System Commands#
Superuser
UID=0, Username=root; can manage all resources within the system
System User
Cannot be used for login, UID=1~999; for example, the http process in the system runs using the user apache
Regular User
UID=1000~65535, can use most resources, some special permissions will be controlled, users only have write permissions for their own directories.
sudo command: Regular users temporarily borrow root permissions to execute commands, need to enter password verification, and all operations are recorded
/etc/password——User account file
Username: Password: User ID: Primary Group ID: Full Name: Home Directory: Login Shell
/etc/shadow——User password file
Password: Last password change time: Minimum days between two password changes: Maximum days: Days in advance to warn about password expiration: Days after expiration to disable user: Expiration time: Reserved fields
/etc/group——User group file
Group name: Password: Group ID and user list
/etc/gshadow saves the passwords of all groups in the system
/etc/skel Every time a new account is created, the system automatically copies all content (including directories and files) from the /etc/skel directory to the new user's home directory "/home/"
User Management#
useradd test Create user test
passwd test Change password for user test

User Group Management#

User Account Management#
- Check
#cat /etc/passwd #cat /etc/shadow
#awk -F: '$3==0 {print $1}' /etc/passwd Query users with UID=0
2. Remove excess accounts
#userdel -r username
3. Lock account
#passwd -l username #passwd -u username (unlock account)
User Password Management#
Check if the user has an empty password in /etc/shadow: Password field is an exclamation mark
#awk -F:'length($2)==0 {print $1}' /etc/shadow
#awk -F ":"'($2==""){print $1}' /etc/shadow
Prevent Weak Passwords#
Modify file:
vi /etc/pam.d/system-auth
Password lifespan:
vi /etc/login.defs
Disable Root Remote Login#

Disable su to root#

User Management Summary#

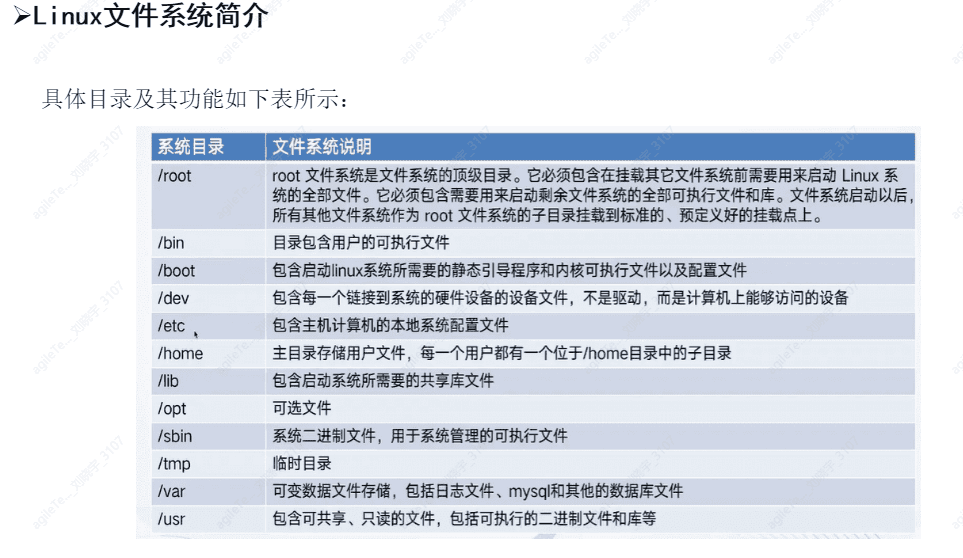
Introduction to the Linux File System#
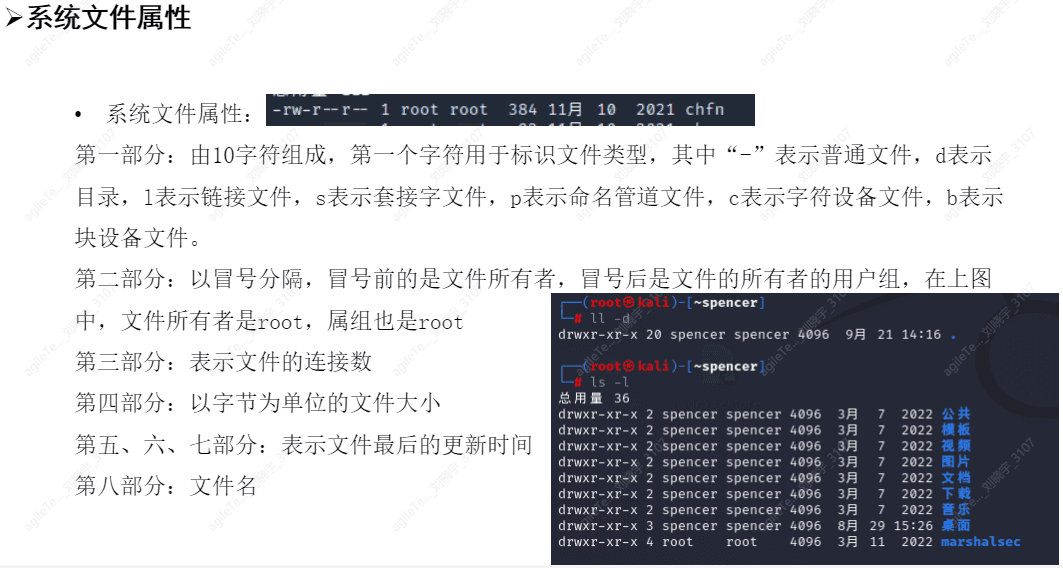
File System Attributes#
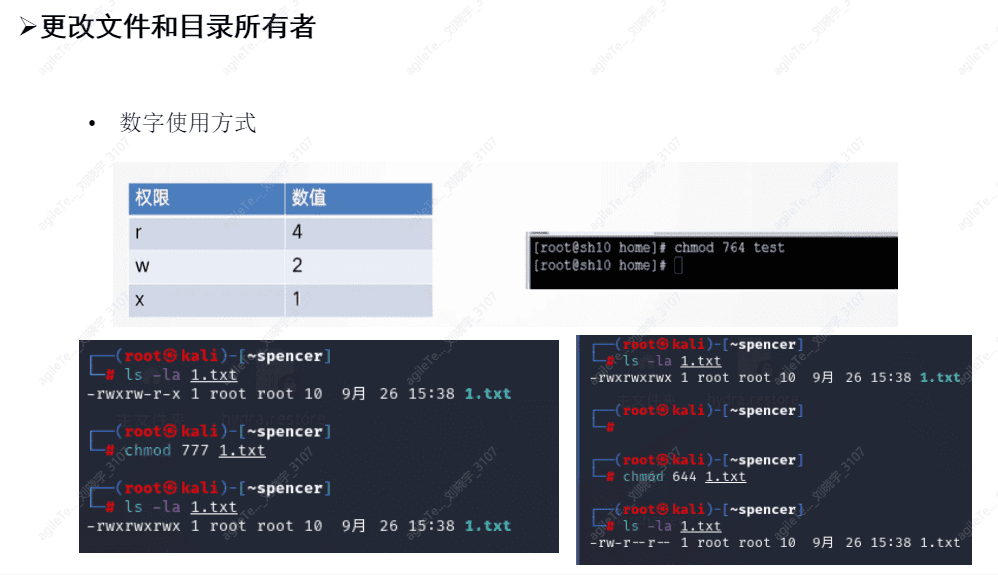
Change file and directory ownership
chown
#chown -R root: users /test
Change file access permissions
chmod
Two methods: 1. Character method: u, g, o 2. Numeric method: 4/2/1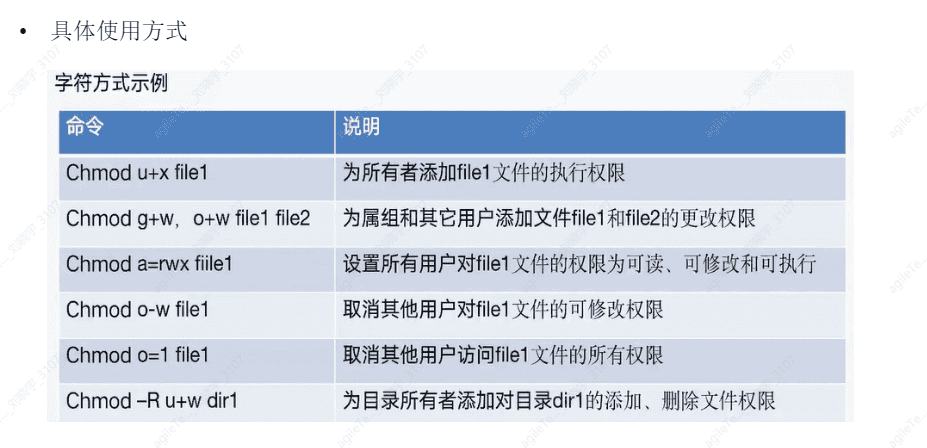
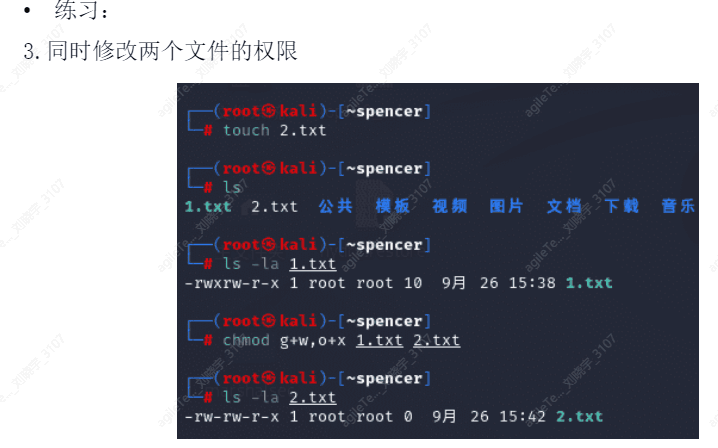
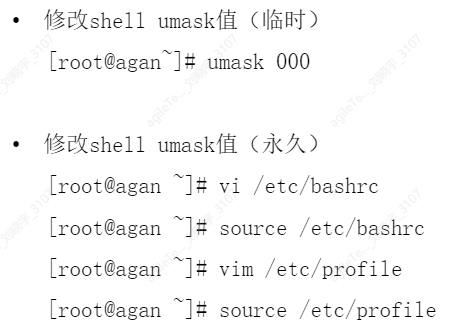
Permission Management#

Log Security#
Log Classification#
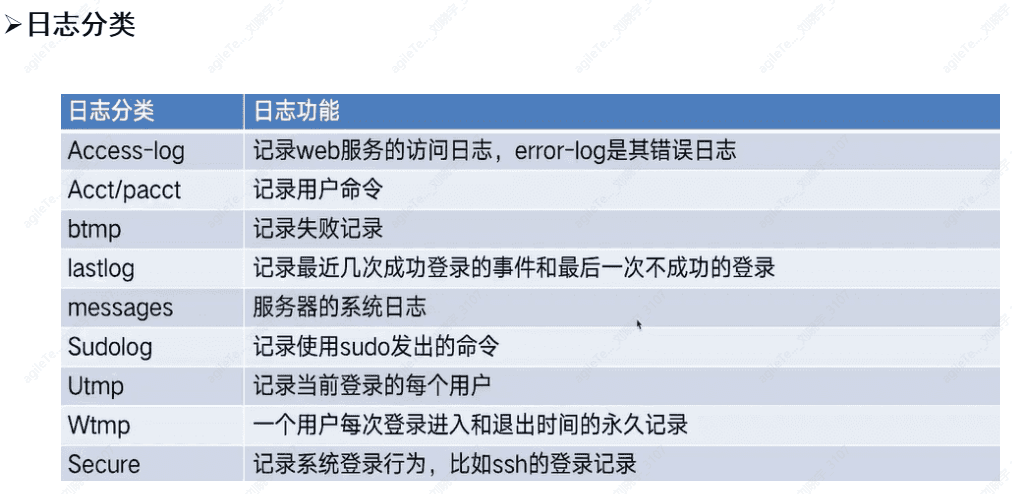



/var/log/messages Server system log
/var/log/secure Records system login behavior
var/log/wtmp, /var/log/lastlog Records system login and logout information