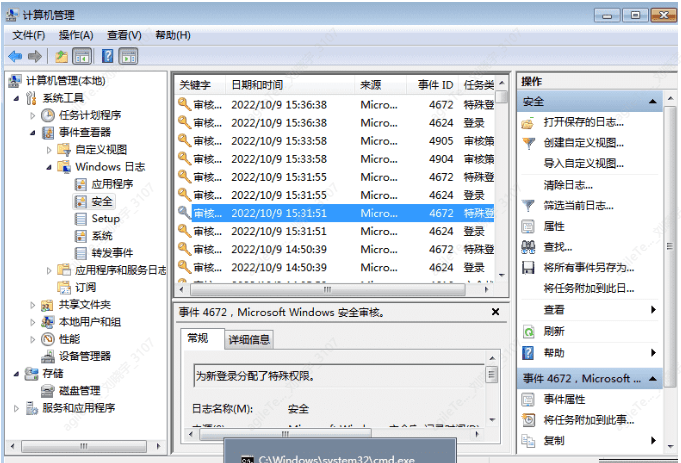
Security Protection#
Starting and stopping the firewall
Can be found in the control panel, operated through a graphical interface.
Command:
Start and stop the firewall
The firewall can also be started or stopped via command line commands.
Start the firewall
netsh advfirewall set allprofiles state on
Stop the firewall
netsh advfirewall set allprofiles state off
Start Windows Security Center.